This is very important!
If you have the "Print Spooler" service enabled (which is the default), any remote authenticated user can execute code as SYSTEM on the domain controller.
Stop and Disable the service on any DC now!



If you have the "Print Spooler" service enabled (which is the default), any remote authenticated user can execute code as SYSTEM on the domain controller.
Stop and Disable the service on any DC now!
https://twitter.com/gentilkiwi/status/1410066827590447108

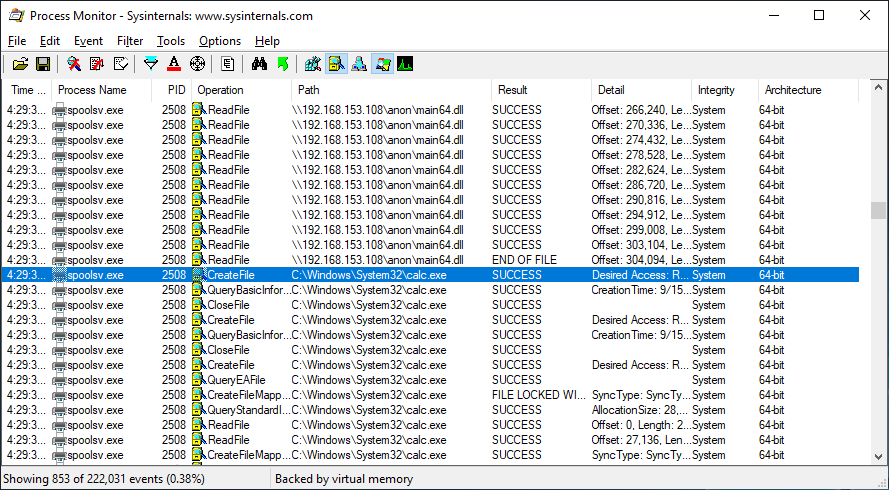

Log entries in Microsoft-Windows-PrintService/Admin might be a good place to look for evidence of exploitation.
Here, despite the "failed to load" error, is what was generated when I loaded main64.dll off of a remote SMB share using this exploit.
Here, despite the "failed to load" error, is what was generated when I loaded main64.dll off of a remote SMB share using this exploit.

Note that looking for this will only find lazy attackers. The only reason that I saw this in my initial test is because the main64.dll that I used made no attempt to look like what the print spooler is looking for.
If the attacker loads a sane-looking DLL, no error is logged.
If the attacker loads a sane-looking DLL, no error is logged.

For example, here's the result of using a "real" printer driver DLL that just happens to have the value-add of launching calc.exe
No warnings or errors in Windows Event viewer
No warnings or errors in Windows Event viewer

I've published a vulnerability note on this. I suspect that Microsoft will need to issue a new CVE to capture what PrintNightmare exploits, as it sure isn't what Microsoft patched as CVE-2021-1675.
kb.cert.org/vuls/id/383432
kb.cert.org/vuls/id/383432
Microsoft has published an advisory on the and has called it CVE-2021-34527
msrc.microsoft.com/update-guide/v…
msrc.microsoft.com/update-guide/v…
• • •
Missing some Tweet in this thread? You can try to
force a refresh