Thread on #NOBELIUM's new malware families: #GoldMax (aka #SUNSHUTTLE), #GoldFinder, and #Sibot 👇
https://twitter.com/MalwareRE/status/1367521323531046916
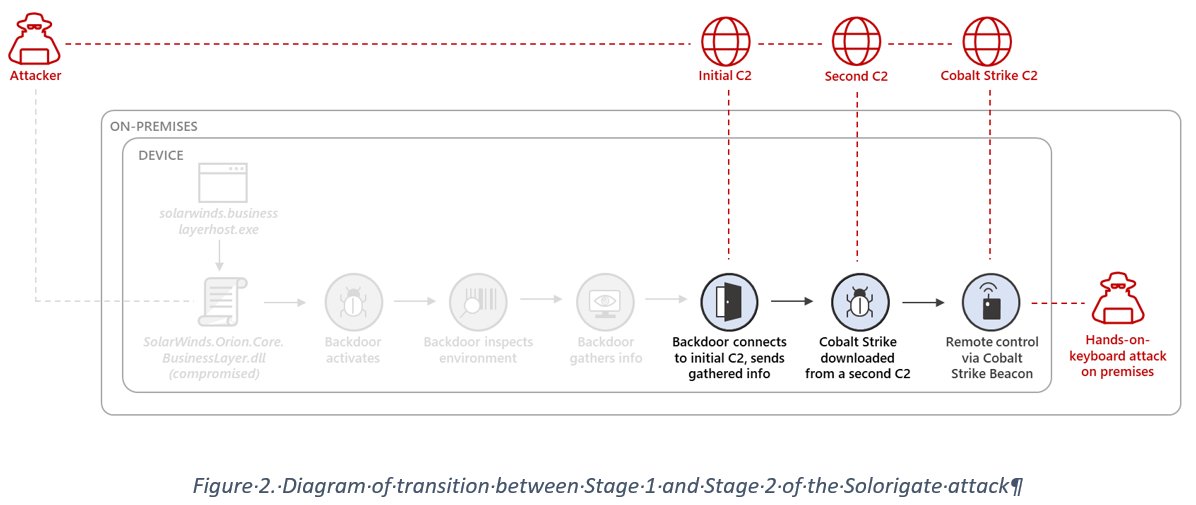
#GoldMax (aka #SUNSHUTTLE) is a new and capable backdoor written in Go/Golang. It is typically used as a late-stage (e.g. 3+) backdoor brought into an environment using access enabled via #TEARDROP, #RainDrop and other related malware deployed by #NOBELIUM/UNC2452.
#GoldMax creates & maintains a config file (name unique to each implant). The config file is AES-256 encrypted (unique-to-each-implant key) & then Base64 encoded (custom alphabet, '=' replaced with null). A handy C2 command allows the operators to update certain config fields. 

#GoldMax's config data contains a field used as an Activation Data/Time value, it allows NOBELIUM to specify (& dynamically update via a C2 command) a "sleep until" data/time (GoldMax checks this value upon execution to determine whether the activation date has been reached yet). 

#GoldMax's config data also contains a decoy traffic generation switch. If enabled, GoldMax issues a pseudo-random number of decoy HTTP GET requests (e.g. to legitimate site using Referer pointing to legitimate sites) to accompany/dilute its actual C2 traffic. 

#GoldMax reaches out to its C2 sever to request a session key. The initial GET request contains a set of hardcoded but unique-to-each-implant Cookie values. These Cookies are meant to authenticate each implant & communicate GoldMax's intentions when dialing into its C2 server. 

The GET request is manually crafted to include the custom cookies above, hardcoded User-Agent and pseudo-randomly selected Referer values. 

After receiving the expected response from its C2 that a unique session key has been exclusively prepared for the implant, #GoldMax sends another HTTP GET request to its C2 similar to the first GET request with only difference being the value of one of the cookies (i.e. op code). 

Next, #GoldMax receives an RSA encrypted session key (Base64-encoded). Each instance of GoldMax contains an RSA private key (PEM) which GoldMax uses to decrypt the RSA-OAEP-encrypted session key received from its C2. The Decrypted session key is AES-256 key.
To retrieve an encoded-encrypted C2 command, #GoldMax sends an HTTP GET request to its C2 that contains a single Cookie value that is also present in the session key generation/retrieval requests (potentially an identifier value for the implant/victim that has to be present). 

#GoldMax's C2 commands are encrypted (AES-256) and encoded (Base64 using a custom alphabet). Each C2 command is AES encrypted using the session key. C2 commands are represented as seemingly random strings that are unique to each implant but known to the C2 server.
#GoldMax's C2 commands allow its operators to download & execute files on the compromised system, upload files from the compromised system to the C2 server, execute OS commands on the compromised system, spawn a command shell, and dynamically update GoldMax’s configuration data.
The dynamic updates to #GoldMax's configuration data/file enable the operators to remotely set a new activation date, replace the existing C2 URL and User-Agent values, enable/disable decoy network traffic feature, and update the number range used by its PRNG.
#Sibot is a malicious downloader implemented in VBScript. It is designed to achieve persistence on the infected machine then download and execute a payload from a C2 server (typically a compromised server). Sibot either comes as a standalone .vbs or stored in a registry key.
#GoldFinder (not #GoldMax) can be used as a custom HTTP tracer tool that logs the route or hops that a packet takes to reach a hardcoded C2. GoldFinder can be used to illuminate all HTTP Proxy servers & redirectors an request would traverse through to reach an intended C2 server.
Both #GoldMax/#GoldFinder were compiled Go ver. 1.14.2 (released in April 2020). The main Go source files for both were located under /var/www/html/builds/. The Go packages and libraries used during the compilation process were mostly located under /var/www/html/go/src/.
What makes detection of #GoldMax challenging:
Activation date
Unique-to-each-implant:
🔸Filename/path
🔸C2 URL
🔸AES-256 key for config
🔸AES-256 session key
🔸ID & op code Cookies
🔸ASCII C2 commands
🔸RSA private key
🔸...
Overall good code opsec (minimal sig'able patterns)
...
Activation date
Unique-to-each-implant:
🔸Filename/path
🔸C2 URL
🔸AES-256 key for config
🔸AES-256 session key
🔸ID & op code Cookies
🔸ASCII C2 commands
🔸RSA private key
🔸...
Overall good code opsec (minimal sig'able patterns)
...
• • •
Missing some Tweet in this thread? You can try to
force a refresh