NEW: An Oracle spokesperson claimed the company's surveillance tech documents were "theoretical" and that Oracle does not sell such tech directly to Chinese police. But she left open the possibility that a broker could do so.
I looked into that. 1/
theintercept.com/2021/04/22/ora…
I looked into that. 1/
theintercept.com/2021/04/22/ora…
Turns out Oracle has worked with several unsavory partners in China, including:
- a reseller active in the PRC 'war industry'
- a subsidiary of state-owned CEC, which is listed by DoD
- a Xinjiang broker tied up with the bingtuan, which runs internment and labor camps 2/
- a reseller active in the PRC 'war industry'
- a subsidiary of state-owned CEC, which is listed by DoD
- a Xinjiang broker tied up with the bingtuan, which runs internment and labor camps 2/
Oracle has a special relationship with Beijing-based broker Digital China, which it recently named a "Partner of the Year."
Digital China is involved in some major surveillance efforts in China, including a Beijing police project that uses "localized" Oracle technology. 3/
Digital China is involved in some major surveillance efforts in China, including a Beijing police project that uses "localized" Oracle technology. 3/

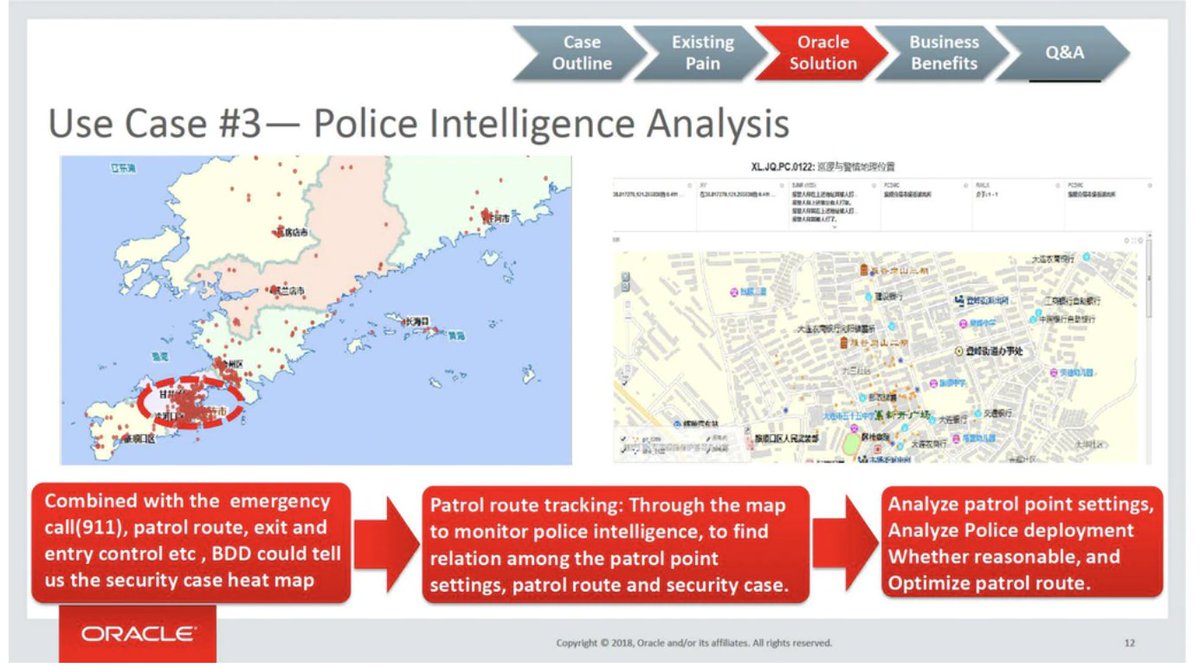
Documents from March 2021 show that Beijing police are buying a powerful server for a Police Cloud project.
Manufactured by a Digital China subsidiary, the server closely resembles Oracle's Exadata machine.
Here is @hrw on Police Cloud 4/
hrw.org/news/2017/11/1…
Manufactured by a Digital China subsidiary, the server closely resembles Oracle's Exadata machine.
Here is @hrw on Police Cloud 4/
hrw.org/news/2017/11/1…

So a "localized" Oracle server will be a major component of a project whose goals include:
- automated license plate recognition
- flagging of cars entering Beijing for the first time
- facial recognition of people *inside their vehicles* 5/
theintercept.com/2021/04/22/ora…
- automated license plate recognition
- flagging of cars entering Beijing for the first time
- facial recognition of people *inside their vehicles* 5/
theintercept.com/2021/04/22/ora…
Foreign tech companies including AWS, IBM, and Microsoft work with brokers in China. These relationships deserve more scrutiny.
But in Oracle's case, the brokers advertise Oracle-compatible "solutions" for data-driven policing platforms *on Oracle.com.* 6/

But in Oracle's case, the brokers advertise Oracle-compatible "solutions" for data-driven policing platforms *on Oracle.com.* 6/
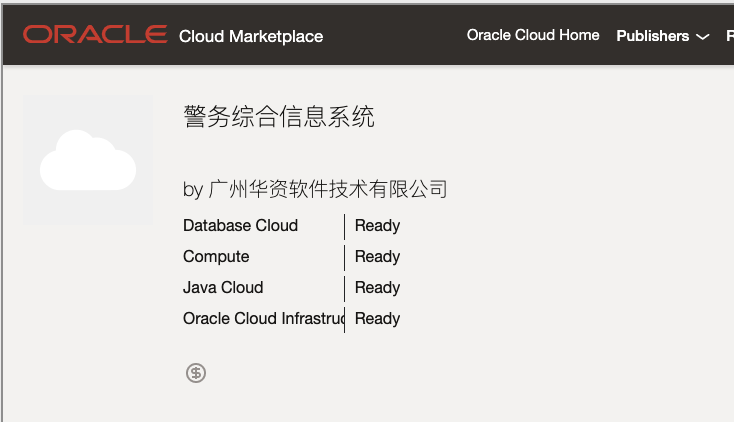
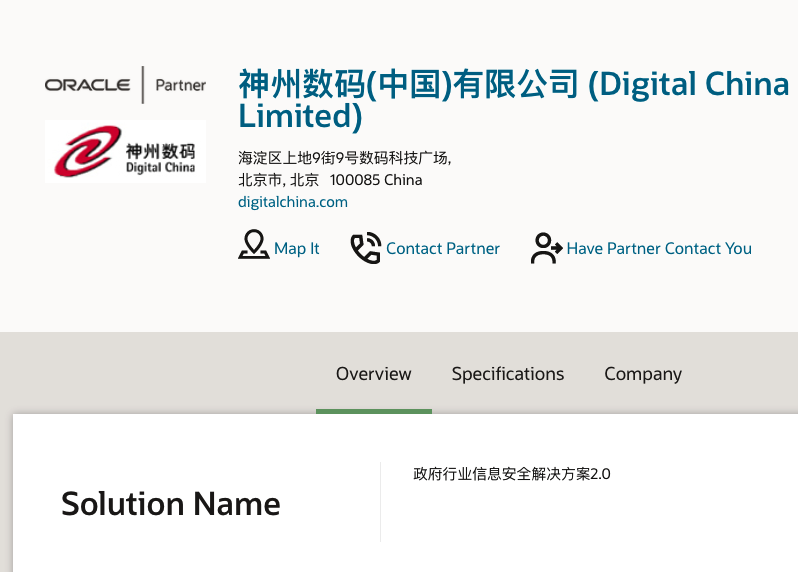
Oracle’s work with brokers illustrates the role that Western companies play in driving surveillance in China, even as they scale back their presence there. 7/ theintercept.com/2021/04/22/ora…
Oracle denies that its work with brokers in China is problematic. When I interviewed Oracle VP Ken Glueck, he told me, “We all have different definitions of what surveillance might be." 🧐
Here is more on Oracle's apparent definition 8/ theintercept.com/2021/04/22/ora…
Here is more on Oracle's apparent definition 8/ theintercept.com/2021/04/22/ora…
And in part 1 of this story, you can find the documents in which Oracle marketed its analytics software for police use in China - as well as in Brazil, Pakistan, Turkey, and the UAE. 9/
theintercept.com/2021/02/18/ora…
theintercept.com/2021/02/18/ora…
If you have worked with Oracle or have details about how its products are used in China or in security applications, ping me on Signal at +1 651-400-7987 or write me securely at marahv at protonmail. 10/
• • •
Missing some Tweet in this thread? You can try to
force a refresh