Here we go!
(For those of you at home, NDSS is one of the "big four" top-tier academic cybersecurity conferences.)
<thread>

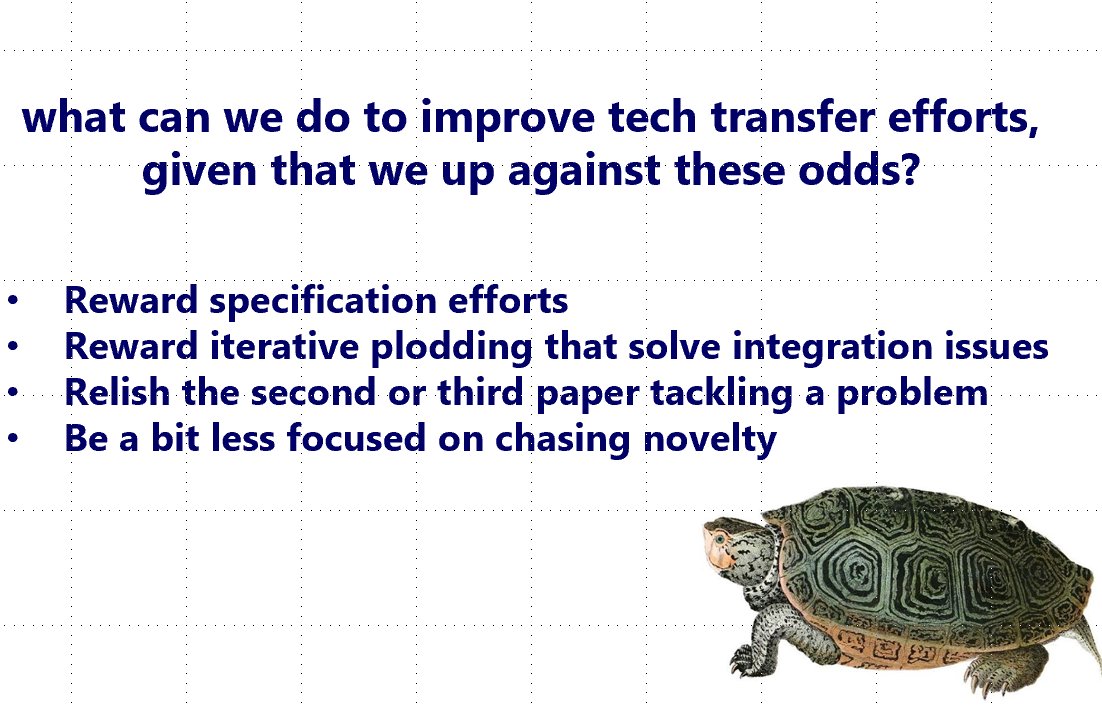
How can we align incentives in the academic community, to encourage researchers to design systems that actually get used in the real world?
This is a key question in 2020, where infosec is everywhere.
eprint.iacr.org/2017/099
As part of this work, we developed a spec for a verifiable random function (VRF).
Due to challenges related to integration, we didn't get very far with the work on DNSSEC.
But our VRF work took off!
datatracker.ietf.org/doc/draft-irtf…

Here's the paper: eprint.iacr.org/2017/099.pdf
Here's the spec: datatracker.ietf.org/doc/draft-irtf…
I think academics need to give more credence to specification.
✅zone enumeration is feature, not a bug [RFC8198]
✅supports dynamic computation of DNSSEC responses
So, basically the opposite of what we optimized for.
This made NSEC5 adoption harder. Since the system is essentially a moving target.
eprint.iacr.org/2018/057.pdf
This work solves a simple problem. What if the keys to your crypto system are maliciously chosen?
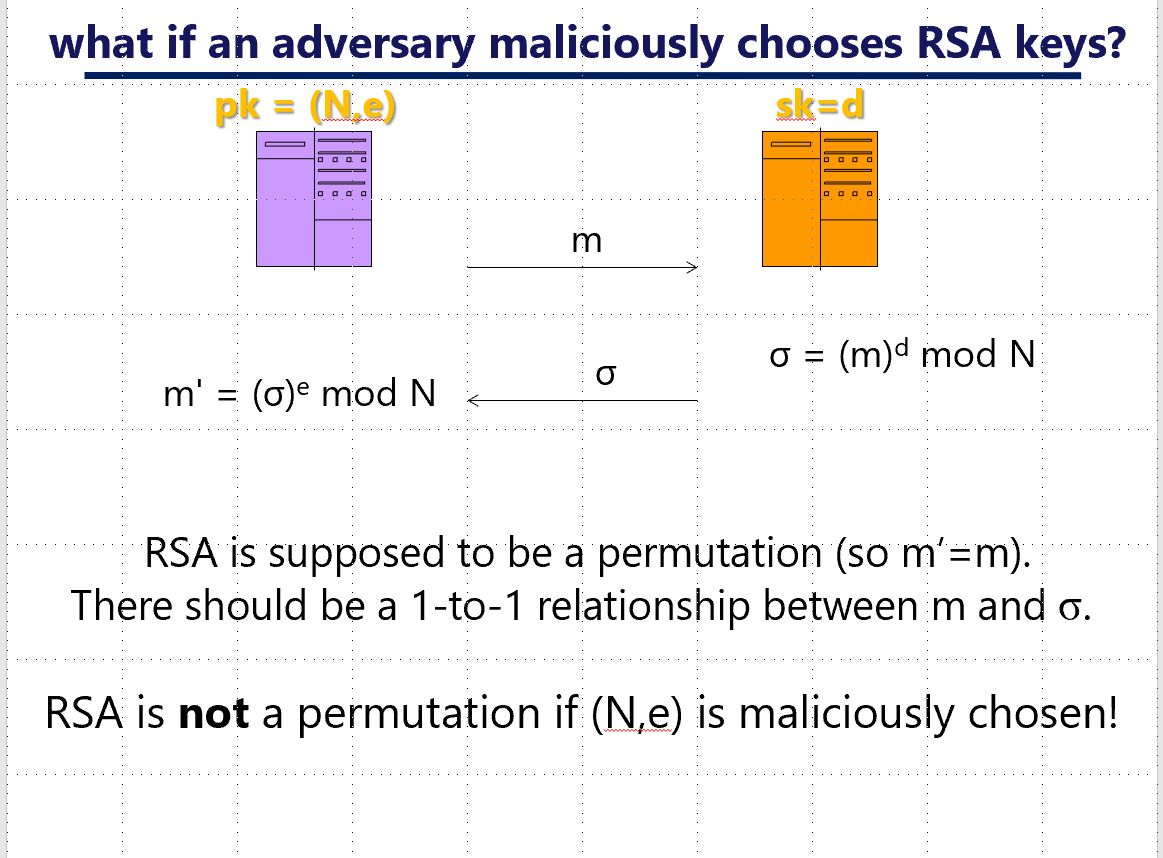
Send a short "certification" that the public key was correctly chosen, along with the public key.
Check the certification once, and you know your public key is good!
Our scheme works for RSA and Pallier, and was adopted by @UnboundTech_ & @ZenGo.
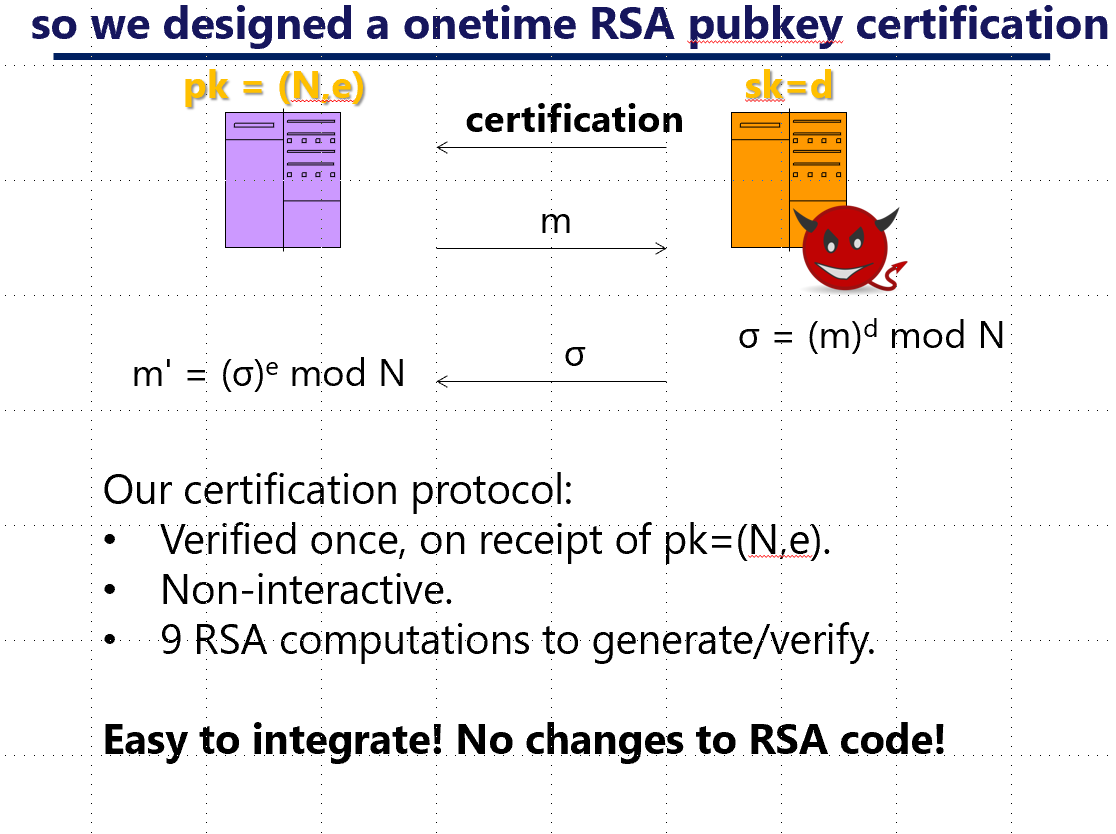
Well, apart from being secure and efficient, our scheme is
✅ specified, and
✅easy to integrate (just add our certification to your pubkey - with no other changes to your cryptosystem!)
Easy. And it works.
I talked about this at IETF'102 at ANRW'18.
You can watch the talk here!
I hope I convinced you to think about quality of specification and ease of integration when you are next reviewing an academic infosec paper!
Thanks for listening!👩🏫
</thread>