Alright everybody, join me as I relay a heist that took place across blocks yesterday and unveil a novel form of MEV.
Again it will be a long and semi-technical journey but I think it is worth it.
Again it will be a long and semi-technical journey but I think it is worth it.
https://twitter.com/bertcmiller/status/1382449291600535555
I woke up yesterday to a searcher extremely distraught because apparently only 1 of 3 transactions in their bundle landed on-chain.
What's worse is someone else's transaction seemed to have been added instead of their own.
What's worse is someone else's transaction seemed to have been added instead of their own.
A quick look and the searcher seemed to be right.
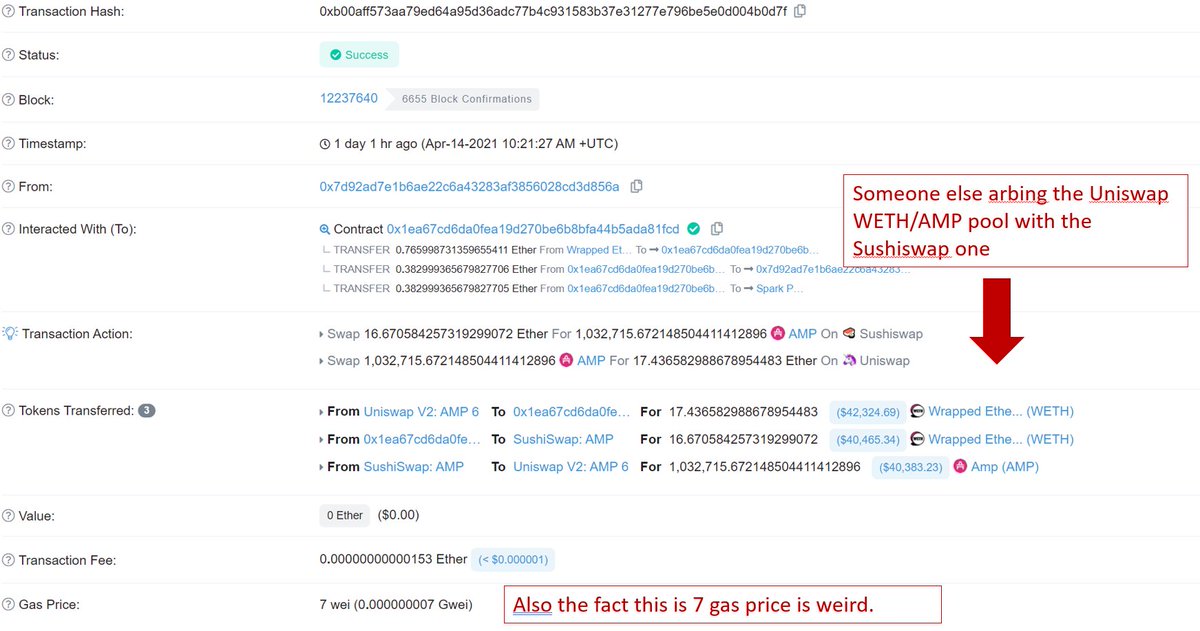
Only the "buy" part of a sandwich bundle they submitted had landed on-chain, and right after that buy someone else had inserted a 7 gas tx arb-ing it
Check the images for a bit more info


Only the "buy" part of a sandwich bundle they submitted had landed on-chain, and right after that buy someone else had inserted a 7 gas tx arb-ing it
Check the images for a bit more info
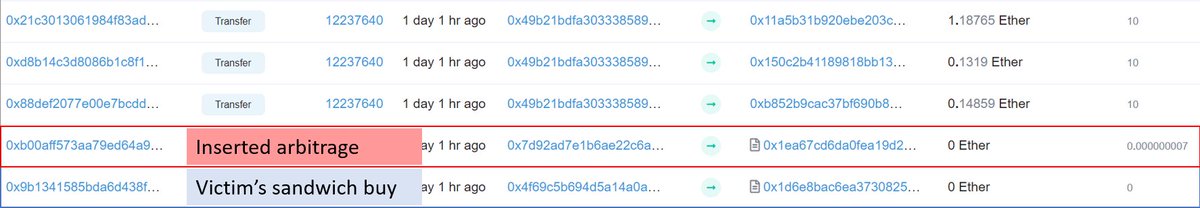
This was a reaaaally big deal!
Bundles are groups of transactions Flashbots users submit. Those transactions must be included in the order submitted, and either the whole bundle is included, or nothing is.
A bundle should never be split up, and no one else should sneak in too!
Bundles are groups of transactions Flashbots users submit. Those transactions must be included in the order submitted, and either the whole bundle is included, or nothing is.
A bundle should never be split up, and no one else should sneak in too!
Interestingly if true this would strongly mirror the 🥪baiting attacks of last week
Someone was taking a 🥪and stopping them from selling somehow. Thus the 🥪-er was left holding some token and their ETH is now potentially vulnerable in a Uniswap pool.
Someone was taking a 🥪and stopping them from selling somehow. Thus the 🥪-er was left holding some token and their ETH is now potentially vulnerable in a Uniswap pool.
https://twitter.com/bertcmiller/status/1381296074086830091
So how did this searcher's bundle get leaked or broken up?! And where did the arb come from?!
Recall that in Ethereum occasionally two blocks are mined at roughly the same time, and only one block can be added to the chain. The other gets "uncled" or orphaned.
For the most part people don't pay much attention to uncled blocks.
For the most part people don't pay much attention to uncled blocks.
But anyone can access transactions in an uncled block and some of the transactions may not have ended up in the non-uncled block.
In a way some transactions end up in a sort of mempool like state: they are now public as a part of the uncled block and perhaps still valid too.
In a way some transactions end up in a sort of mempool like state: they are now public as a part of the uncled block and perhaps still valid too.
The distraught searcher was certain their bundle had been leaked but we had a different hypothesis.
What if their bundle was included an uncled block but NOT the non-uncled block and someone selectively took one of their transactions from that and included it in their bundle?
What if their bundle was included an uncled block but NOT the non-uncled block and someone selectively took one of their transactions from that and included it in their bundle?
If true there should be evidence of this on-chain.
Quickly we began to chase that down. First thing of note was an uncled block was in the right place and it was mined by a Flashbots miner: etherscan.io/uncle/0xa773e5…
Quickly we began to chase that down. First thing of note was an uncled block was in the right place and it was mined by a Flashbots miner: etherscan.io/uncle/0xa773e5…
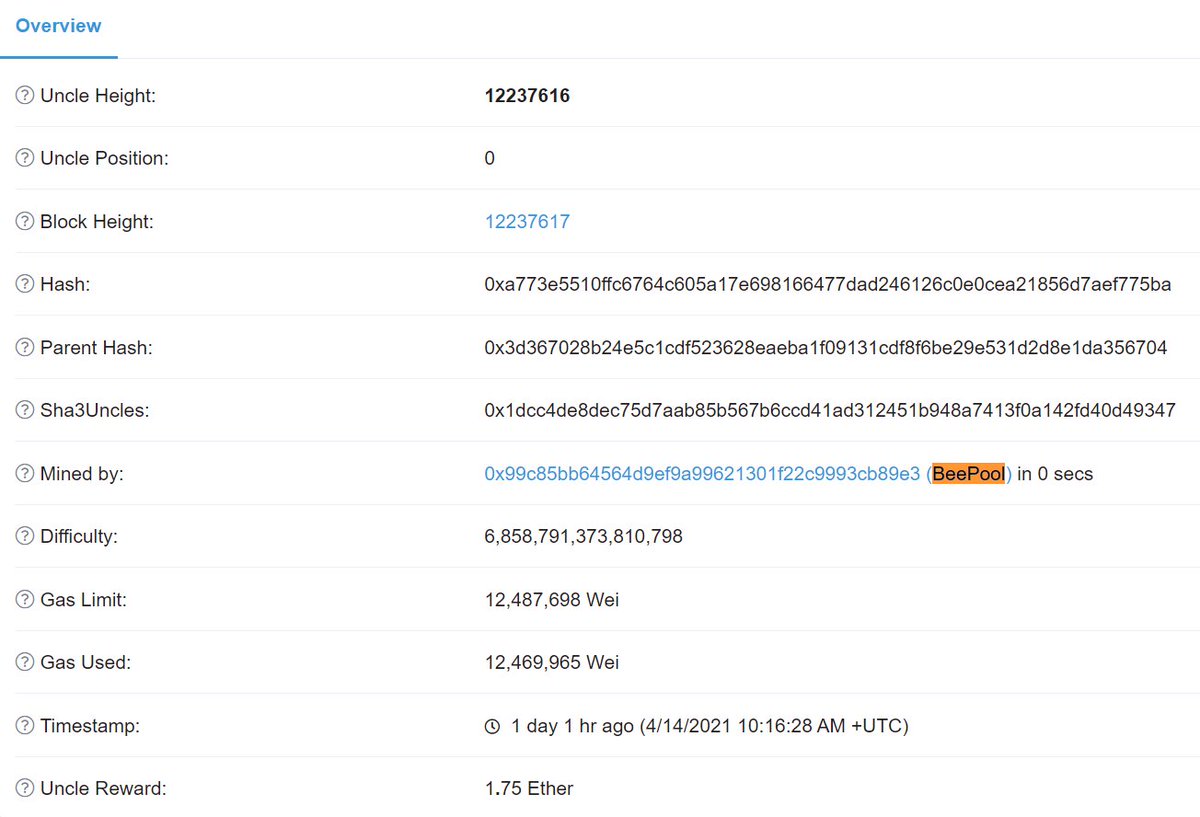
But that could be coincidental and no one on the team even knew how to get uncle transaction data (there's no Etherscan for it as far as I can tell)! It took us awhile to figure out how to confirm this.
Eventually the good folks at @AlchemyPlatform got back to me.
Eventually the good folks at @AlchemyPlatform got back to me.
There was a method we could use to get uncle block's transaction data. I plugged in the uncle block's hash & ctrl+f'd the searcher's buy transaction's hash.
Immediate hit. Their buy transaction hash was at the top of the uncled block. My jaw dropped.
composer.alchemyapi.io/?composer_stat…

Immediate hit. Their buy transaction hash was at the top of the uncled block. My jaw dropped.
composer.alchemyapi.io/?composer_stat…
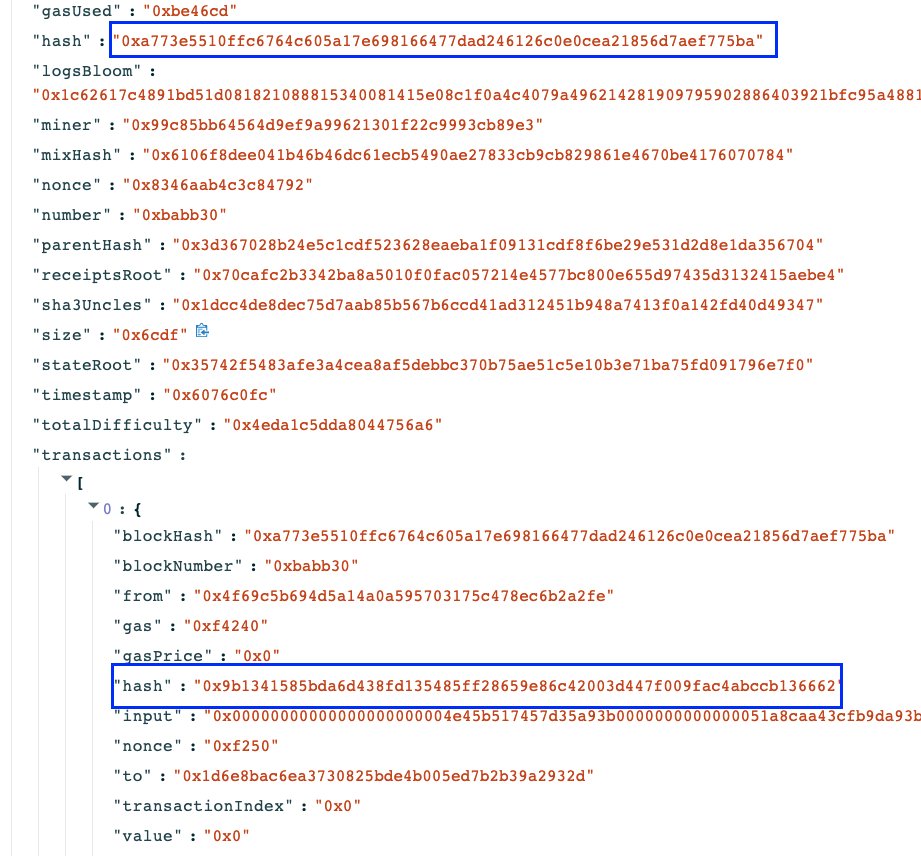
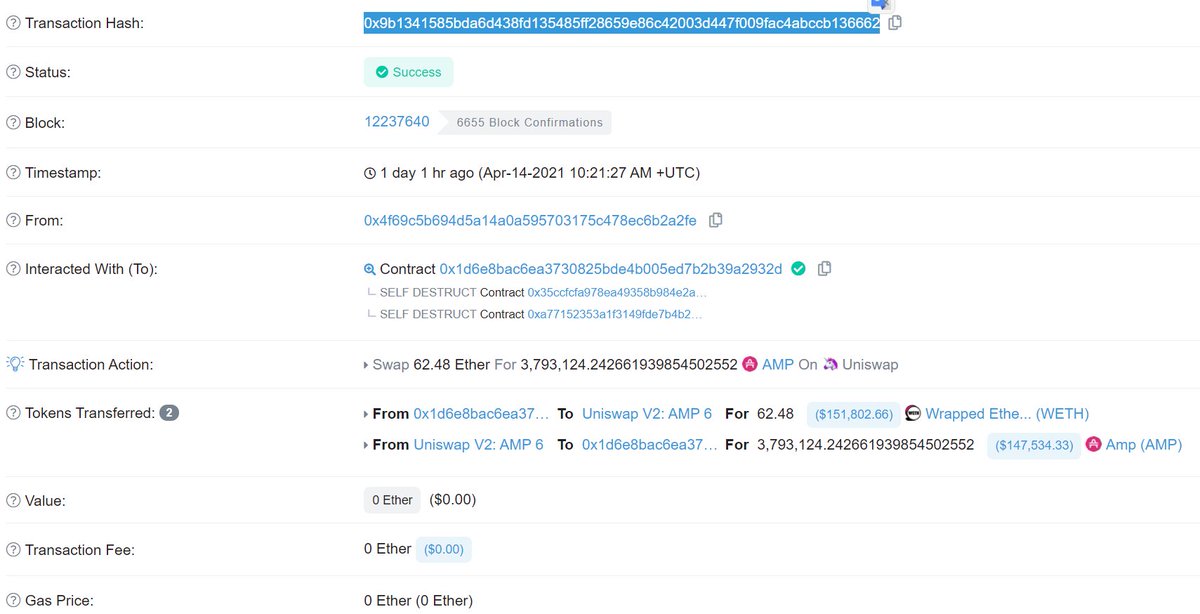
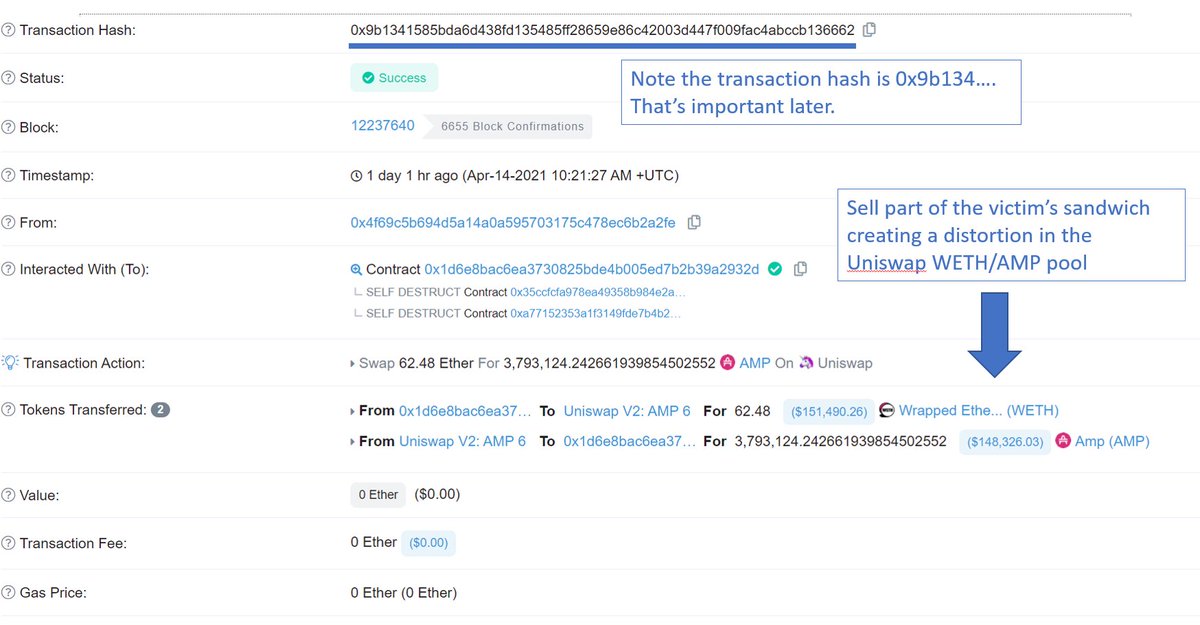
You could also see their full bundle in the uncled block.
First transaction is the buy of the 🥪
Second was someone else they were sandwiching.
Third was the sell of the 🥪
There was no leak. Someone really had pulled off the uncle block attack we hypothesized.
First transaction is the buy of the 🥪
Second was someone else they were sandwiching.
Third was the sell of the 🥪
There was no leak. Someone really had pulled off the uncle block attack we hypothesized.
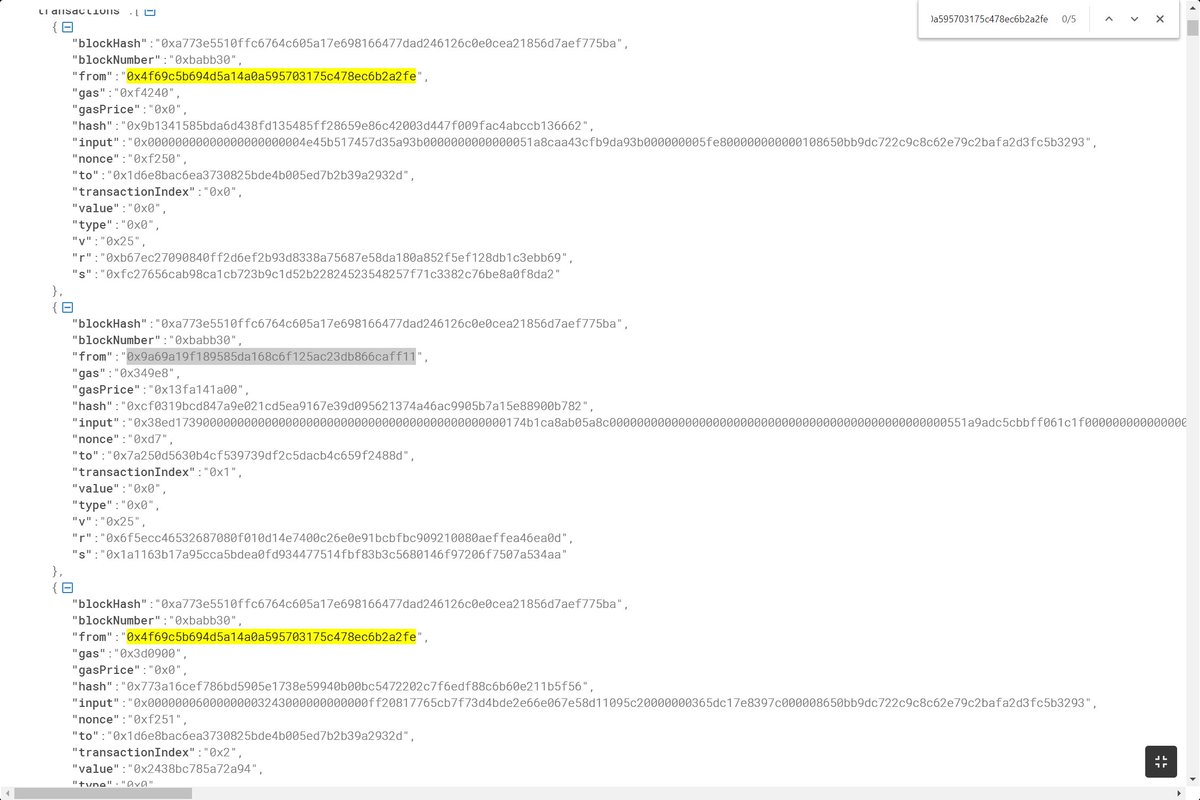
To sum this up here is what happened again:
A 🥪er's bundle was included in an uncled block
An attacker saw this, grabbed only the buy part of the 🥪, threw away the rest, and added an arb after it
The attacker then submitted that as a bundle, which was then mined
A 🥪er's bundle was included in an uncled block
An attacker saw this, grabbed only the buy part of the 🥪, threw away the rest, and added an arb after it
The attacker then submitted that as a bundle, which was then mined
In a way the searcher was right. Their bundle had been leaked but that happened in the normal course of things. Uncles happen all the time.
Actually this searcher was sort of lucky. They were left holding AMP, not something poisoned like 0x2's YoloChain!
Actually this searcher was sort of lucky. They were left holding AMP, not something poisoned like 0x2's YoloChain!
https://twitter.com/bertcmiller/status/1381296111181299713
Afaik this is the 1st case of something like this happening. We're calling this an uncle bandit attack - an ode to time bandit attack.
Instead of seeing something late in time and rewinding it, you're seeing something in an uncle and bringing it forward.
h/t: @epheph
Instead of seeing something late in time and rewinding it, you're seeing something in an uncle and bringing it forward.
h/t: @epheph
The attacker here only made ~0.4 ETH from all of this, but that's enough to incentivize a lot of people to do this going forward.
Also in general uncle bandit attacks are another way 🥪 bots can get rekt. Only a matter of time before someone does so and takes a ton of ETH.
Also in general uncle bandit attacks are another way 🥪 bots can get rekt. Only a matter of time before someone does so and takes a ton of ETH.
And this marks the end of our story today folks.
The reach of the monsters of Ethereum's dark forest extends past the mempool and into uncled blocks too. Where else might we find them in the future?
The reach of the monsters of Ethereum's dark forest extends past the mempool and into uncled blocks too. Where else might we find them in the future?
Huge shout to the Flashbots team who I am eternally grateful to for their tireless and excellent work
@phildaian @tzhen @epheph @ObadiaAlex @thegostep @jparyani @fiiiu_ @tkstanczak
@EdgarArout @taarushv @LukeYoungblood @sui414
@phildaian @tzhen @epheph @ObadiaAlex @thegostep @jparyani @fiiiu_ @tkstanczak
@EdgarArout @taarushv @LukeYoungblood @sui414
Lastly check out our Github to learn more and get involved if you're interested in mitigating MEV's negative externalities:
github.com/flashbots/pm
github.com/flashbots/pm
Taking suggestions for what I should do with my newfound Twitter reach and these incredible stories!
• • •
Missing some Tweet in this thread? You can try to
force a refresh