Wild story: Meet Kurt Jantz (rap name Forgiato Blow aka 'Donald Trump's Nephew').
By his telling, he's the grandson of Auto Trader's founder.
Jantz flew to DC in a private jet on January 6th... 1/
Pics: Parler, Facebook.


By his telling, he's the grandson of Auto Trader's founder.
Jantz flew to DC in a private jet on January 6th... 1/
Pics: Parler, Facebook.



2/ Jantz and entourage then went to the #Capitol and filmed the pro-Trump "We Outside" rap video restricted grounds.. in the middle of the siege.
Lyrics like:
"my president is Trump never be sleepy Joe.."
"free all my people at last or Imma have to hit em with the gas""



Lyrics like:
"my president is Trump never be sleepy Joe.."
"free all my people at last or Imma have to hit em with the gas""


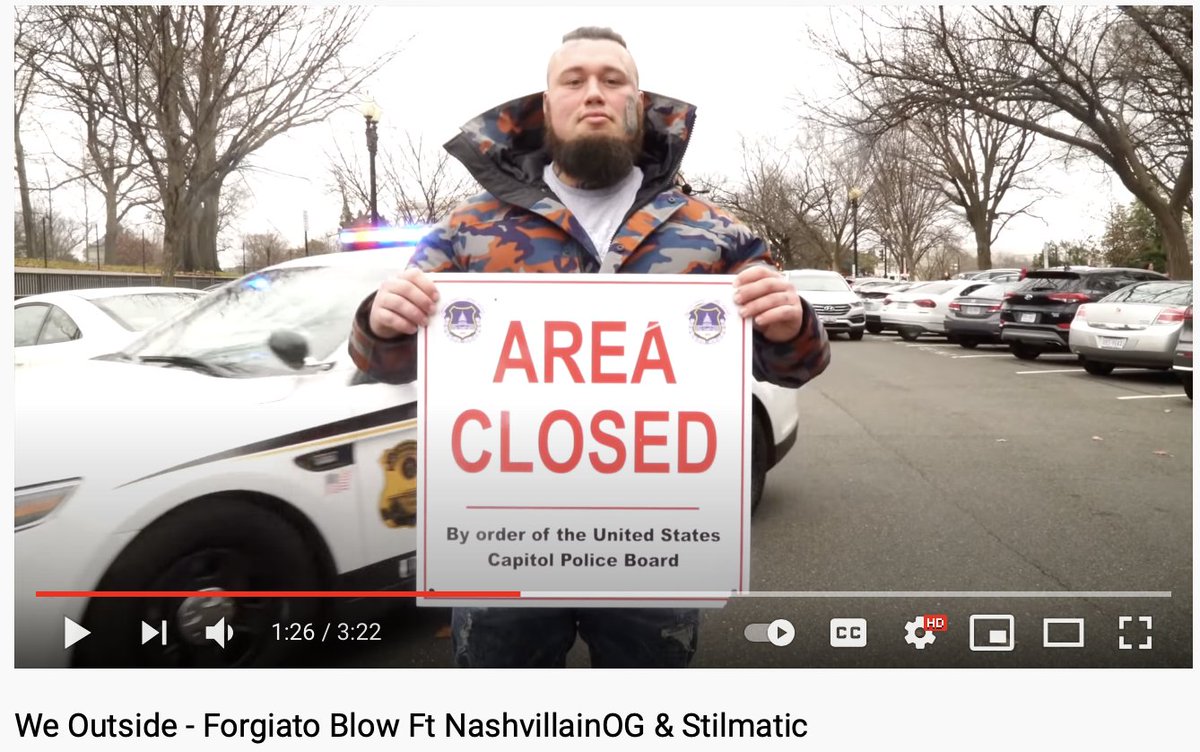

3/ Jantz jetted home. His spokesperson told @donie @CNN he didn't enter the #Capitol building.
He did keep up the flow of music videos, which bring us to him dancing with Roger Stone at CPAC.
He did keep up the flow of music videos, which bring us to him dancing with Roger Stone at CPAC.
4/ This was for a music video mocking the investigation. Featuring #ProudBoys leader Enrique Tarrio
Refrain: "the feds did a sweep they was knocking at the front door, patriots pulling up they was knocking on the #Capitol"
Check out @donie's piece.👇



Refrain: "the feds did a sweep they was knocking at the front door, patriots pulling up they was knocking on the #Capitol"
Check out @donie's piece.👇
https://twitter.com/donie/status/1367508288372416514



5/ Why is this interesting? Jantz is a (niche) cultural figure recasting the #Capitol siege in a positive light... away from the huge stigma it has for most...marketing it and making it look cool while taunting the feds in the process.
6/ Lest you think Forgiato Blow is completely marginal: he did a remixed Ice Ice Baby video with @vanillaice & @RickRoss in 2019. He also toured with Vanilla Ice for a minute.
More: koncrete.com/florida-rapper…



More: koncrete.com/florida-rapper…




7. Please, someone do a piece on the #MAGAhadeen aesthetic. Forgiato Blow is just the volume-knob-to-11 of the #tacticool look that is all over a certain kind of American's wardrobe right now. 







• • •
Missing some Tweet in this thread? You can try to
force a refresh