Looking for analysis on @POTUS' recent Executive Order on Improving the Nation's Cybersecurity? We've got you covered. THREAD 🧵
First, listen to @BobbyChesney and @CyberStatecraft director Trey Herr break it down on the @lawfareblog podcast. 1/4
lawfareblog.com/lawfare-podcas…
First, listen to @BobbyChesney and @CyberStatecraft director Trey Herr break it down on the @lawfareblog podcast. 1/4
lawfareblog.com/lawfare-podcas…
Second, we brought together @likethecoins, @NMAndersen, @wendynather, @_kate_stewart, @drdavidawheeler, and @WeldPond to mark up the executive order.
See their annotations throughout the text here. 2/4 atlanticcouncil.org/blogs/new-atla…
See their annotations throughout the text here. 2/4 atlanticcouncil.org/blogs/new-atla…
Third, check out @BobbyChesney and Trey Herr's article for @lawfareblog for an overview of the order and their core takeaways. 3/4
lawfareblog.com/everything-you…
lawfareblog.com/everything-you…
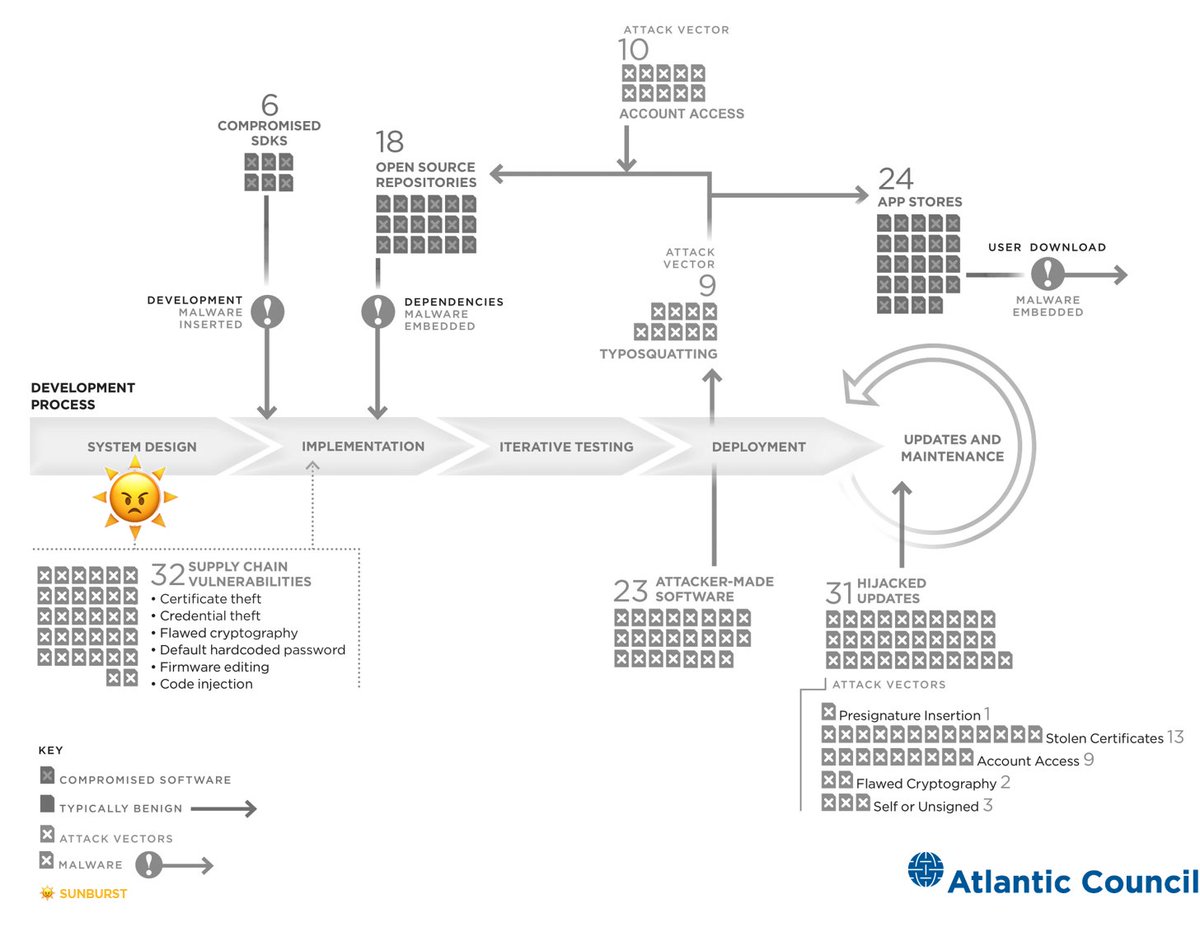
Finally, for more on the events that inspired the executive order, the state of US cyber strategy, and the work that lies ahead, see our report below.
Follow us at @CyberStatecraft for more, and join the conversation using #ACcyber. 4/4
atlanticcouncil.org/in-depth-resea…
Follow us at @CyberStatecraft for more, and join the conversation using #ACcyber. 4/4
atlanticcouncil.org/in-depth-resea…
• • •
Missing some Tweet in this thread? You can try to
force a refresh