It's a day ending in "y", and a bunch of similar-looking accounts are attaching four letter codes to their otherwise identical tweets denying genocide and downplaying human rights abuses in Xinjiang. #TuesdayAstroturf
cc: @ZellaQuixote
cc: @ZellaQuixote

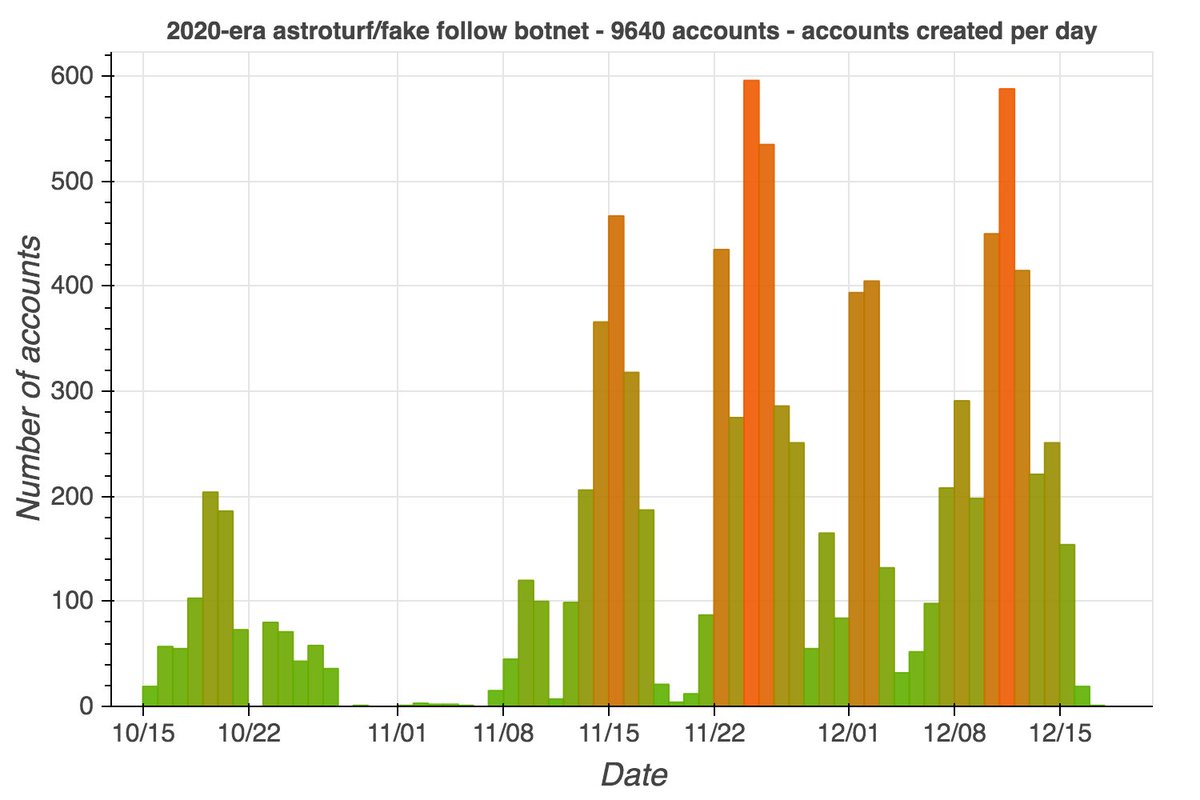
We found a network of 113 accounts posting duplicate tweets about Xinjiang with random four letter codes appended. All were created between December 2020 and February 2021, generally in batches of accounts with similar naming schemes. Most use photos of scenery as profile pics. 





These 113 accounts (allegedly) post all of their tweets via the Twitter Web App, generally in brief tweetstorms where most/all of the accounts tweet within an hour or so of each other. Most tweets are in English or Chinese, but the network has tweeted in 31 languages thus far. 



This botnet links a variety of websites, mostly Chinese state media sites such as Global Times as CGTN or Chinese government sites (including multiple embassies). YouTube also turns up frequently. 



This network's content is repetitive, with many tweets having been duplicated verbatim (other than the random 4 letter codes) by dozens of the accounts in the network. Many of the duplicate tweets are headlines from Chinese media sites without accompanying article links. 

This network generally sends all copies of a given tweet on the same day (and usually within an hour or two of each other). Xinjiang is the dominant theme (specifically, claims that no genocide, forced labor, or other human rights violations are occurring there). 

This is not the first time we've encountered astroturf networks pushing propaganda denying human rights abuses in Xinjiang. Here are two threads on previous networks (both of which have been shut down by Twitter):
https://twitter.com/conspirator0/status/1333084194990383109
https://twitter.com/conspirator0/status/1352408453143269378
• • •
Missing some Tweet in this thread? You can try to
force a refresh