
🍪IAM Access Analyzer has a new treat for all you permission setters out there in #AWS land.🍪Now, Access Analyzer generates policies based on your CloudTrail activity. (1/11)
amzn.to/3wzIJlR
amzn.to/3wzIJlR
We all know that when you starting building in development, you probably start with broader permissions since you may not know what you need...yet. But you need to shrink those permissions as you move to production. For this part, you can call on Access Analyzer! (2/11)
🔍After you’ve run your workload. You give us the role for your workload, your CloudTrail trail, and a date range. Then Access Analyzer does what it does best...analyzes! 🔍 (3/11)
Access Analyzer generates a policy with action-level permissions for 16 rather popular services. Such as EC2, Lambda, IAM, and S3. For the others, we tell you if the service was used and you can specify the actions. (4/11)
We are actively working on generating action-level policies across more services. Stay tuned! (5/11)
Okay so now that you know what it does. Here are my top5⃣reasons why this is a big deal for permissions in AWS. Here we go! (6/11)
1⃣ Access Analyzer generates fine-grained policies guiding you to set least privilege permissions based on what you actually need. (7/11) 

2⃣ Policies adhere to the IAM policy language for each AWS service. You can request policies that include resource level templates. This makes it easier to specify resource-level permissions. (8/11) 
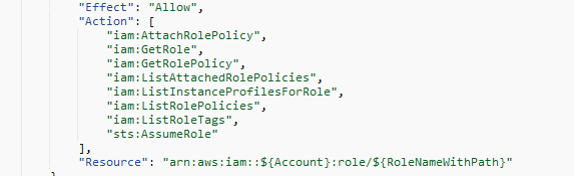
3⃣Access Analyzer does the heavy lifting🏋️♀️for you to analyze what you actually need based on your CloudTrail activity. This helps you get to the right permissions sooner and at no additional cost. (9/11)
4⃣Customers tell us they want to “shrink wrap” their permissions. Access Analyzer now sets you up for success to do this for your workloads. (10/11)
5⃣Access Analyzer now helps you generate fine-grained policies, validate policies, and review public and cross account access. We got your back each step of the way! 👏👏👏
Congrats to the team! 🥳🎉🍾
• • •
Missing some Tweet in this thread? You can try to
force a refresh





