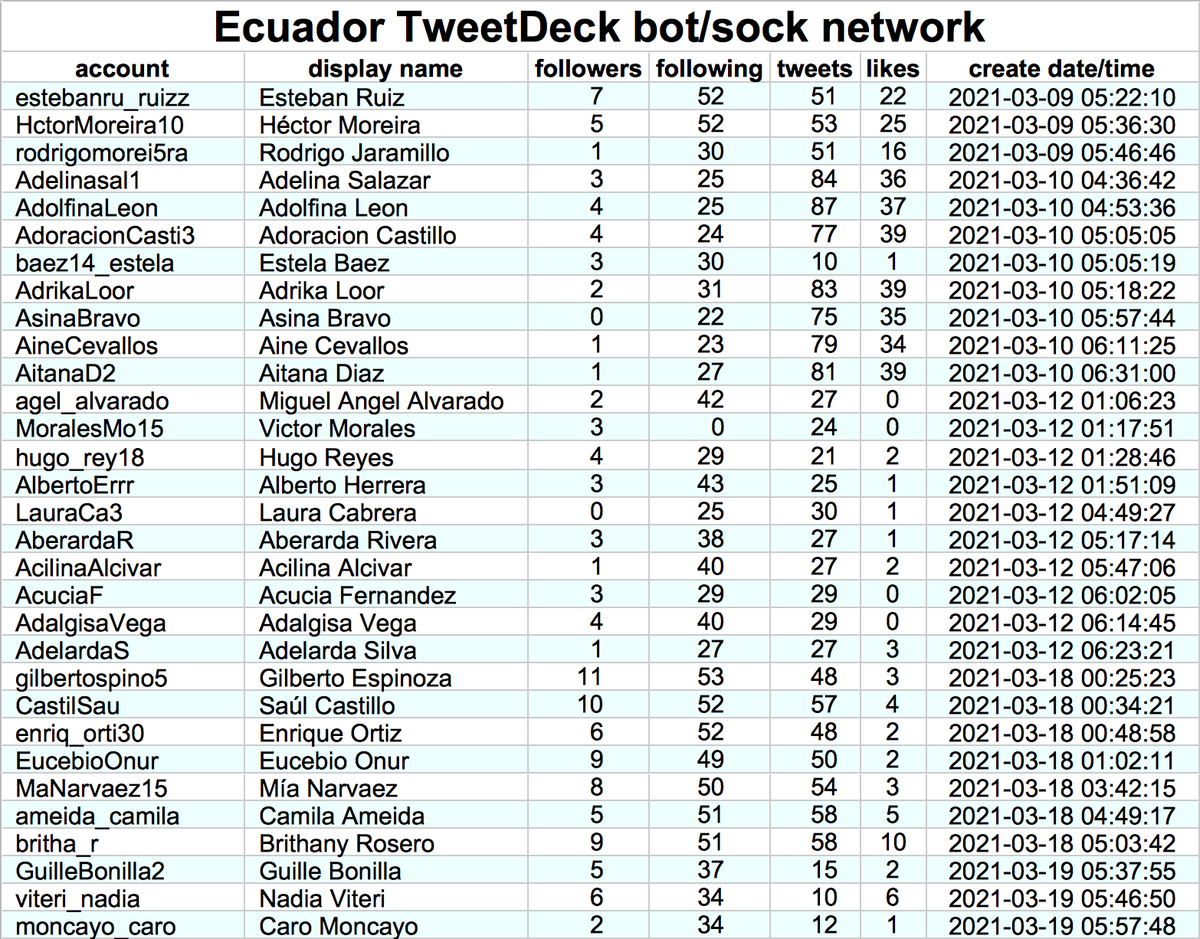
Meet @An_mal11, @An_mal12, @An_mal13, @An_mal14, @An_mal15, @An_mal16, @an_mal17, and @An_mal18. This collection of similarly-named tiny Twitter accounts could be yours for $71, but you should probably save your money.
cc: @ZellaQuixote
cc: @ZellaQuixote

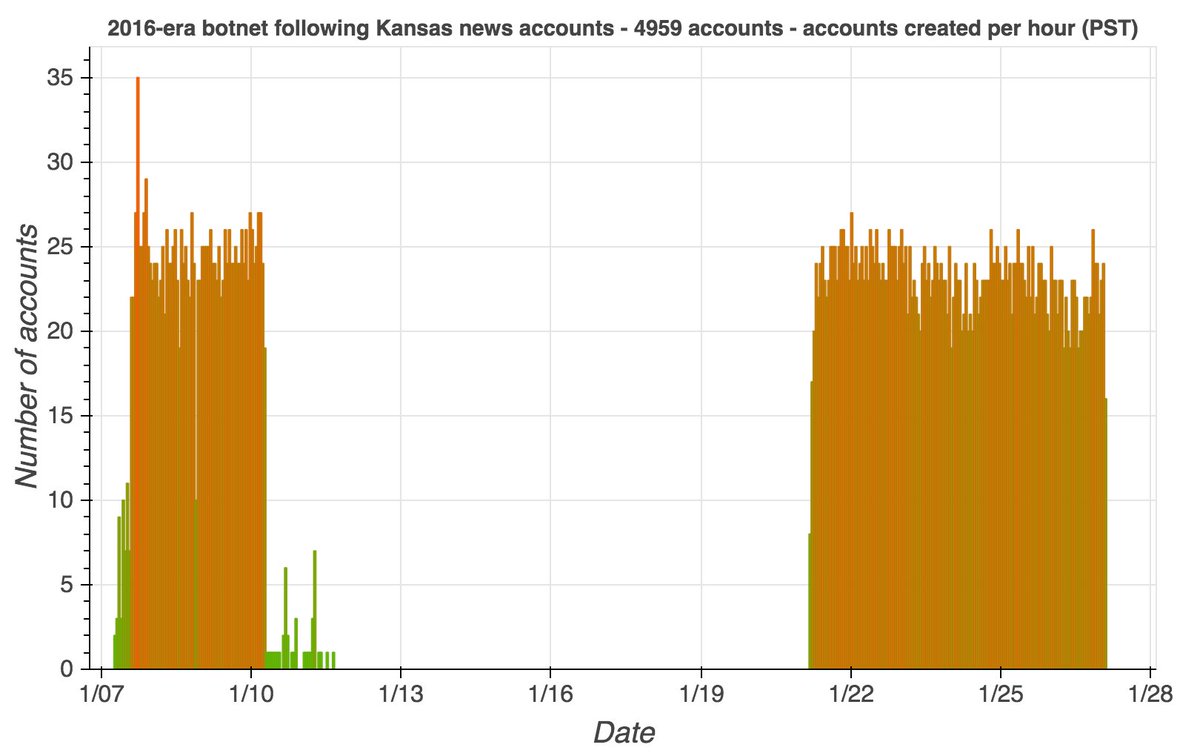
These eight accounts were all created on either February 18th or February 21st, 2021. Thus far, they have tweeted very little (only 58 tweets), and have sent all their tweets via the Twitter Android app. Two of them (@An_mal12 and @An_mal14) currently have identical biographies. 



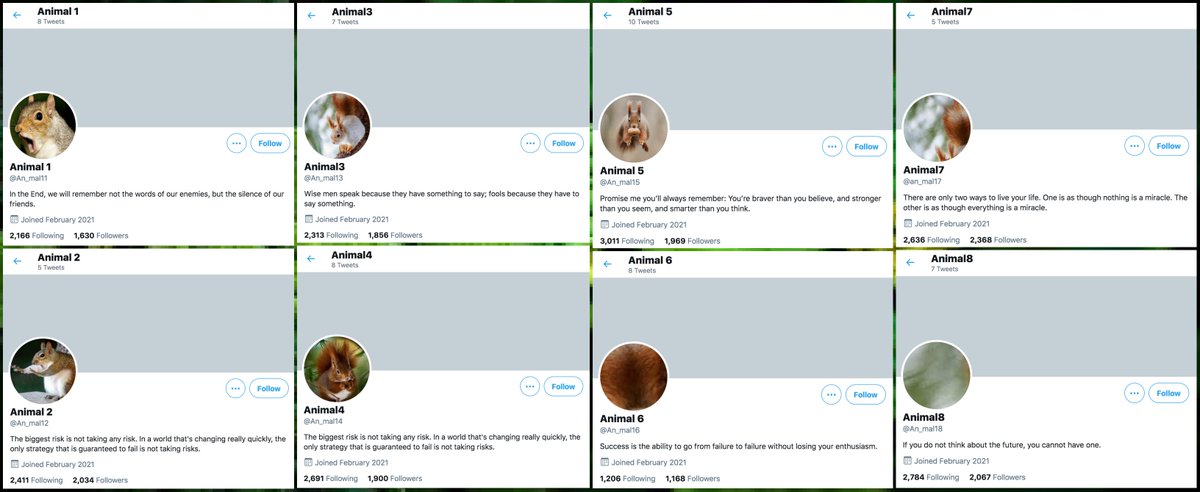

The majority of these accounts' tweets so far are extremely brief replies to each other (and sometimes replies to each other's replies to each other, and so on). They have also posted a few follower growth tweets, including retweets of a tweet that contains a likely malware link. 



Each of the eight accounts in this network follows all seven of the others (in many cases, the accounts are each other's earliest followers). This diagram shows both the follow and reply relationships between the accounts in the network. 

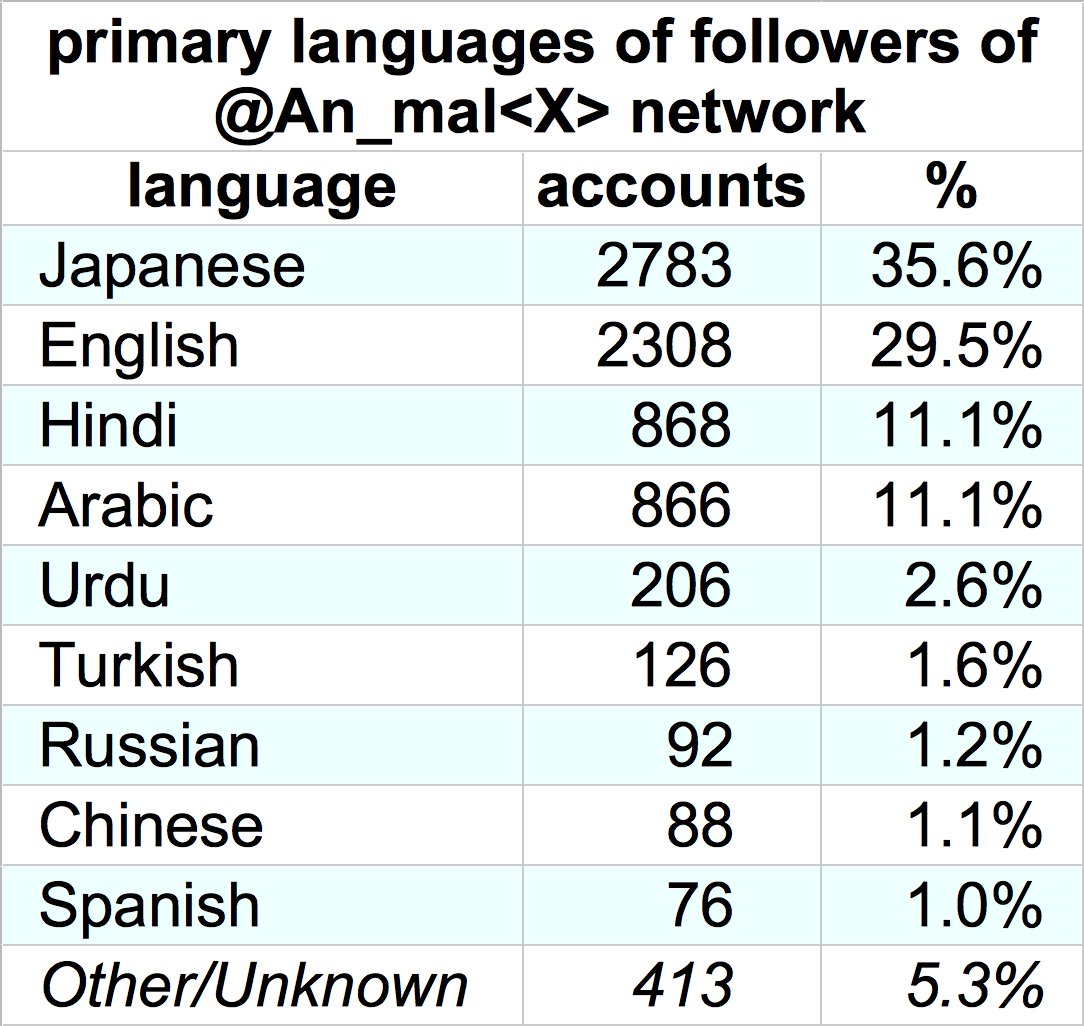
How did these accounts build their following? They appear to be fishing for followbacks from small accounts in a variety of languages (chiefly Japanese, English, and Hindi). These accounts mostly don't look automated, but do tweet a lot of followback spam. 
(old thread on the malware link that this network amplified and associated spam)
https://twitter.com/conspirator0/status/1246163645383561216
(thread on the account sales site this network was listed on)
https://twitter.com/conspirator0/status/1281064275524673536
• • •
Missing some Tweet in this thread? You can try to
force a refresh