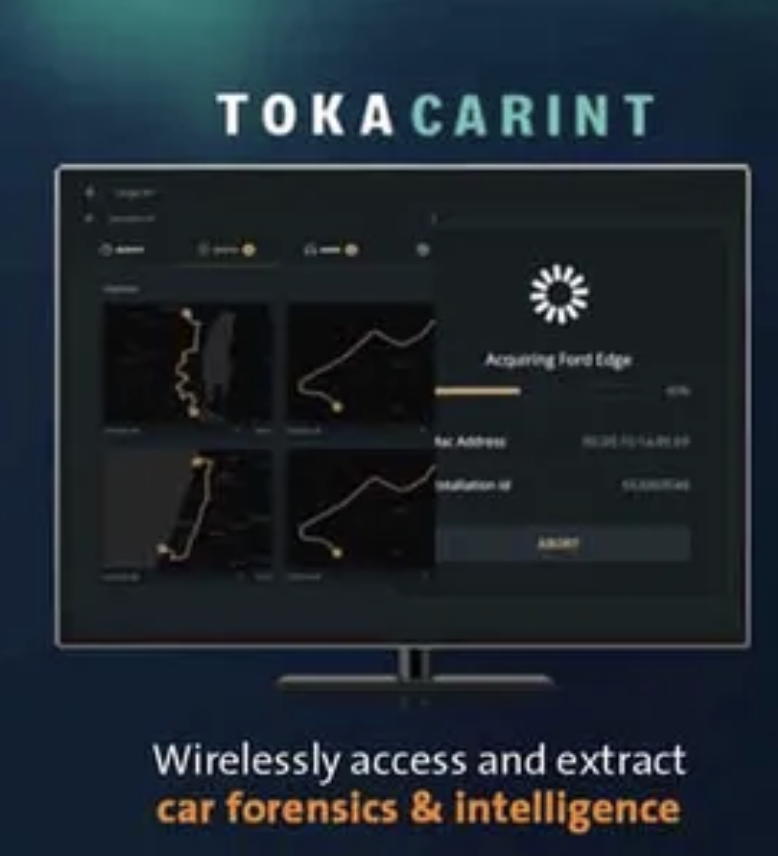
NEW: in November Jessica Watkins was training a paramilitary group to be "fighting fit" while "awaiting direction" from President Trump.
By December 29th, a text exchange showed she perceived that Trump had given the signal.
Per: Gov detention memo.
h/t @ryanjreilly THREAD

By December 29th, a text exchange showed she perceived that Trump had given the signal.
Per: Gov detention memo.
h/t @ryanjreilly THREAD


2/ Folks will remember Jessica Watkins as part of the disciplined "stack" of #Oathkeepers moving up to the #Capitol doors, then forcing entry.
Video: @rstevensbrody
Video: @rstevensbrody
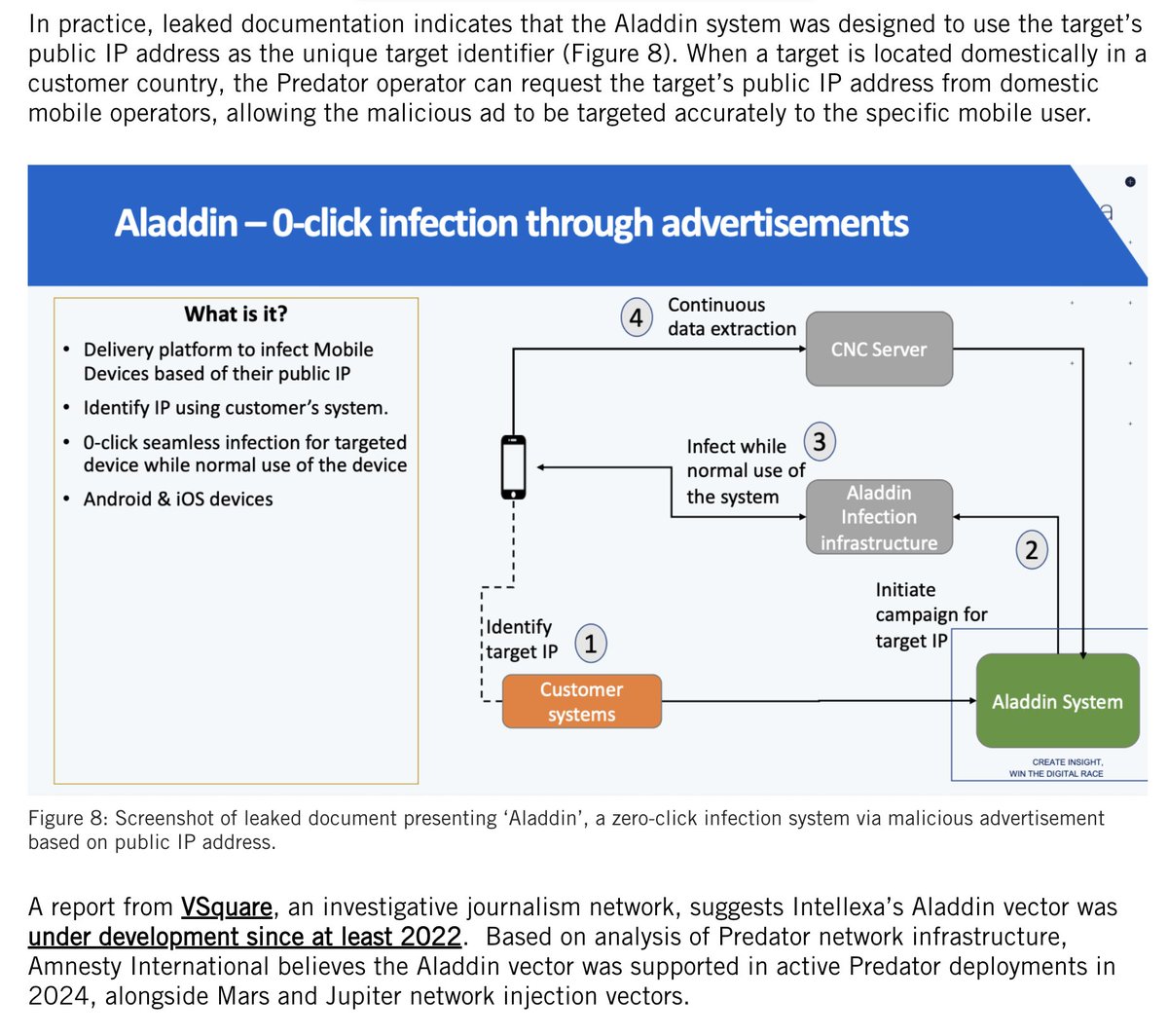
3/ The Gov memo begins by highlighting the call for action made by #OathKeepers leader Elmer Stuart Rhodes on their website.
I'm including a screenshot of it: "TAKE AMERICA BACK. BE THERE. WILL BE WILD."

I'm including a screenshot of it: "TAKE AMERICA BACK. BE THERE. WILL BE WILD."


4/ “I need you fighting fit by innaugeration.” [sic]
In October, Watkins was actively recruiting new militia members for the operation.
And discussing the need to "go underground" if Biden came into power.
In October, Watkins was actively recruiting new militia members for the operation.
And discussing the need to "go underground" if Biden came into power.

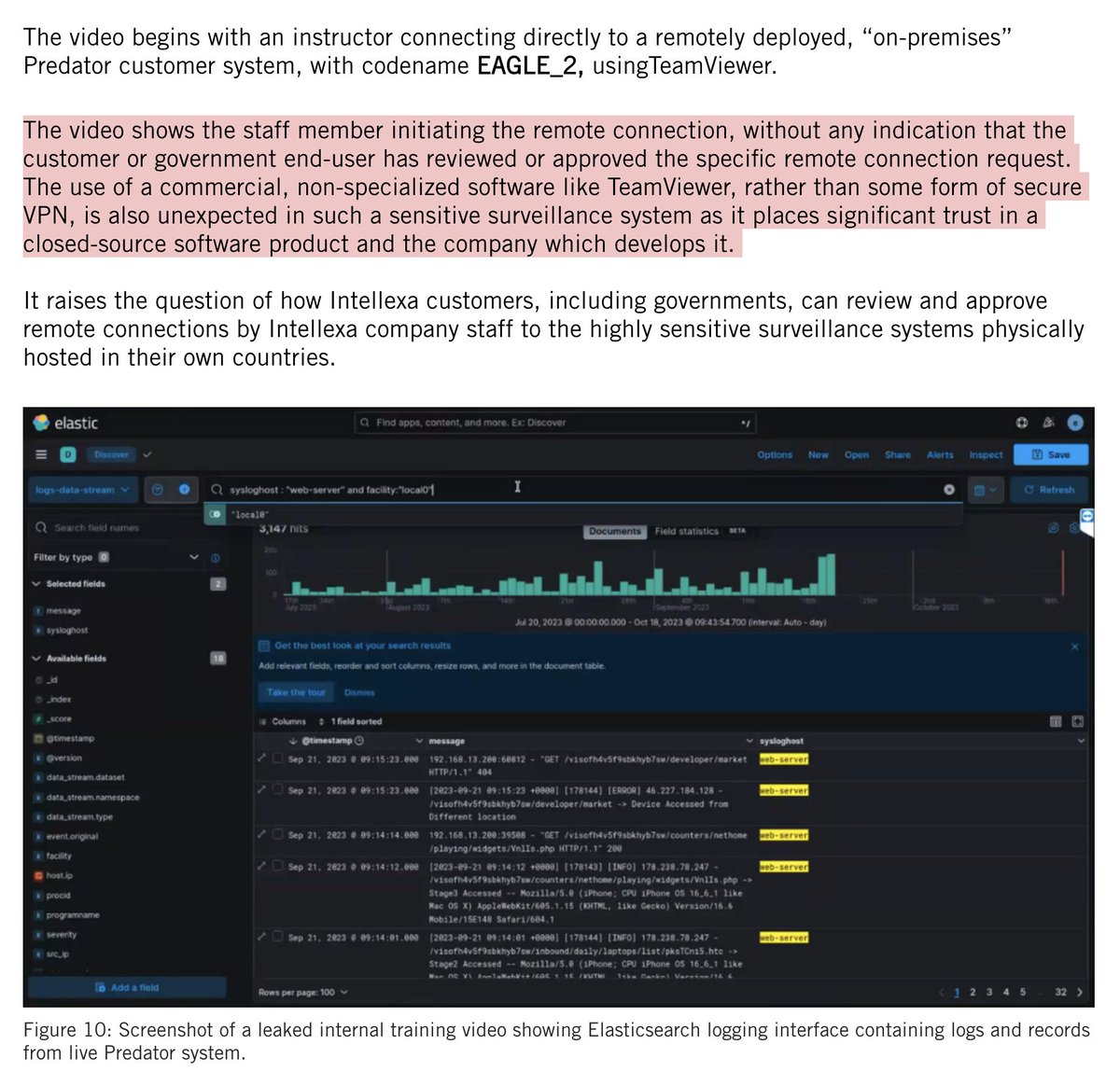
5/ 🚨CHILLING: The Jan6 Quick Reaction Force was "our Law Enforcement members of Oathkeepers".
Context: The group had a planned armed QRF outside DC during previous protests that would "await...orders to enter DC under permission from Trump" and then bring in weapons.


Context: The group had a planned armed QRF outside DC during previous protests that would "await...orders to enter DC under permission from Trump" and then bring in weapons.



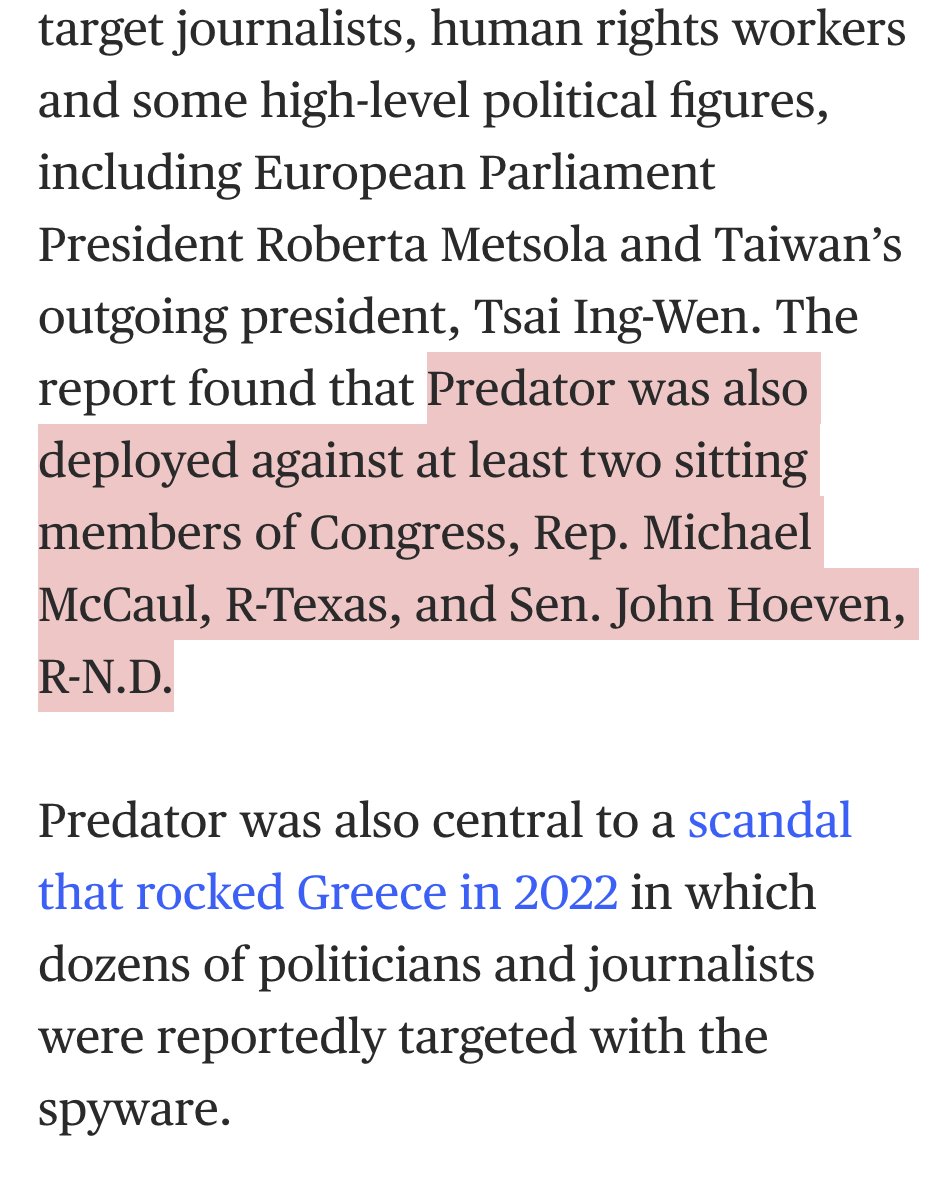
6/ NEW pic: memo shows cluster of #Oathkeepers bunching inside the #Capitol, seen on what looks like Capitol CCTV. Watkins is highlighted with a yellow arrow. 

7/ Reminder: Watkins was not alone.
-Indicted alongside vets Thomas Caldwell & Donovan Crowl.
-Participated in an #Oathkeepers "leadership only" phone conference & passed along directives.
- Apparent coordination among other Oath Keepers👇
-Etc.

-Indicted alongside vets Thomas Caldwell & Donovan Crowl.
-Participated in an #Oathkeepers "leadership only" phone conference & passed along directives.
- Apparent coordination among other Oath Keepers👇
-Etc.
https://twitter.com/jsrailton/status/1355290684249559045

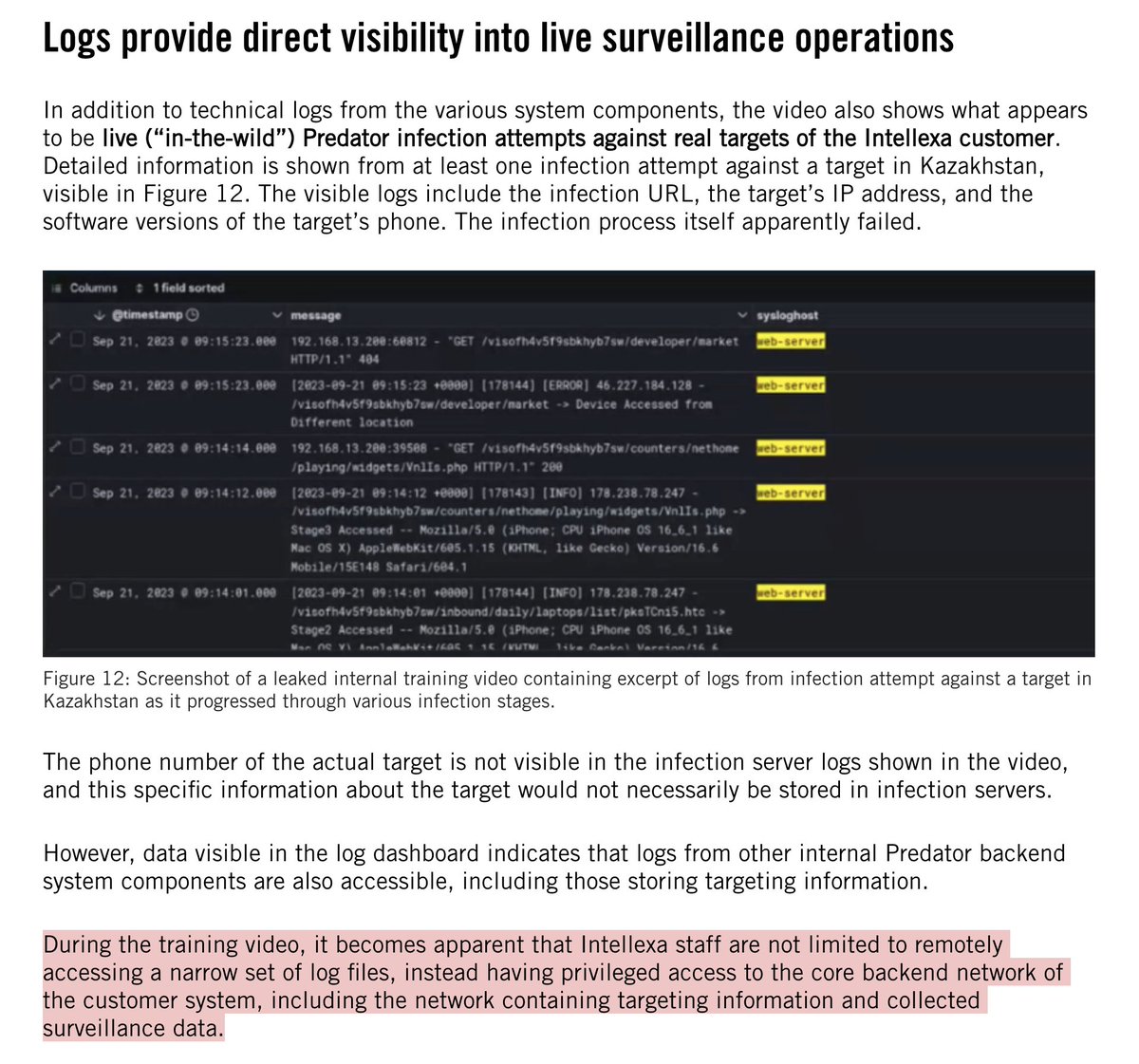
8/ The memo's factual background finishes with mention of Elmer Stuart Rhodes' disturbing "Warning Order" from January.
I tweeted a bit about it at the time👇
I tweeted a bit about it at the time👇
https://twitter.com/jsrailton/status/1352700362579464192

• • •
Missing some Tweet in this thread? You can try to
force a refresh