Here it is! It was an absolute pleasure to develop this course, #CyberChef for Security Analysts, with @chrissanders88. I've tried to cover a range of use cases for work in our field but I probably only scratched the surface. (1/5)
https://twitter.com/chrissanders88/status/1356618930438221833
What I've aimed to do instead is to teach the skills so that you can look at the data you'll be using in your work and be confident you can whip up a recipe in CyberChef to suit your needs (2/5).
What's covered are the fundamentals of CyberChef up to the more advanced features that make it the indispensable tool for network defenders. Totally unpaid tweet right here: 👇 (3/5)
https://twitter.com/williballenthin/status/1356436969195098113
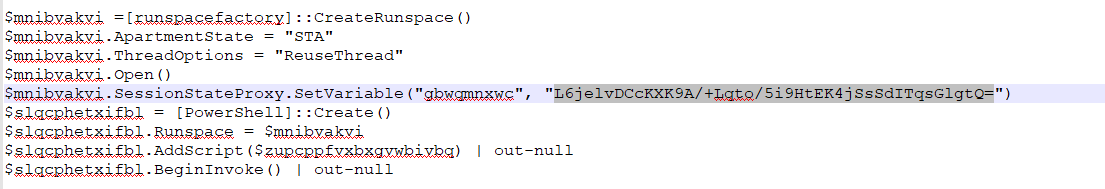
This is a demo heavy course with multiple labs and challenges. I've tried to minimise the dreaded PowerPoint, and all the example data is included so you can work alongside me in slicing, dicing, parsing, and de-obfuscating data. Then complete labs to test your knowledge. (4/5)👌
So please take a look at the syllabus at learncyberchef.com to learn more! Thanks! (fin)
• • •
Missing some Tweet in this thread? You can try to
force a refresh