
The last bit of @devseccon is ongoing, go join! #DSC24
Or, just watch this 🎥or read this 🧵from my talk with @csoandy. We tell war stories of 5 watershed security incidents: FluffyBunny, Operation Aurora, DigiNotar, NotPetya and SolarWinds.
Or, just watch this 🎥or read this 🧵from my talk with @csoandy. We tell war stories of 5 watershed security incidents: FluffyBunny, Operation Aurora, DigiNotar, NotPetya and SolarWinds.
These are just some of incidents that inspired us to build @getBastionZero, which eliminates single points of compromise while providing zero-trust remote access to servers, containers and clusters. 2/x
bastionzero.com
bastionzero.com

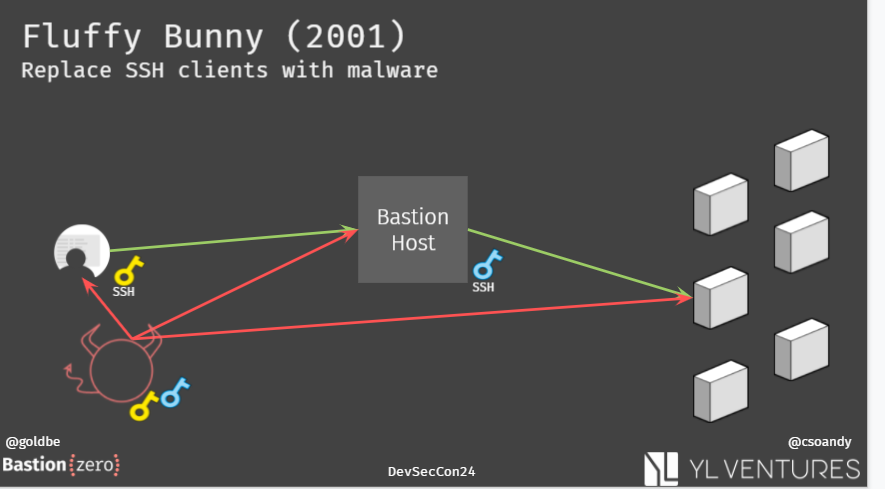
We start with FluffyBunny.
The attacker overwrote SSH clients with malware. And the malware steals SSH keys. And this was in 2001!
🧐This is classic example illustrates why standing credentials are bad. Because if stolen today, they can be used to attack in the future! 3/x
The attacker overwrote SSH clients with malware. And the malware steals SSH keys. And this was in 2001!
🧐This is classic example illustrates why standing credentials are bad. Because if stolen today, they can be used to attack in the future! 3/x
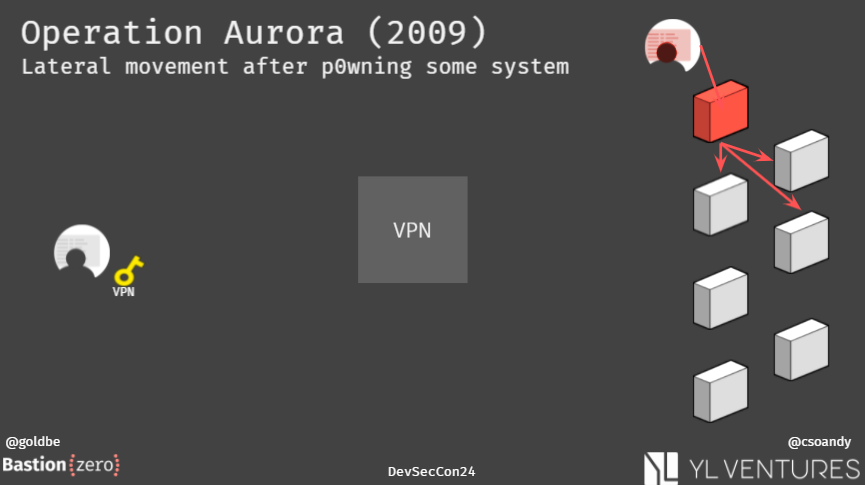
Next, we have Operation Aurora from 2009.
The attacker compromises one machine, and then moves laterally to p0wn the whole network.
What do we learn?
🧐Segment your infrastructure!
🧐Don't trust someone just because they are behind the VPN! 4/x
The attacker compromises one machine, and then moves laterally to p0wn the whole network.
What do we learn?
🧐Segment your infrastructure!
🧐Don't trust someone just because they are behind the VPN! 4/x
Next up is Diginotar, from 2011.
The attacker stole the Certificate Authority key from Diginotar, and started issuing fraudulent TLS certificates for Google and others.
This was a watershed moment for TLS security. 5/x
The attacker stole the Certificate Authority key from Diginotar, and started issuing fraudulent TLS certificates for Google and others.
This was a watershed moment for TLS security. 5/x

After Diginotar, the TLS ecosystem changed.
Certificate Authorities (CAs) were no longer trusted blindly. Technologies like Certificate Transparency were deployed.
All of this was done to limit the risk of CAs as a single point of compromise. 6/
Certificate Authorities (CAs) were no longer trusted blindly. Technologies like Certificate Transparency were deployed.
All of this was done to limit the risk of CAs as a single point of compromise. 6/

Interestingly, even today, ten years after Diginotar, there are tools for zero-trust remote access to infrastructure that rely on Certificate Authorities (CAs).
These CAS are a single point of compromise. 7/
These CAS are a single point of compromise. 7/
The Diginotar incident was very inspiring to us at @getBastionZero.
We set out to learn the lessons from Diginotar, and build a tool that provides simple remote access to infrastruture without relying on a single CA that can get hacked. 8/
We set out to learn the lessons from Diginotar, and build a tool that provides simple remote access to infrastruture without relying on a single CA that can get hacked. 8/

Next up is NotPetya from 2017.
The ransomware compromised your machine if it visited the site of a hacked Ukrainian tax software.
Then, one the machine was compromised, it stole the AD admin credentials for your domain. 8/
The ransomware compromised your machine if it visited the site of a hacked Ukrainian tax software.
Then, one the machine was compromised, it stole the AD admin credentials for your domain. 8/

NotPetya exploited the fact that AD admin creds are usually reused across multiple machines.
So once the attacker stole the AD admin creds from one machine, it could log in as admin on many others.
And that move laterally through your infrastructure. 9/
So once the attacker stole the AD admin creds from one machine, it could log in as admin on many others.
And that move laterally through your infrastructure. 9/
What do we learn from NotPetya?
🧐 Don't use standing credentials.
🧐 Don't use the *same* standing credentials across all of your infrastructure.
And...
🧐 Definitely don't this with admin credentials. 10/
🧐 Don't use standing credentials.
🧐 Don't use the *same* standing credentials across all of your infrastructure.
And...
🧐 Definitely don't this with admin credentials. 10/

Finally, we have SolarWinds, from late 2020.
To me, SolarWinds is super interesting, because it demonstrates some of the risks from the recent mass-movement to Single Sign On (SSO).
On one hand, SSO is great, because it eliminates standing credentials. 11/
To me, SolarWinds is super interesting, because it demonstrates some of the risks from the recent mass-movement to Single Sign On (SSO).
On one hand, SSO is great, because it eliminates standing credentials. 11/

So, SSO eliminates standing credentials. Good! We learned our lesson from NotPetya and FluffyBunny!
And so, many modern zero-trust systems use SSO to control access.
What SolarWinds teaches us is: not so fast, folks. 12/
And so, many modern zero-trust systems use SSO to control access.
What SolarWinds teaches us is: not so fast, folks. 12/

In the SolarWinds incident, the attacker stole the SSO key.
So, in many way, SolarWinds is the modern day (2020) equivalent of the Diginotar incident (2021), where there is an overpowered authority whose keys get stolen. 13/
So, in many way, SolarWinds is the modern day (2020) equivalent of the Diginotar incident (2021), where there is an overpowered authority whose keys get stolen. 13/

What do we learn from SolarWinds?
🧐Don't rely on a single root of trust that could get compromised!
SolarWinds is another key incident that inspired our design of @getBastionZero.
BastionZero uses two independent roots of trust to control access to your infrastructure. 14/
🧐Don't rely on a single root of trust that could get compromised!
SolarWinds is another key incident that inspired our design of @getBastionZero.
BastionZero uses two independent roots of trust to control access to your infrastructure. 14/

DM me on twitter or ping me on the #DSC24 slack if you'd see how BastionZero provides:
✨ Zero-trust remote access to cloud resources
✨ Eliminates single points of compromise
✨ Provides visibility into what your engineers are doing in your infrastructure.
That's it! 15/15
✨ Zero-trust remote access to cloud resources
✨ Eliminates single points of compromise
✨ Provides visibility into what your engineers are doing in your infrastructure.
That's it! 15/15
@threadreaderapp unroll please
• • •
Missing some Tweet in this thread? You can try to
force a refresh





