
Let's walk through #malware de-obfuscation of a REvil PowerShell ransomware script in #CyberChef. The original can be found below if you want to play alone at home! hybrid-analysis.com/sample/e1e19d6…
Following my analysis, I realised there is an excellent write up of the same PowerShell on SANS here which is worth a read: isc.sans.edu/forums/diary/P… Thanks to @xme for saving me the detonation to learn its ransomware! 👍
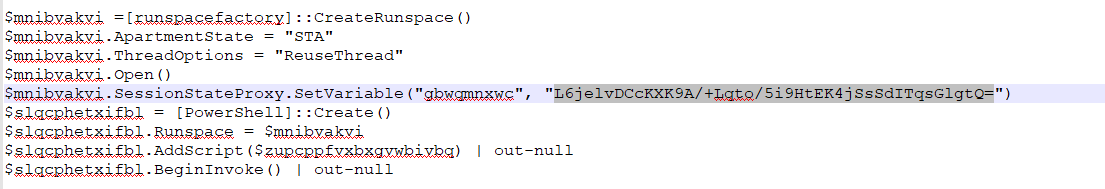
Taking a scan we can see an AES decrypt function and blob of Base64 - likely what is to be decrypted. Later on we see our IV and Key variables references, also in Base64. 




Step 1 in CyberChef is to use a Subsection to convert the Base64 to hex values so we can pass to the AES decrypt operation. (You can actually pass Base64/UTF-8 as well but its always nicer to work in hex! 😎) 





Next you can place the IV and Key into two Registers for later use. Essentially like variables (or memory registers which ever makes more sense to you), Registers are really handy for 'saving' data for later use to pass in CyberChef operations. Here they are saved as $R0 and $R1. 

Then we can pass the register values to the isolated blob of encrypted hex data. We isolate that through a regex. The decrypted blob (second screenshot) has another block of hex as variable $hex_str 



From there we can isolate that blob of hex via another regex, and convert to bytes using 'From hex' operation. Then hello we see our friend 'This program cannot be run in DOS mode. 

We can highlight the garbage code up until the MZ header. CyberChef will tell us how many bytes that is: 1925 



Need to 'drop bytes'? There's an operation for that! We can just cut the 1925 bytes away to leave us with our PE file. 

What's next? Hash and look it up? Save it off for more analysis? Here it is in the awesome PEStudio. 

So, why CyberChef?
1⃣Low barrier to entry, all the tools in the one interface.
2⃣ Immediate feedback! Go wrong? You can step back.
3⃣ Training! A senior member can walk through this de-obfuscation with junior team member so they can learn the 'why' and not just to run a script.
1⃣Low barrier to entry, all the tools in the one interface.
2⃣ Immediate feedback! Go wrong? You can step back.
3⃣ Training! A senior member can walk through this de-obfuscation with junior team member so they can learn the 'why' and not just to run a script.
Thanks for reading this long thread! If you want to learn the skills and gain the confidence to use these operations to de-obfuscate malware like this, join CyberChef for Security Analysts! learncyberchef.com
I'll put this recipe up on the Github repo and always welcome more to learn what others are doing with this amazing tool. github.com/mattnotmax/cyb…
• • •
Missing some Tweet in this thread? You can try to
force a refresh





