
We would like to thank everyone for the overwhelming response to the #PegasusProject . Today, we reflect on forensic & technical research conducted by @amnesty’s Security Lab that has helped expose the enormous scales of abuse linked to NSO Group’s Pegasus spyware. Thread 1/13 

@amnesty We @amnesty began our research on NSO Group back in 2018, when one of our own staff members was targeted with this invasive spyware tool. The research also identified a Saudi activist was targeted in the same attacks. Read more: amnesty.org/en/latest/rese… 2/13
@amnesty The Security Lab next found tell-tell Pegasus SMS messages on the phone of a well-known activist. We also found a new attack technique that was not seen before. Network injection attacks were being used to send targets to Pegasus exploit websites amnesty.org/en/latest/rese… 3/13
@amnesty NSO Group spyware no longer needed to trick users with a phishing link. Attacks against journalists and activists were becoming even harder to detect. To respond, the Security Lab needed to develop a set of forensics tools to deeply analyze phones for traces of these attacks 4/13
@amnesty These tools were key to finding traces of Pegasus on phones of journalists, activists, and civil society around the world as part of the #PegasusProject . Working closely with @ForbiddenStories and our journalist partners, 67 devices were forensically analyzed. 5/13 
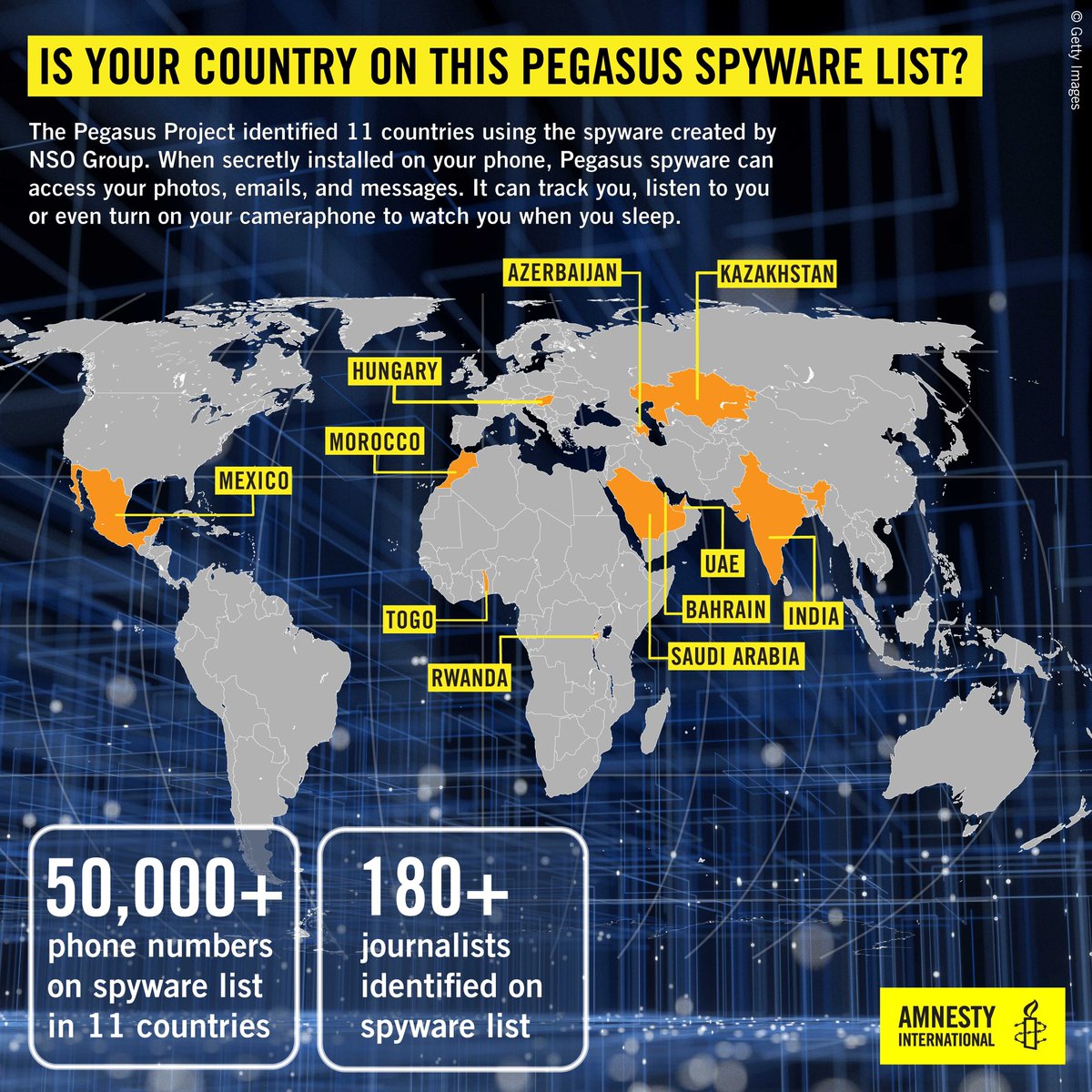
@amnesty The findings were shocking. Dozens of the devices we analyzed showed traces of Pegasus. These were not only historical attacks either. Even the latest iPhone 12 devices with the latest security patches were being compromised with zero-click attacks up to this month. 6/13
@amnesty The Security Lab analyzed a sample of 67 devices from potential targets in #PegasusProject list. Some devices had since been replaced (or were Android). From the 33 iPhones which still contained data from the time of targeting, we found definite traces of Pegasus on 26. 7/13
@amnesty More than 75% of the non-replaced iPhones showed traces of Pegasus. These results show that the #PegasusProject data is clearly linked to NSO Group’s Pegasus product and their clients’ targets. Full forensic traces at: amnesty.org/en/latest/rese… 8/13
@amnesty Significantly, as reported in the @Guardian, @lemondefr, and the @WashingtonPost, in many cases forensic traces of Pegasus targeting were found on devices just seconds or minutes after the phone appeared in the #PegasusProject data. 9/13
@amnesty @guardian @lemondefr @washingtonpost Our forensics analysis were peer-reviewed by researchers at @CitizenLab who confirmed our findings in a representative sample of targeted devices. Citizen Lab also confirmed that the overall forensic methodology used in this research was “sound”. citizenlab.ca/2021/07/amnest… 10/13
@amnesty @guardian @lemondefr @washingtonpost @citizenlab Amnesty International adheres to incredibly rigorous and evidence-based research methods. We believe in sharing our knowledge with the communities with which we work. That is why we have released our mobile forensics tool MVT as open-source software. github.com/mvt-project/mvt 11/13
@amnesty @guardian @lemondefr @washingtonpost @citizenlab We have also published a comprehensive set of Pegasus indicators of compromise which can be used with MVT to check for signs of targeting or compromise with the Pegasus spyware. You can find a good walkthrough about using MVT at techcrunch.com/2021/07/19/too… 12/13
@amnesty @guardian @lemondefr @washingtonpost @citizenlab Together with partners at @FbdnStories and the #PegasusProject Amnesty has been privileged to shine a light on the human rights abuses linked to the spyware industry. Now is the time to end the unlawful targeted surveillance of human rights defenders amnesty.org/en/get-involve… 13/13
• • •
Missing some Tweet in this thread? You can try to
force a refresh



