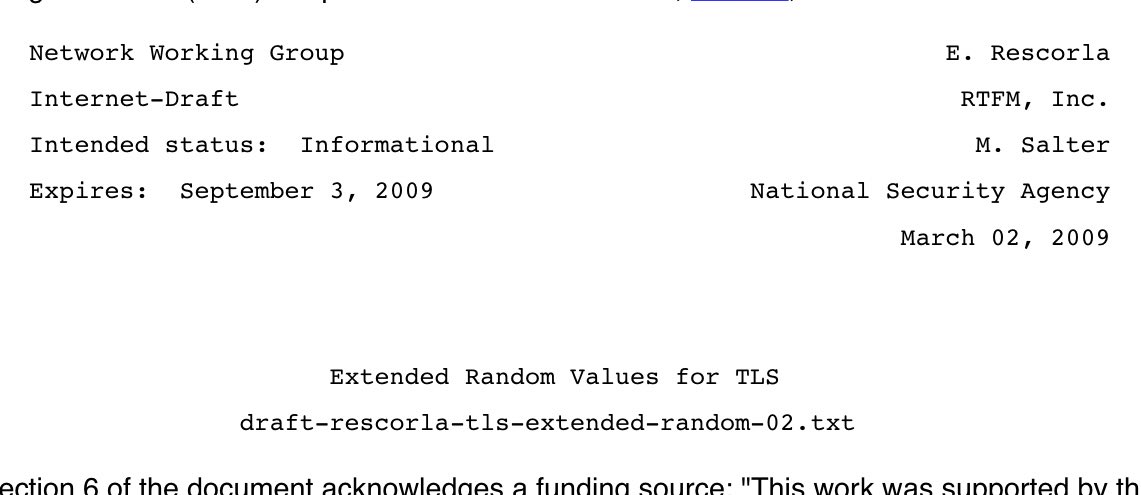
This is probably old enough that it doesn’t ring a lot of bells for people, so here: blog.cryptographyengineering.com/2017/12/19/the…
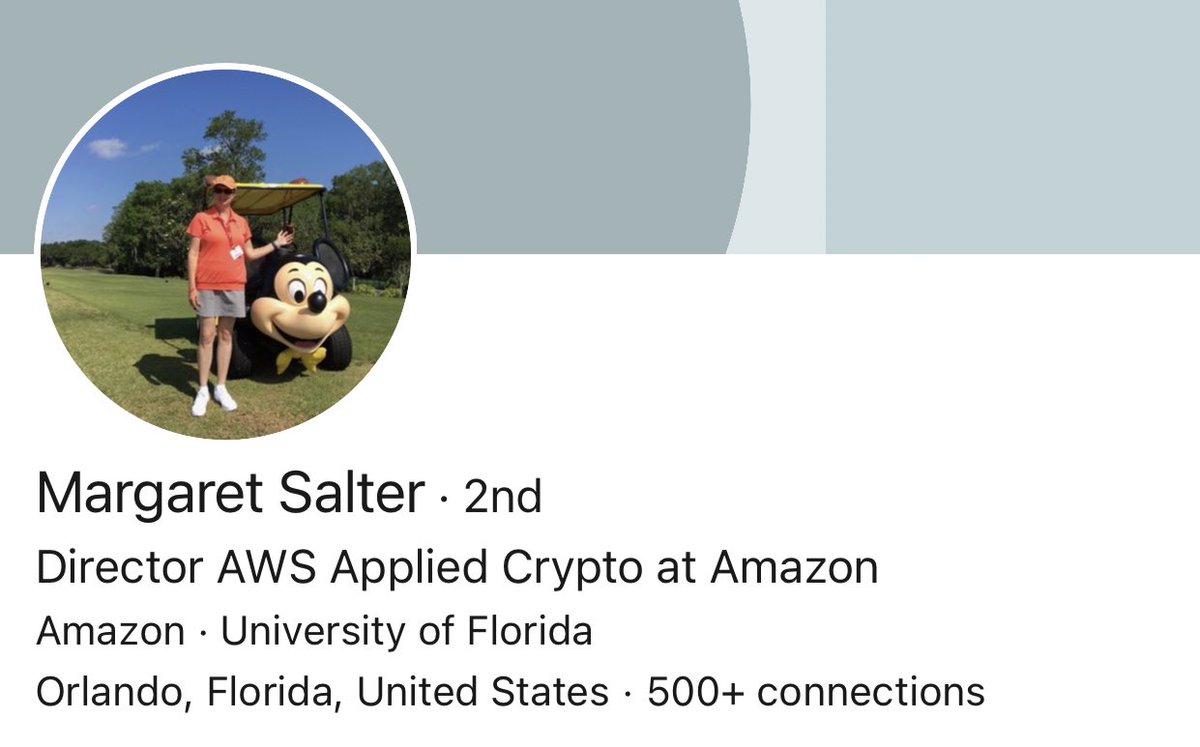
I was trying to be really low-key on this one, so let me make it really blunt. There is every reason to believe the NSA tried to subvert commercial cryptography in the 2000s, and now one of the architects of that work runs applied crypto at Amazon.
It’s funny how nonchalant we’ve gotten about all of this. A year after the Snowden leaks if you’d told me we’d be fine with having people involved with Dual EC running the crypto groups at major tech firms, my mouth would have dropped open. Now I’m worried I’m being too mean.
If my boss was involved in that work, nothing they later recommended would make it to production without a million reviews. I hope that’s happening at Amazon. I mean that in the nicest and least alarmist way possible.
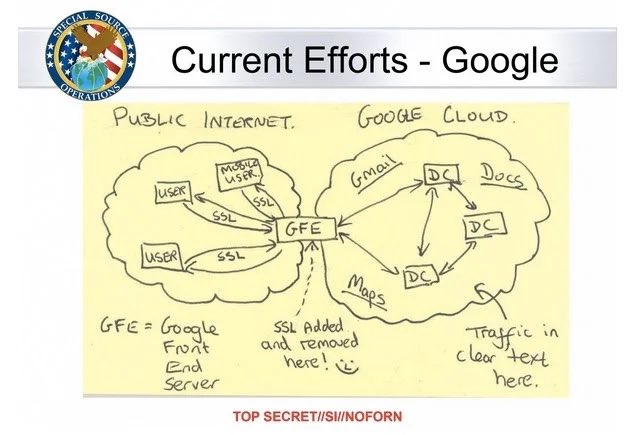
Also, remember this slide? Wasn’t Dual EC — but nice to know the tech companies have definitely learned their lesson. 
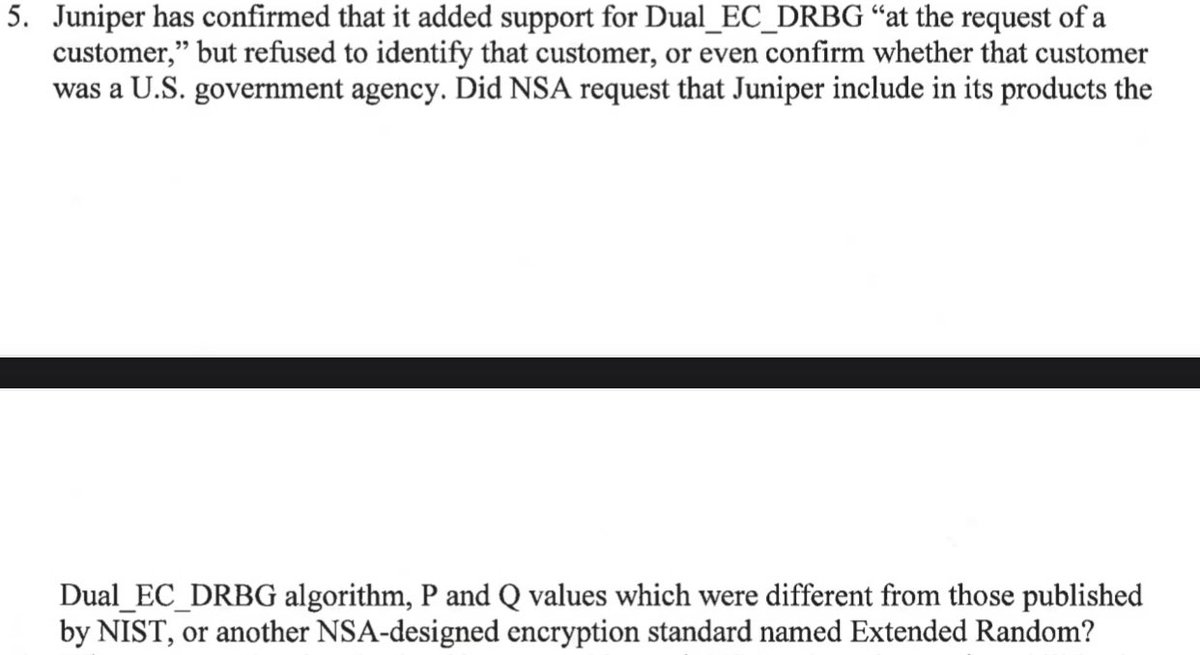
Oh gosh I’d forgotten that “Extended Random” was recently in the news. Senator Wyden asked about it in this letter. wyden.senate.gov/imo/media/doc/… 
• • •
Missing some Tweet in this thread? You can try to
force a refresh