
Just recieved what looks a lot like a phishing email, suggesting I am now registered for a COVID test on August 12
Uses the branding of a legit medical facility (in roughly my geo area), from a gmail account with the facility’s legit info@ as the reply-to
Let’s investigate ⬇️
Uses the branding of a legit medical facility (in roughly my geo area), from a gmail account with the facility’s legit info@ as the reply-to
Let’s investigate ⬇️
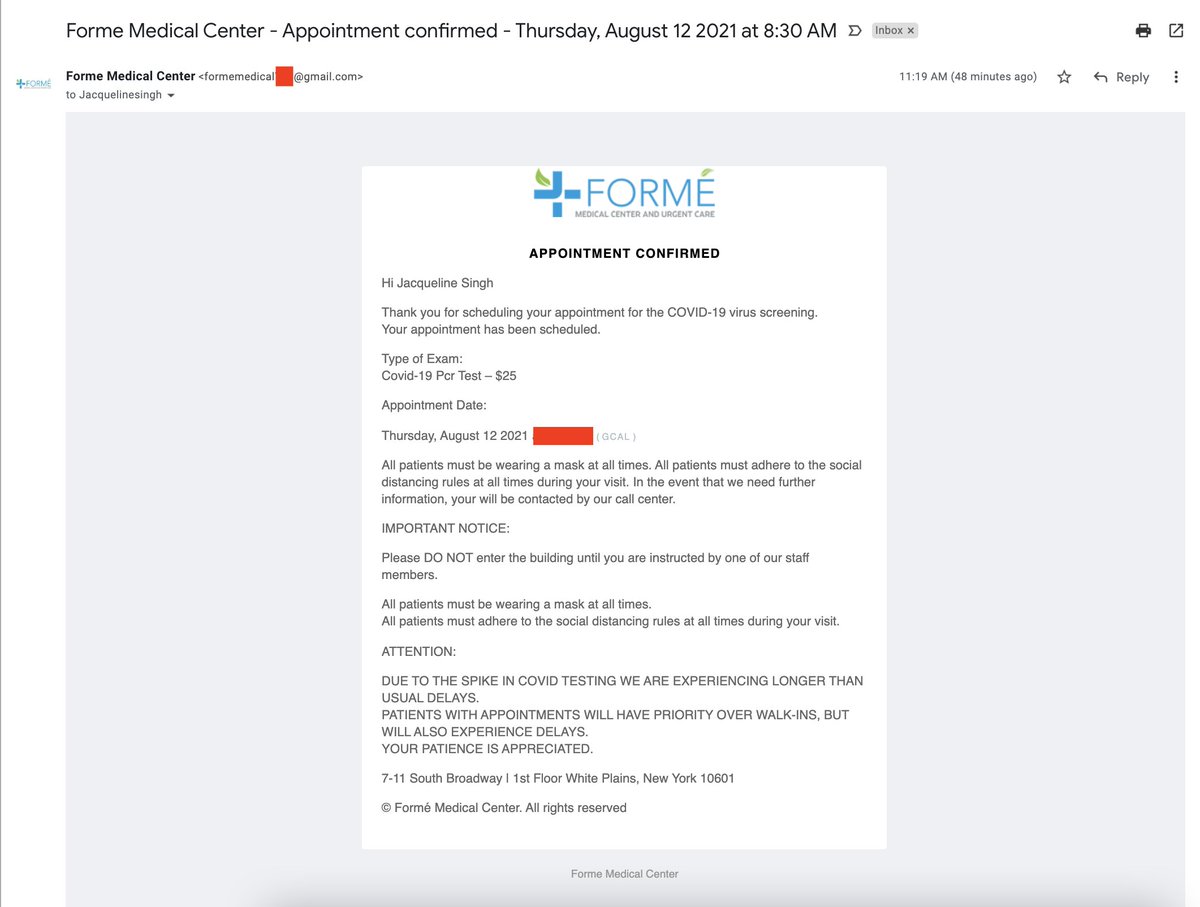
Here's the email. Pretty convincing, right? I have removed a couple of details for OPSEC purposes.
But is there anything particularly sinister about this email? Did it include a tracking pixel? Any bad links?

But is there anything particularly sinister about this email? Did it include a tracking pixel? Any bad links?

Let's download the message as an .eml file from Gmail. We do this directly from the message's context menu.
This will provide us the complete headers and allow us to further analyze the message.

This will provide us the complete headers and allow us to further analyze the message.


Well .eml files are quite technical and verbose.
They can be a bit tedious to parse visually. Here's what they look like inside using a text editor:
They can be a bit tedious to parse visually. Here's what they look like inside using a text editor:

Since .eml files follow a set format, let's install a tool to help us understand the contents.
h/t @ninoseki for this awesome dockerized tool!
github.com/ninoseki/eml_a…
h/t @ninoseki for this awesome dockerized tool!
github.com/ninoseki/eml_a…
@ninoseki Once you've got docker installed, you can use that repository to install the application, which will set up a listener on port 8000. 



Once the application is running, you can browse to http://localhost:8000 and drop that .eml file right in. 

I'm going to interrupt this thread to notify all infosec and DFIR people that this thread isn't really for them
If you're experienced in this area, this thread isn't for you. It's a basic primer. Less than 101. Thanks.
If you're experienced in this area, this thread isn't for you. It's a basic primer. Less than 101. Thanks.
What we learn here is not that the email is "safe", but that it does not bear certain markers associated with spammers and scammers.
Also, saying there are no suspicious OLE object in the attachments is helpful, as OLE is often used in malicious Microsoft Office and RTF files
Also, saying there are no suspicious OLE object in the attachments is helpful, as OLE is often used in malicious Microsoft Office and RTF files

We can often rely on SPF/DKIM/DMARC, which are important security technologies for email which help validate that the email was legitimately sent from the infrastructure it claims to have been sent from.
However, many organizations have not bothered to configure this.
However, many organizations have not bothered to configure this.

In the case of Google, failing to pass certain checks as a sender will result in your email landing in SPAM instead of the intended recipient's inbox.
Here is an overview to help you understand these technologies and how they work together.
csoonline.com/article/325423…
Here is an overview to help you understand these technologies and how they work together.
csoonline.com/article/325423…
Once we get past the header section of the .eml analyzer, we arrive at the content of the message.
We can now individually evaluate the IOCs, or Indicators of Compromise, which could potentially be malicious.
> URLs
> Domain Names
> IP Addresses
> Email Addresses
We can now individually evaluate the IOCs, or Indicators of Compromise, which could potentially be malicious.
> URLs
> Domain Names
> IP Addresses
> Email Addresses

When analyzing a domain for malicious content, never browse to a domain you don't know from your own "naked" browser.
Instead, you can use Startpage's IXQuick Proxy ("anonymous view"). This can limit the site's ability to harm you. Some features on the target site may not work.
Instead, you can use Startpage's IXQuick Proxy ("anonymous view"). This can limit the site's ability to harm you. Some features on the target site may not work.

A safer way to protect your own system while browsing to potentially malicious websites is to use a "sandboxing" environment.
A simple and cheap/free way to set up a sandbox is to install VMWare Player, then install a virtual machine.
vmware.com/products/works…
A simple and cheap/free way to set up a sandbox is to install VMWare Player, then install a virtual machine.
vmware.com/products/works…
You can get a free 90-day license for Windows 10 which will work with VMWare Player.
developer.microsoft.com/en-us/microsof…
developer.microsoft.com/en-us/microsof…
The intent behind the VM is for you to conduct all potentially harmful research on that version of Windows, instead of your normal everyday host operating system.
For folks who want to learn more about Linux or hacking tools, Kali is but a download away.
kali.org/docs/virtualiz…
For folks who want to learn more about Linux or hacking tools, Kali is but a download away.
kali.org/docs/virtualiz…
Going back to the .eml analysis, we can see the tool has extracted two URLs and two domain names.
The first one appears to be legitimate, but how can we tell? Their website looks like a Wordpress template, and indeed it is!


The first one appears to be legitimate, but how can we tell? Their website looks like a Wordpress template, and indeed it is!

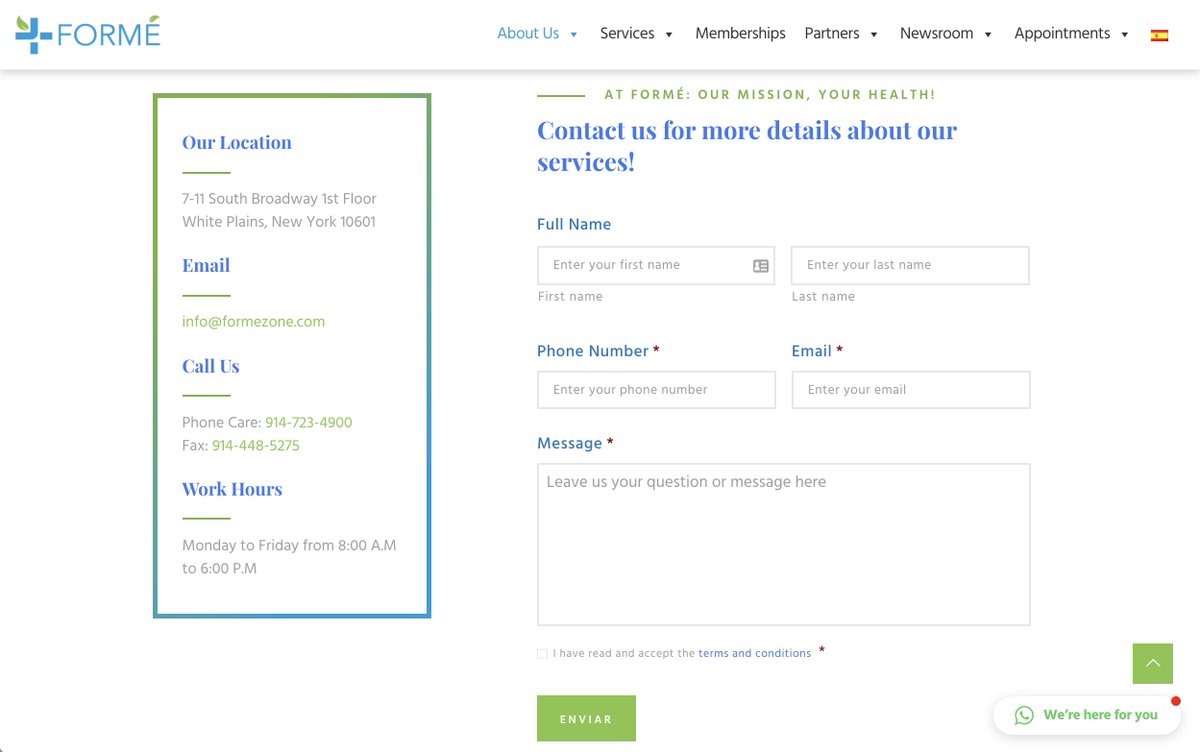

We're able to quickly identify that by right-click/viewing the source, as well as by navigating to the domain[.]com/wp-admin, which is the default URL for the admin page of Wordpress installations.
This is only relevant because threat actors also use popular web dev frameworks.
This is only relevant because threat actors also use popular web dev frameworks.
Indeed, many "phishing kits" which are sold on the "dark web" and hacker forums are packages which would allow a bad actor to deploy a phishing campaign without a lot of effort.
Here is some more info about how phishing kits work.
nortonlifelock.com/blogs/norton-l…
Here is some more info about how phishing kits work.
nortonlifelock.com/blogs/norton-l…
Calling the phone numbers, which are in the right area code, yields nothing but a recorded line and mailbox. They're supposedly closed on Sundays. So how else can we potentially determine these folks are legitimate?
Maybe we can look for other references to their website.
Maybe we can look for other references to their website.

Searching for the phone number led to a local news site which has previously featured this facility in the context of covid testing 
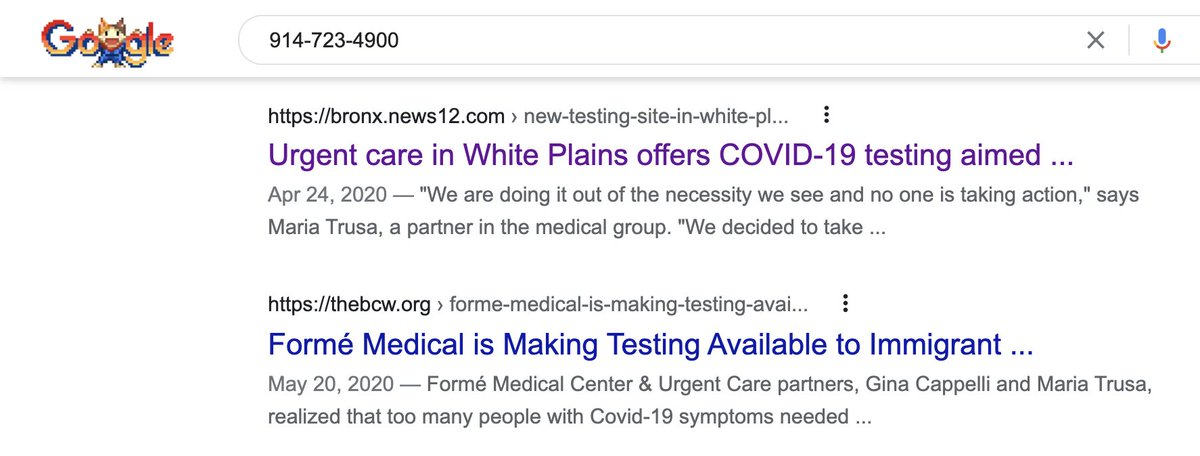
Also, a basic search also reveals aged Facebook, Instagram, Yelp, Nextdoor accounts...
These are all positive signs that while the site uses popular frameworks and looks a little wonky, it wasn't built anytime recently, which would be a red flag.
These are all positive signs that while the site uses popular frameworks and looks a little wonky, it wasn't built anytime recently, which would be a red flag.
In fact, by using a basic "whois" search, we are able to identify the domain was first registered in 2015.
This is another good sign, as many domains used for phishing are rapidly auto-generated, registered, and dropped. Domain age is often a significant indicator of badness.
This is another good sign, as many domains used for phishing are rapidly auto-generated, registered, and dropped. Domain age is often a significant indicator of badness.

It seems likely the domain is legit, yet we still have no explanation for why they are sending from a Gmail address.
A Google search for the address in quotes yields nothing. Perhaps this medical facility is doing some "shadow IT" by sending email from an off-domain account?
A Google search for the address in quotes yields nothing. Perhaps this medical facility is doing some "shadow IT" by sending email from an off-domain account?
The other domain we know exists is "formezone[.]com", since they added a reply-to for this address, meaning when you hit "reply" in your email client, "info@formezone[.]com" would be loaded in the To: field instead of the address that actually sent you the email.
The email is also listed on their website. The domain itself only hosts an "under construction" page.
Running a whois search on that domain and examining the registration details leads us directly to the web developer, who is local to the medical facility.
Running a whois search on that domain and examining the registration details leads us directly to the web developer, who is local to the medical facility.
An automated check we can run on the site is to pass it through URLScan. If you see a bunch of red text with a verdict of "potentially malicious", the site could still be legitimate, yet hacked and serving malware.
urlscan.io/result/dcbee5b…
urlscan.io/result/dcbee5b…
Now that we can conclude this site is likely legitimate (feel free to also check with VirusTotal), let's turn our focus to the other URL which was identified by the .eml analyzer as having been included in the email message.
It's a Google Calendar template link.
It's a Google Calendar template link.
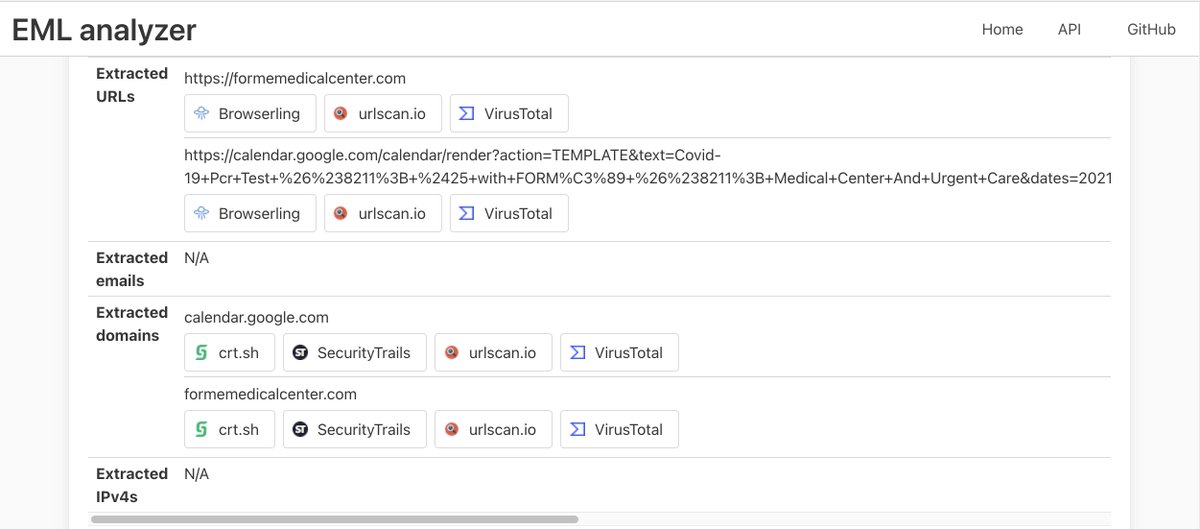
"Malformed" links are often used to cause a target application to behave in a way that is out of bounds with what the developer of the app intended, and are sometimes a way get into a system
Using an event link generator, we can easily see the link is not malformed, looks normal
Using an event link generator, we can easily see the link is not malformed, looks normal

Searching the body of the email for images (png, jpg, img, etc), I've found one single image being loaded from the website in a simple way; not a tracking pixel.
With this, you will still send your IP address to the website, but not in connection to a specific campaign
With this, you will still send your IP address to the website, but not in connection to a specific campaign

The way marketers get folks to "enable external images" these days is by adding so much visual content to the email, it becomes unreadable without loading the external images.
If you're concerned about tracking pixels, you would do best to never load any external images.
If you're concerned about tracking pixels, you would do best to never load any external images.

Here you can see an example of what it looks like to generate an email pixel and tracking URLs. Note the uniqueness of the image filename and domain URL. 
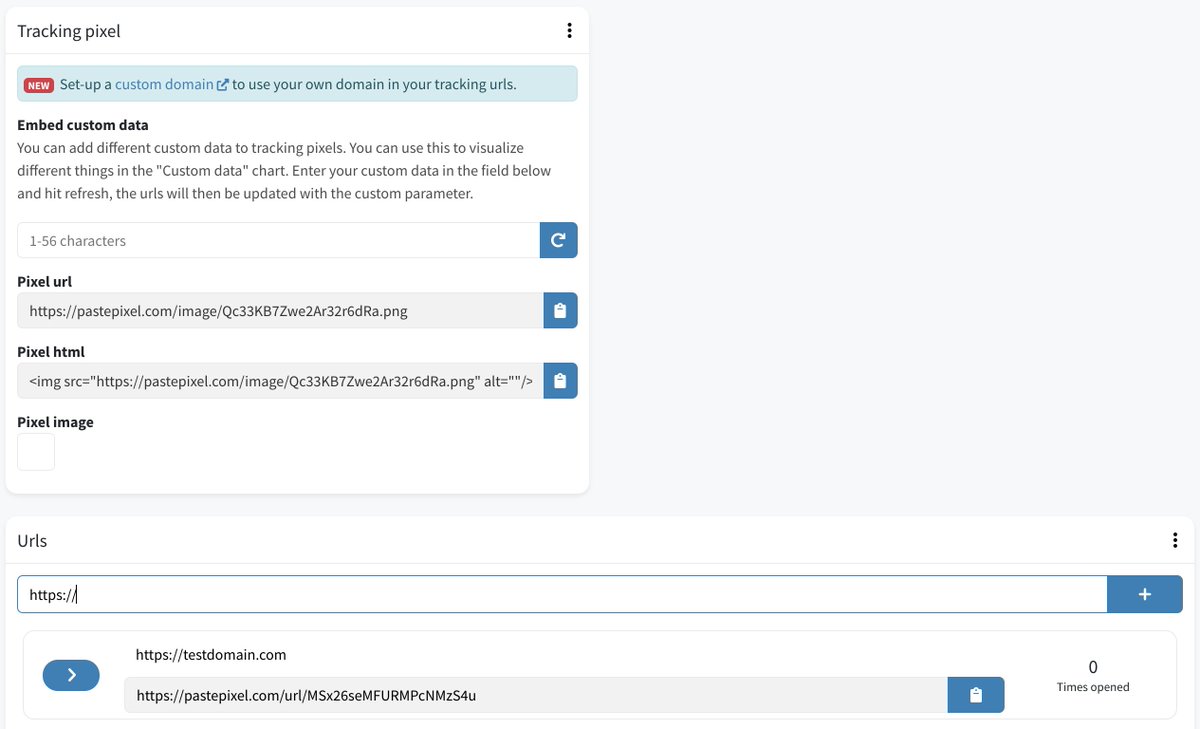
So we've legitimized the content of the email and the place it was sent from.
The only open question is why they're using a Gmail account and the answer is likely because it's somehow convenient for the sender!
In this case it appears someone mistakenly used my email address.
The only open question is why they're using a Gmail account and the answer is likely because it's somehow convenient for the sender!
In this case it appears someone mistakenly used my email address.
I thought I'd show you some of the mental steps used to review a message for signs of maliciousness.
I hope this was helpful for those of you who want to look deeper but not sure where to start.
Feel free to drop any questions you might have!
Cheers 🍻
I hope this was helpful for those of you who want to look deeper but not sure where to start.
Feel free to drop any questions you might have!
Cheers 🍻
One more tiny disclaimer — this is in no way the total spectrum of analysis which can be applied to an email message!
These are just a few of the basics which felt applicable to this email message in particular.
These are just a few of the basics which felt applicable to this email message in particular.
Update: the medical facility typo’ed my email when they sent the confirmation.
There is another Jacqueline Singh out here in NY, and she uses an email address which is essentially mine, but with numbers on the end. They forgot to include the numbers.
There is another Jacqueline Singh out here in NY, and she uses an email address which is essentially mine, but with numbers on the end. They forgot to include the numbers.
• • •
Missing some Tweet in this thread? You can try to
force a refresh











