
Next up at #enigma2021, Sunny Consolvo will be speaking about "SECURITY & U.S. POLITICAL CAMPAIGNS: A STUDY & EXPERT ROUNDTABLE"
usenix.org/conference/eni…
usenix.org/conference/eni…
What if your personal account getting hacked could lead to years of harassment, allow election interference, and subvert democracy?
What if to avoid this you have to fundamentally change your online habits? And you work in politics, not tech.
What if to avoid this you have to fundamentally change your online habits? And you work in politics, not tech.
Not all hacks will lead to outsized outcomes like that, but some will! And it's especially hard in a fast-paced temporary environment of a political campaign.
How are campaigns different than the general population?
* Totally transient
* Almost everyone gets hired in the 3 months before the election
* Ticking clock
* Low security incentives
* Totally transient
* Almost everyone gets hired in the 3 months before the election
* Ticking clock
* Low security incentives
Risks:
* Highly motivated attackers, including nation-states
* Impacts of an attack can be outsized, like impact on democracy
* Highly motivated attackers, including nation-states
* Impacts of an attack can be outsized, like impact on democracy
Culture:
* short-lived
* little money, especially early on and it's harder to change things later
* chaotically busy
* amorphous boundaries: staff, consultants, volunteers
* when does the campaign really begin? there's a lot of communication before it "really" starts
* short-lived
* little money, especially early on and it's harder to change things later
* chaotically busy
* amorphous boundaries: staff, consultants, volunteers
* when does the campaign really begin? there's a lot of communication before it "really" starts
All of that's pretty well-known, but in order to improve the state of their security, we had to understand better. Performed a qualitative UX study and then brought together an expert roundtable.
First let's look at account use. Every one is different, but some common bits:
* use many different systems (e.g. Gsuite, Twitter, Zoom) including personal accounts
* use many different systems (e.g. Gsuite, Twitter, Zoom) including personal accounts
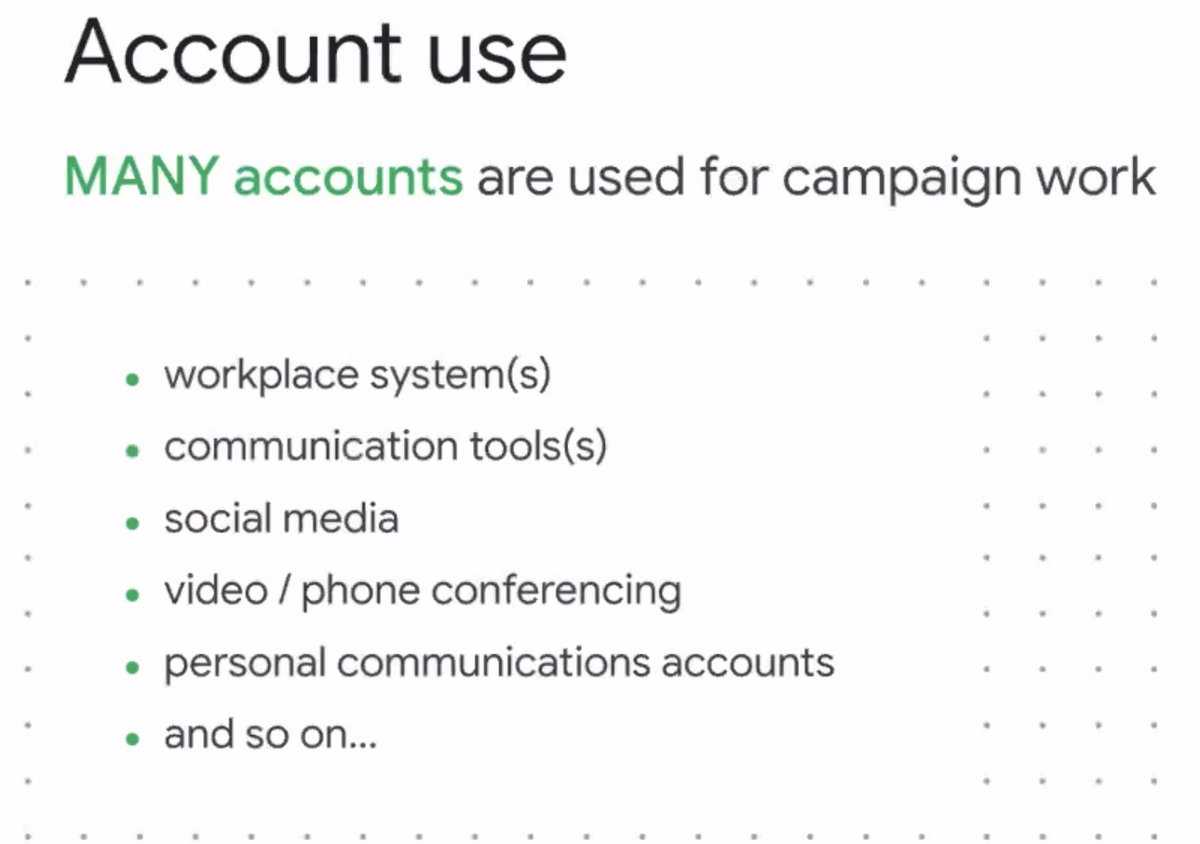
* many accounts are owned/shared by many people
-- social media accounts
-- accounts using for hiring
* some accounts are made by the campaign, some were personal accounts made during or before, some will keep being used after
-- social media accounts
-- accounts using for hiring
* some accounts are made by the campaign, some were personal accounts made during or before, some will keep being used after
* It's unusual for campaigns to have IT staff. Even when they do, they can't protect the personal accounts.
* The individual is the *only* one who has access to all of their accounts. That means they need to do the security for them: understand, prioritize, actually do.
* The individual is the *only* one who has access to all of their accounts. That means they need to do the security for them: understand, prioritize, actually do.
* Account security is a somewhat recent concern.
* They are focused on winning the election. Is it worth it to spend time on that rather than hiring more staff or working on the myriad of other tasks?
* They are focused on winning the election. Is it worth it to spend time on that rather than hiring more staff or working on the myriad of other tasks?
What are account security practices actually like?
common 2-factor concerns:
* too much time and effort
* fear of being locked out of their accounts, including when they travel, phone battery runs out, etc. And there's usually no IT to help with tech support.
common 2-factor concerns:
* too much time and effort
* fear of being locked out of their accounts, including when they travel, phone battery runs out, etc. And there's usually no IT to help with tech support.
(But people were overestimating how often folks get locked out)
* 2FA doesn't work well on hyper-shared accounts, especially if the account was made on the last cycle
* 2FA doesn't work well on hyper-shared accounts, especially if the account was made on the last cycle
Different factors have different security against different types of attackers...
... but people don't understand this, leading to under-use of the most secure forms of 2FA
... but people don't understand this, leading to under-use of the most secure forms of 2FA
There were announcements that 2020 US election was the most secure yet. Is everything fixed? Heck no!
There are other elections around the world and we did see attacks.
There are other elections around the world and we did see attacks.
How can we the security community help?
* More research on practices and usability studies on security protections
* Very robust and usable security protections
* Standardization of offerings and experience
* Reducing (perceived) time and effort
* Default settings
* More research on practices and usability studies on security protections
* Very robust and usable security protections
* Standardization of offerings and experience
* Reducing (perceived) time and effort
* Default settings
[I'm going to give my hands a break and not livetweet the questions here. If you want to see the questions, please join us at #enigma2021 -- or hey, at Engima 2022!]
• • •
Missing some Tweet in this thread? You can try to
force a refresh












