A longish thread on Van Buren: Where does it leave the CFAA?
Here's a first cut.
Here's a first cut.
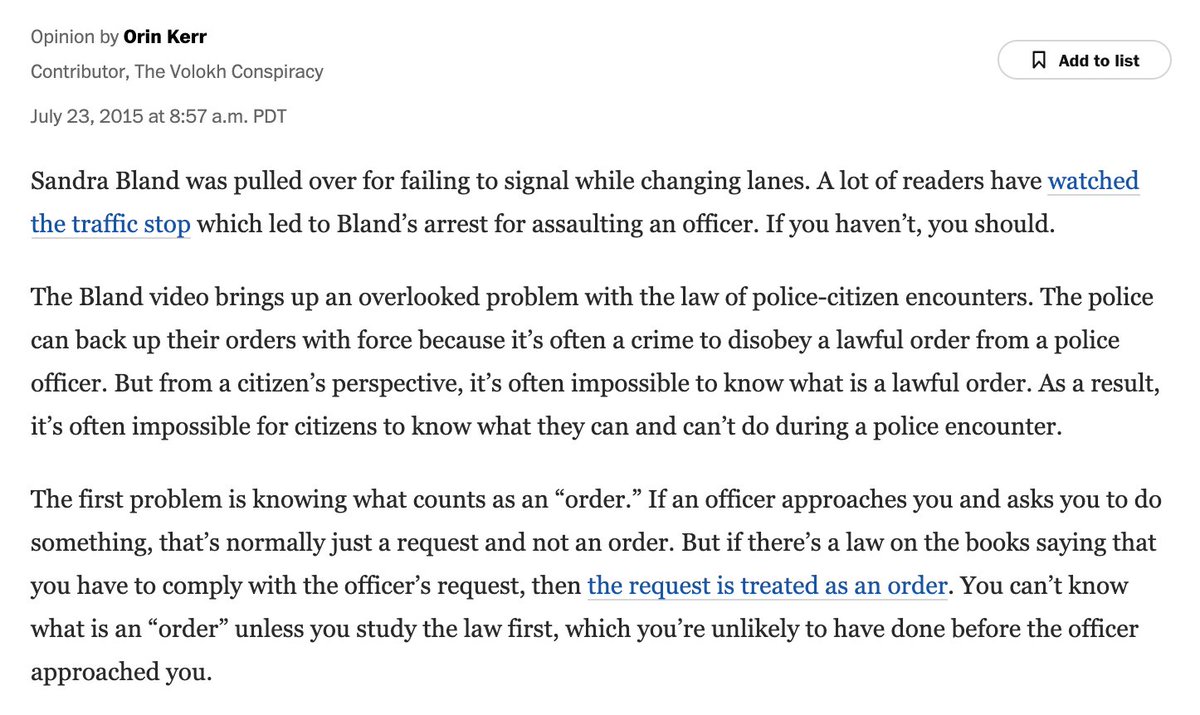
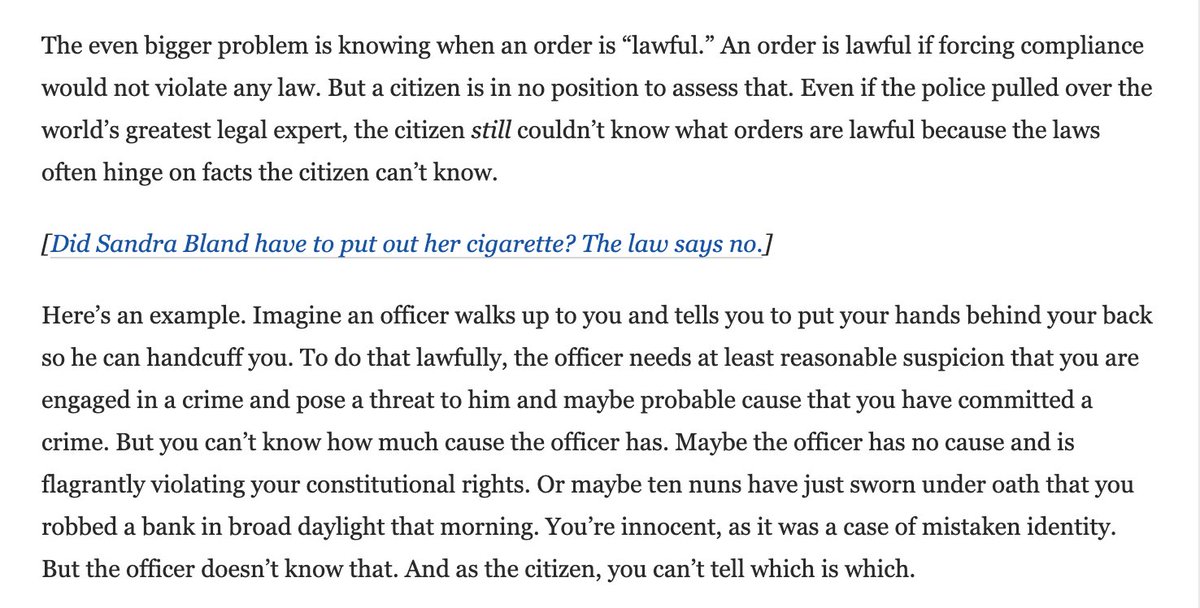
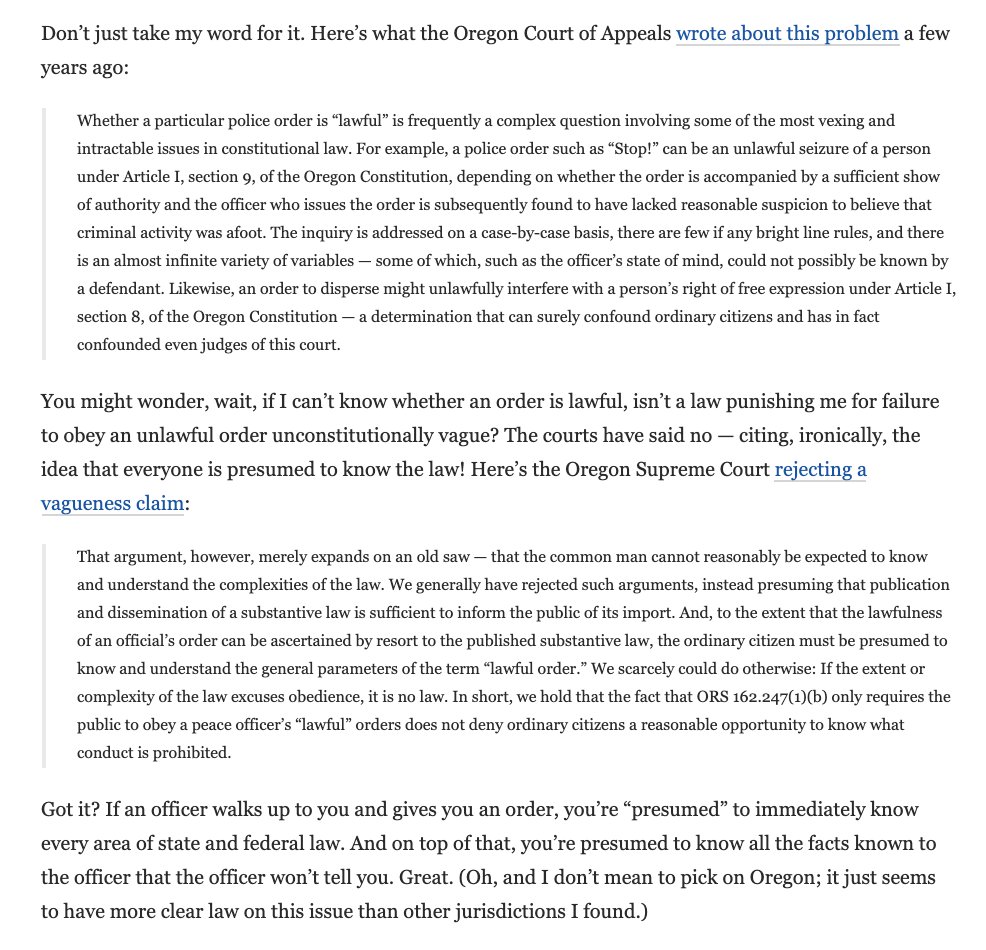
The computer hacking statute, the CFAA, prohibits two things: access without authorization, and exceeds authorized access. Access without authorization is understood to require some kind of breaking in. The question here is whether exceeds authorized access does, too.
As I read the new decision, the Court says yes -- exceeding authorized access also requires some breaking in. The court agrees with the defendant's claim that the two prohibitions are similar -- at just different stages. The Court calls this a "gates-up-or-down" inquiry. 

In a footnote, the Court seems to adopt the authentication test -- "whether a user’s credentials allow him to proceed past a computer’s access gate" -- that I and others have proposed. 
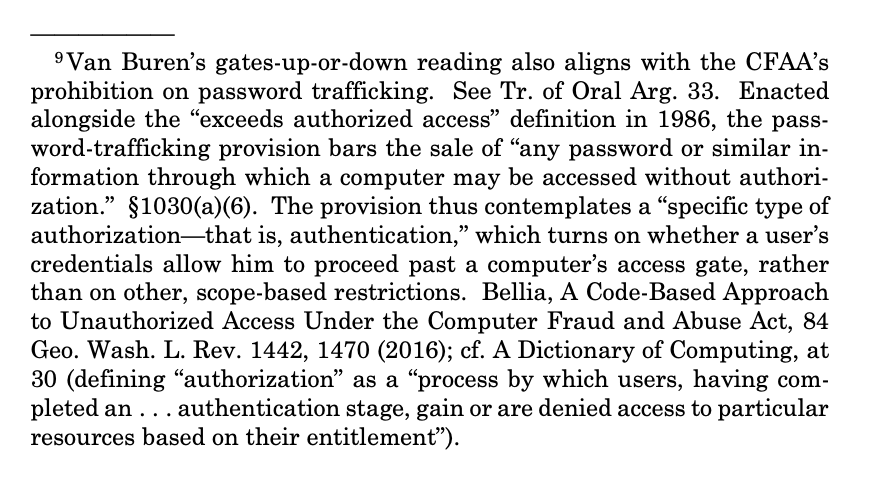
But there's a big caveat to that. In a different footnote, the Court says it is *not* reaching whether that "gate" can be imposed only by technology, or by a contract or policy. 

I am not sure how to square those footnotes.
I may be too close to this to see it clearly right now, but I would have thought the issue in Van Buren is what counts as a "gate." Does there need to be a technological gate, or can a gate of words ("do not access this computer for a bad purpose") suffice?
Reading Van Buren other than FN8 seems to point consistently to the idea that "gates up or down" means "access is blocked or not blocked," that is, a technological block. Put another way, it's all about actual hacking. 



(With apologies to the computer science folks who insist that the word "hacking" is misused by everyone, here the word is understood as meaning to break in.)
So this seems a little confusing, at least on my first read. It seems that the opinion other than FN8 is a rejection of the view that FN8 says the opinion is not resolving.
Putting a former clerk hat on, I wouldn't be entirely surprised if FN8 was added in response to another Justice who worried that the opinion was taking on more than it needed to.
Van Buren's brief at times alternated between a narrow and broad position -- at times narrowly arguing about "improper purpose," and at times more broadly arguing about technologically breaking in.
Van Buren ended up 6-3 and took a long time (argued 11/30, handed down 6/3). This is all just outside speculation, but it may be that the delay was caused by a Justice or 2 wanting a somewhat narrower ruling than Barrett's initial draft, which other than FN8 seems quite broad.
Anyway, that's how it seems to me at first blush. Curious if others have a different reaction. /end
Pondering this a bit more, I wonder if I was over-reading FN8. It leaves unresolved whether the gate test is “only” technological, or also “looks to” policies, terms, etc. That might still mean a mostly technological test, but one that can be impacted by written restrictions. 

For example, what if there’s a password gate, but the company has posted the PW and has a policy that anyone can use it? You could say that’s a case where the policy alters the gate; it’s not closed gate if they post the key and invite use.
That interpretation could reconcile the various footnotes, at least. Maybe FN8 is just saying that breaching a code-based barrier is not necessarily sufficient to establish liability — not that it is not required.
• • •
Missing some Tweet in this thread? You can try to
force a refresh