Last day of #enigma2021 and we're kicking off with @cooperq from @EFF talking about "DETECTING FAKE 4G LTE BASE STATIONS IN REAL TIME"
usenix.org/conference/eni…
usenix.org/conference/eni…
What is a cell site simulator?
*transmitter or receiver which intercepts metadata from cell phones, often by pretending to be a legit cell tower
*transmitter or receiver which intercepts metadata from cell phones, often by pretending to be a legit cell tower

First started looking at these because of reports from the Standing Rock protests (people were seeing weird things with their cell phones, tried apps to detect e.g. Stingray) 

Packed a bag, headed out there, and tried to detect something.
Figured out had no idea what he was doing. The apps had a lot of false positives and didn't know what to do with the spectra.
Figured out had no idea what he was doing. The apps had a lot of false positives and didn't know what to do with the spectra.

But weird -- there was no 2G anywhere in the area. Why is this important?
Stingray pretends to be a base station, but pretends to be 2G, so it wasn't that. Also the apps (probably) don't work because they're trying to detect Stingray.
Stingray pretends to be a base station, but pretends to be 2G, so it wasn't that. Also the apps (probably) don't work because they're trying to detect Stingray.

How do the 4G versions work (e.g. Hailstorm)?
* it has to have vulns to work -- but we didn't know about any
* so @rival_elf went and dove in and found a bunch of them
* it has to have vulns to work -- but we didn't know about any
* so @rival_elf went and dove in and found a bunch of them

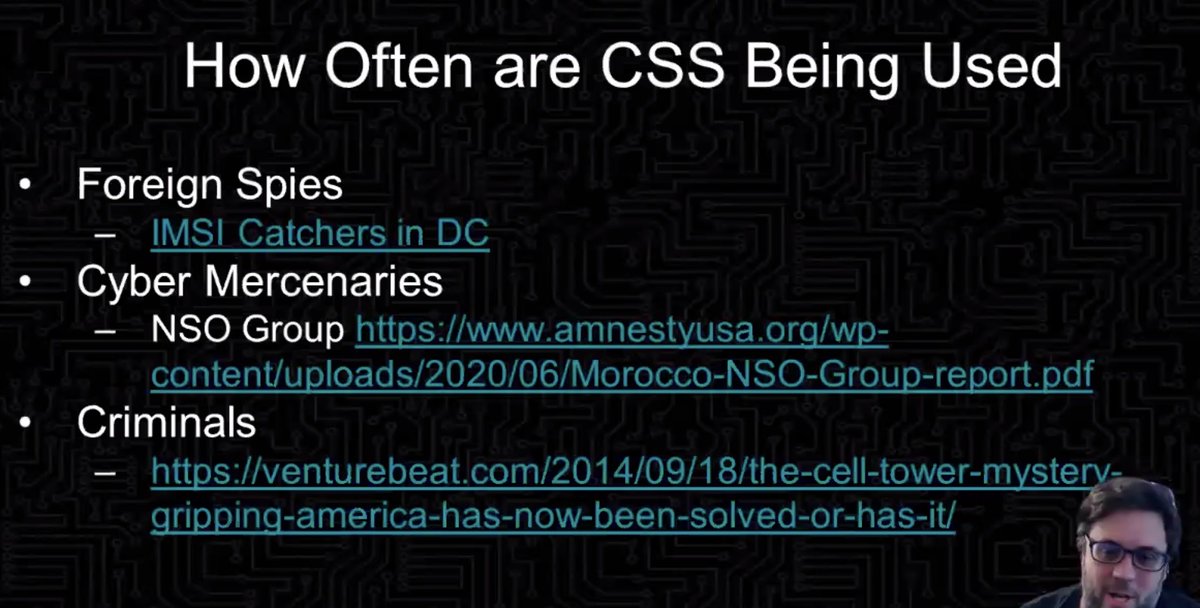
How often are these fake cell sites being used? To the FOIA!
* federal law enforcement: ICE/DHS 100s of times/year
* local law enforcement:
- Oakland 1-3 times/year
- Santa Barbara PD 231 times in 2017
Why the difference? Oakland has strong privacy laws
* federal law enforcement: ICE/DHS 100s of times/year
* local law enforcement:
- Oakland 1-3 times/year
- Santa Barbara PD 231 times in 2017
Why the difference? Oakland has strong privacy laws

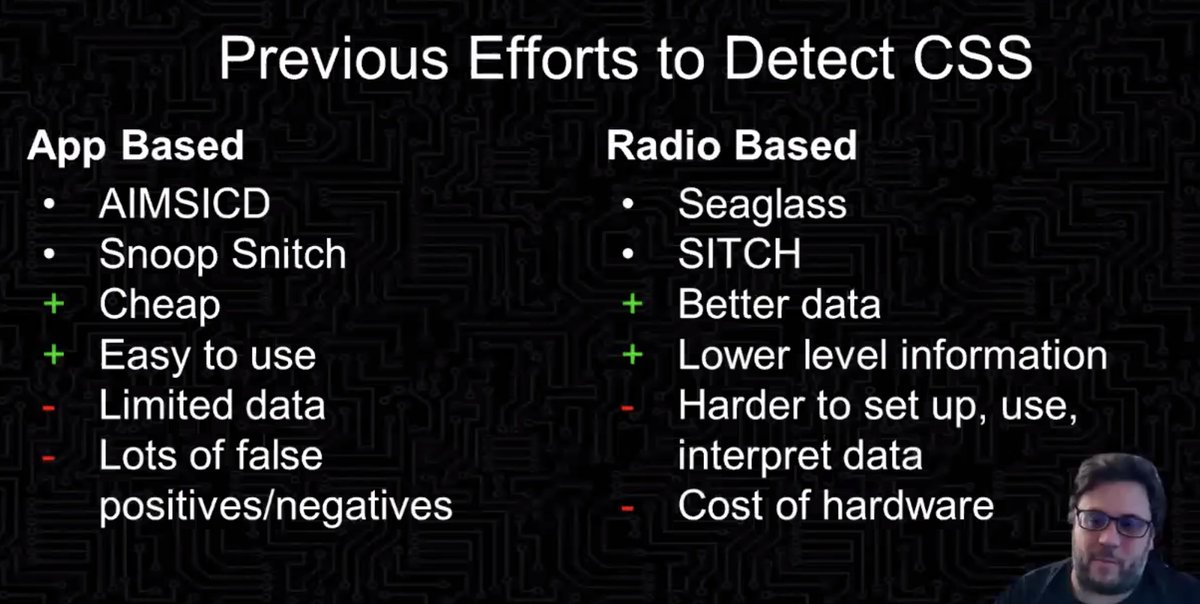
Previous efforts to detect:
* app based -- cheap and easy to use, but limited amount of data (only for towers the phone is connected to, what is visible through API)
* radio based -- expensive, harder to use, have to have programming/DB knowledge
* app based -- cheap and easy to use, but limited amount of data (only for towers the phone is connected to, what is visible through API)
* radio based -- expensive, harder to use, have to have programming/DB knowledge
Can we detect 4G cell-site simulators?
* how can we do better than previous efforts?
* how can we detect 4G rather than previous 2G?
* how can we verify the results?
* how can we do better than previous efforts?
* how can we detect 4G rather than previous 2G?
* how can we verify the results?

So made crocodile hunter to detect 4G cell site simulators
* relatively cheap and small (fits in backpack)
* open-source
* relatively cheap and small (fits in backpack)
* open-source

Each of these red dots are cell sites
... the skulls look suspicious (they're not all IMSI catchers)
... the skulls look suspicious (they're not all IMSI catchers)
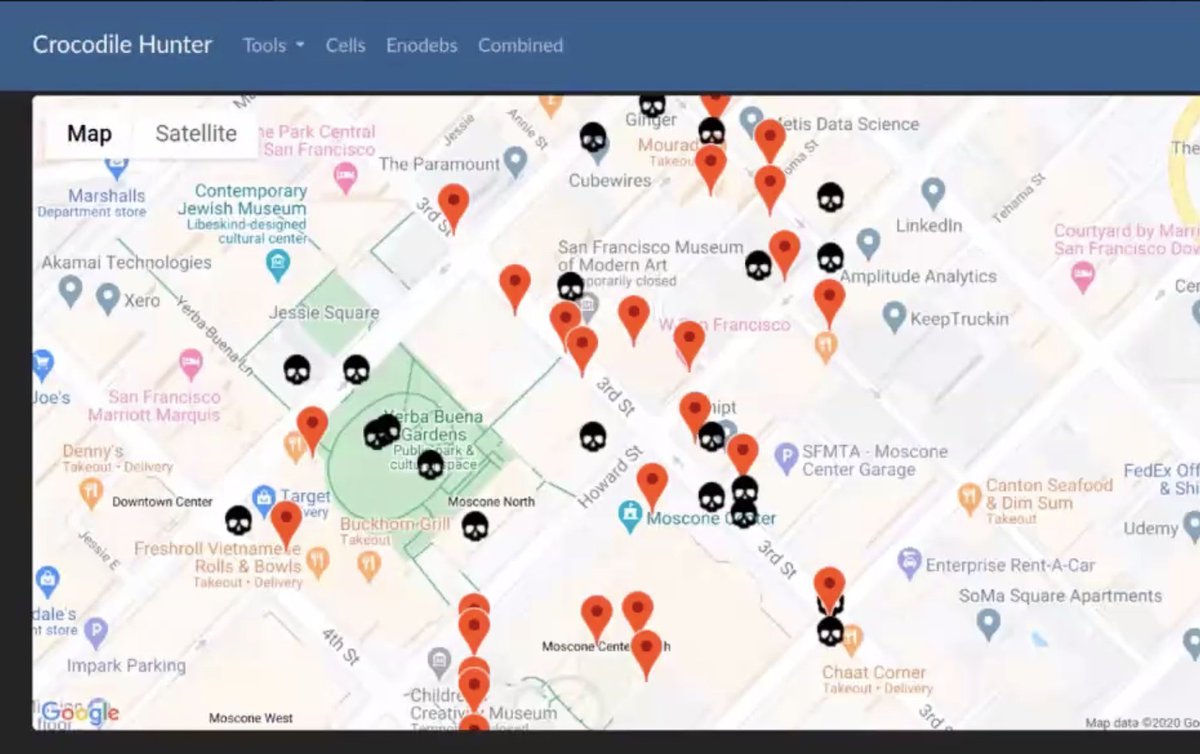
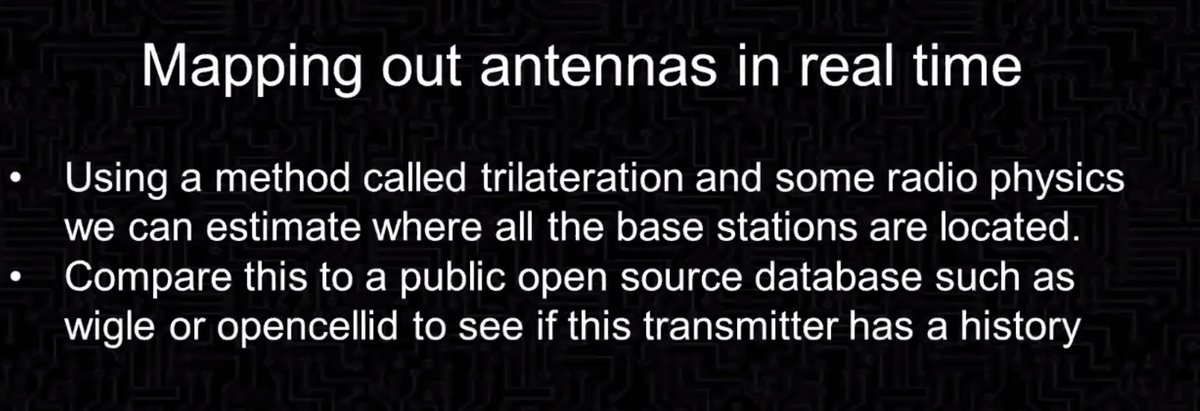
Mapping out where base stations are located in real time, so can track them down to figure out
* does it have a history or is it new?
* is it missing parameters?
* is it moving?
* etc

* does it have a history or is it new?
* is it missing parameters?
* is it moving?
* etc
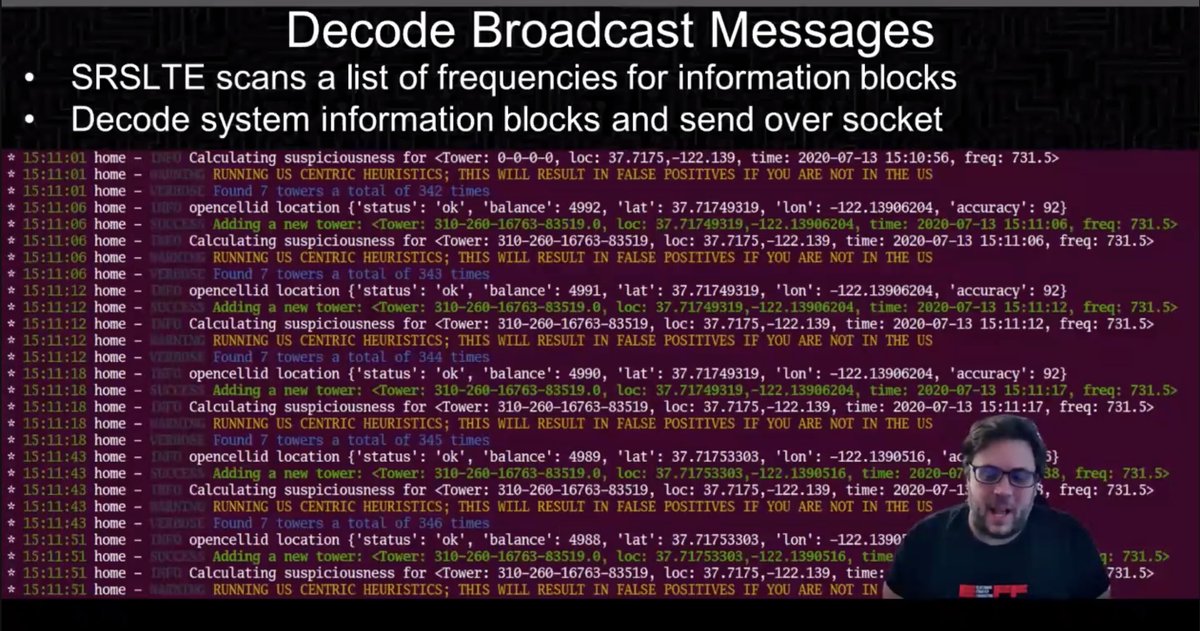
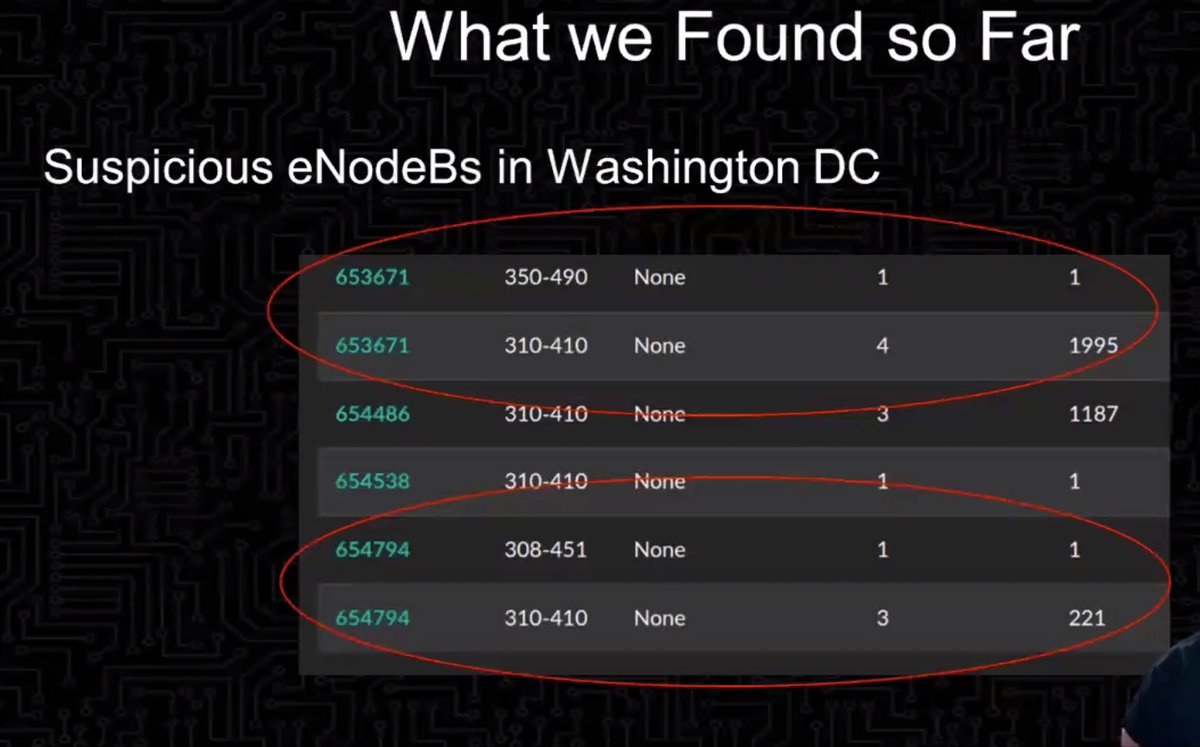
Found some suspicious things on first test in DC
* why the heck did this suddenly stop claiming it's a US cell phone and then start claiming it's not part of any country's network in the world?
* why is this other one claiming to be off the coast of Nova Scotia?
* why the heck did this suddenly stop claiming it's a US cell phone and then start claiming it's not part of any country's network in the world?
* why is this other one claiming to be off the coast of Nova Scotia?
Didn't track that one down, but then looked in Oakland during a march and found more suspicious signals (don't correspond to US country codes and network codes which don't match the country codes)
What the heck is this?
What the heck is this?
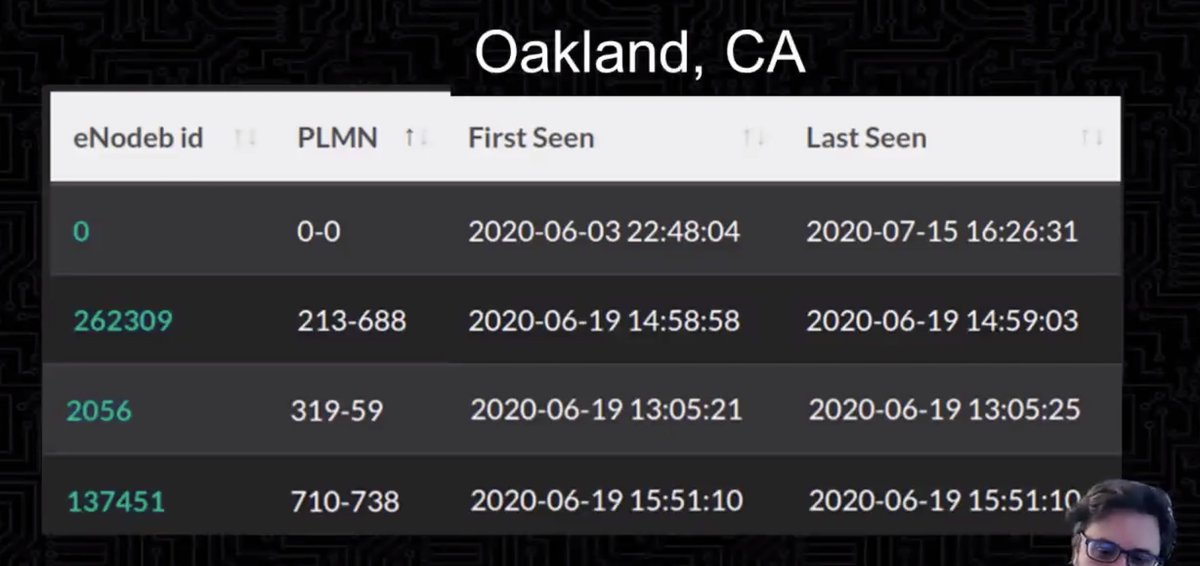
More research needed.
The name is after Steve Irwin (crocodile hunter), who was killed by a stingray.
The name is after Steve Irwin (crocodile hunter), who was killed by a stingray.

Key takeaways
* we have a pretty good understanding of the vulns used
* none of the previous IMSI catcher detector apps really do their job any more, but the same principles should work on the next gen
* the problems of CSS abuse can be solved but it's going to be a lot of work
* we have a pretty good understanding of the vulns used
* none of the previous IMSI catcher detector apps really do their job any more, but the same principles should work on the next gen
* the problems of CSS abuse can be solved but it's going to be a lot of work

[end of talk]
• • •
Missing some Tweet in this thread? You can try to
force a refresh