
🚨@Coldcard MK3 PIN Replacement Attack🚨
I bypassed an MK3 security feature which prevented needing 100% trust in the SE, not serious by itself..
However, when paired with a second attack on the SE it allowed for seed extraction if an attacker steals your wallet
Video below👇
I bypassed an MK3 security feature which prevented needing 100% trust in the SE, not serious by itself..
However, when paired with a second attack on the SE it allowed for seed extraction if an attacker steals your wallet
Video below👇

Hardware wallets are 100x safer than using only a PC. Don’t stop using your HWW, it is very safe. Just be aware it is not invincible. Choose a good passphrase and be cautious and provide physical protection of your HWW as best you can.
Please ask any questions you have!
Please ask any questions you have!
Video moves fast, pause it to read.
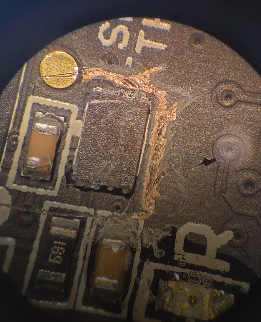
I take apart the device, remove the SE. Update the PIN externally. Also reset the pin attempt counter.
There are a number of power up tests to make sure its still working 😂
I take apart the device, remove the SE. Update the PIN externally. Also reset the pin attempt counter.
There are a number of power up tests to make sure its still working 😂
The attack allows the replacement of your PIN in the SE with attacker PIN and then unlock your wallet with full access.
The attack requires a high level of skill. The attack does NOT recover your passphrase + requires physical theft of the CC.
Fix: ATECC608B + Bootloader v2.0.1
The attack requires a high level of skill. The attack does NOT recover your passphrase + requires physical theft of the CC.
Fix: ATECC608B + Bootloader v2.0.1
Check your bootloader version and SE version by going to the menu then Advanced -> Upgrade -> Version Info and then scroll down. 

MK3 security overview:
The MK3 added an additional secret known only to the MCU to encrypt your secret key. It was intended to prevent a secure element (SE) backdoor from totally breaking your security. Very wise addition.
The MK3 added an additional secret known only to the MCU to encrypt your secret key. It was intended to prevent a secure element (SE) backdoor from totally breaking your security. Very wise addition.
I knew the MK3 did this, but the @DonjonLedger attack on the MK2 SE triggered me to check closer into this feature just to see if I could mount an attack on the MK3 and 608.
https://twitter.com/DonjonLedger/status/1262390534003400704?s=20
I found an error in the MK3 architecture for the feature. The method used encrypted the seed. However, the PIN hash slot was left unprotected from an SE break. If an attacker recovers slots 1, 3 from the SE he can replace the user's PIN and take full control of the wallet.
The PIN validation is done in 3 parts:
pin_hash()
ae_stretch_iter()
ae_mixin_key()
Might look complex but they really aren’t. Hashing rounds just involve mixing SE,MCU and user secrets + constants. This results in a final value that requires, SE, MCU and User to all collaborate.


pin_hash()
ae_stretch_iter()
ae_mixin_key()
Might look complex but they really aren’t. Hashing rounds just involve mixing SE,MCU and user secrets + constants. This results in a final value that requires, SE, MCU and User to all collaborate.
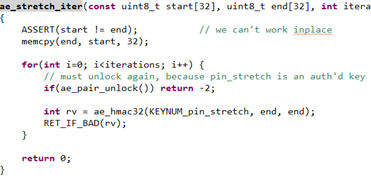
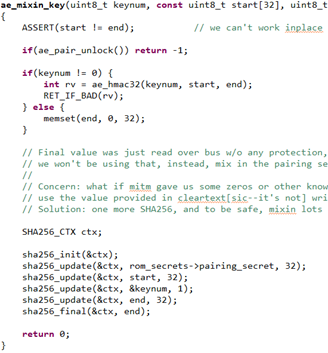
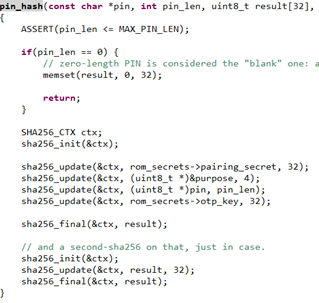
Hash should match the value in slot 3. Knowledge of this allows the MCU to unlock the encrypted secret in SE slot 9. The MCU then decrypts the secret using a MCU only secret called the otp_key. This prevents an attacker from just breaking slot 9 on the SE and recover the secret.
If you look at the hashing carefully you can see otp_key is not used in the calculation of the PIN hash. So the SE slot 3 can be changed if you know the current value. So breaking the SE allows you to trick the MCU in to decrypting the seed. This gives the attacker full access.
Previous to the ledger attack disclosure, attacking the SE seemed to difficult, however their methodology has allowed others to preform this LFI attack. I have a contact at a lab that was able to achieve the ledger attack on the 608. They wish to remain anonymous.
What the hell does all this mean?
Don't invite me over for coffee.
Don't invite me over for coffee.
Also it should be noted, I could have faked everything in the video... So you really only have my reputation to go by. But if someone wants to question my reputation and make me a bet... I'm open to taking their money 😂
This attack disclosure is 40% to help users and 60% for me just to brag.
** @COLDCARDwallet not what I typed...
• • •
Missing some Tweet in this thread? You can try to
force a refresh


