
Today, @SentinelOne published a report on "XcodeSpy", a new macOS malware specimen. 🍎👾
📝 "New macOS malware XcodeSpy Targets Xcode Developers": labs.sentinelone.com/new-macos-malw…
Q: Can our free open-source tools protect you ...with no a priori knowledge of this insidious threat?
📝 "New macOS malware XcodeSpy Targets Xcode Developers": labs.sentinelone.com/new-macos-malw…
Q: Can our free open-source tools protect you ...with no a priori knowledge of this insidious threat?

When the malicious script in the infected Xcode project is executed and attempts to connect to the attacker's remote C&C server for tasking (via /bin/bash), LuLu will intercept this, and alert you: 

If we allow the malicious payload (EggShell), to be downloaded from the server ....when it attempts to persistently install itself as a Launch Agent, BlockBlock will alert you: 

If we allow the malware to persist, a subsequent KnockKnock scan will flag the malware's Launch Item persistence: 

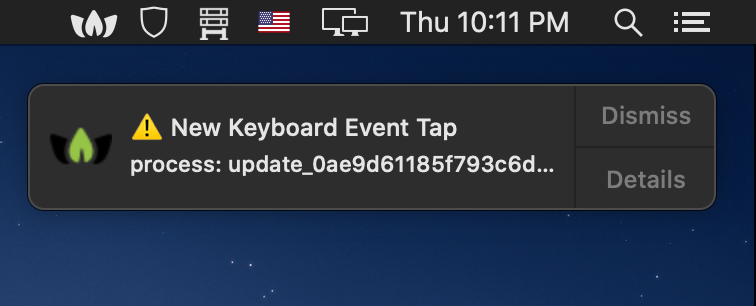
Our other tools, such as OverSight, will detect when it attempts to access the mic or camera, while Reikey, will detect the malware's keylogger logic: 
If you're interested in studying this malware, just added a sample to our public macOS malware repository: objective-see.com/malware.html (pw: infect3d)
...just don't infect yourself 😂
...just don't infect yourself 😂

• • •
Missing some Tweet in this thread? You can try to
force a refresh


