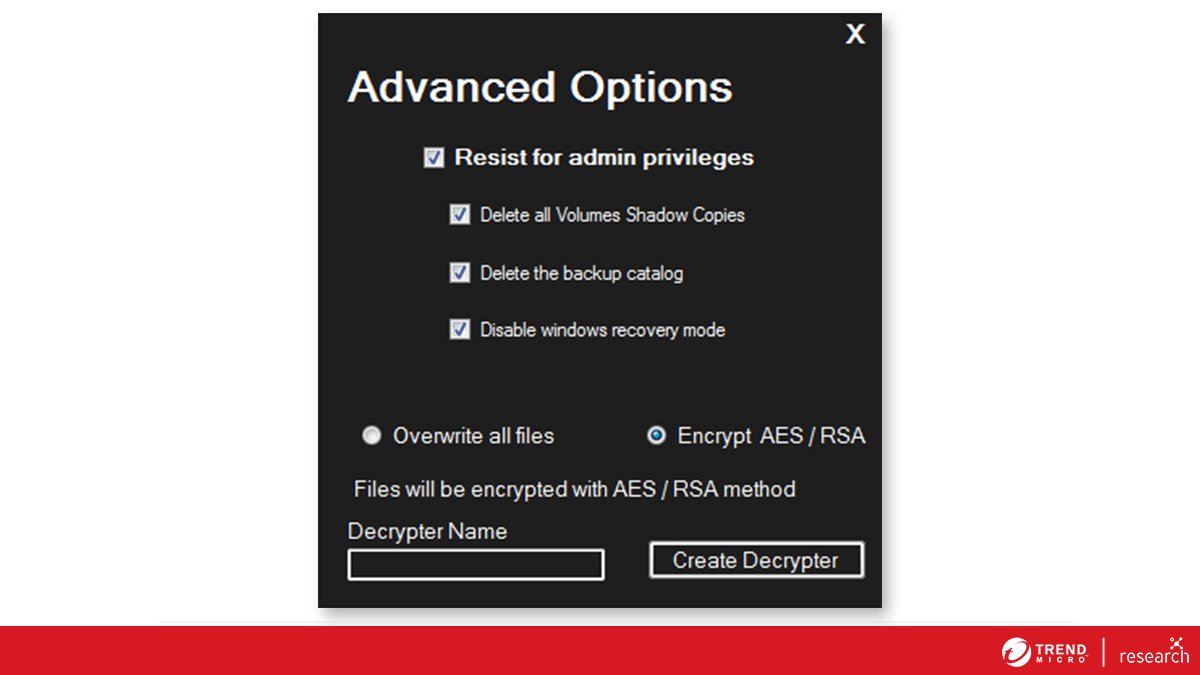
LATEST NEWS: Cring #ransomware recently made headlines due to a recent attack that exploited a bug in the 11-year-old version of the Adobe ColdFusion 9 software. Follow this thread and let’s look at the techniques typically wielded by this ransomware.
👇 👇 👇 [1/5]
👇 👇 👇 [1/5]

[2/5] #Cring ransomware gains initial access through unsecure remote desktop protocol (RDP) or through unpatched vulnerabilities. 

[3/5] The threat also abuses tools such as #Mimikatz for credential access and Cobalt Strike for lateral movement. More details on how these tools are abused for ransomware attacks:
research.trendmicro.com/3hYEMkT
research.trendmicro.com/3hYEMkT
[4/5] We detect Cring ransomware as Ransom.MSIL.CRYNG.A: trendmicro.com/vinfo/us/threa…
.
.
.
We also detect another variant of the ransomware as Ransom.Win32.CRING.C: trendmicro.com/vinfo/us/threa…
.
.
.
We also detect another variant of the ransomware as Ransom.Win32.CRING.C: trendmicro.com/vinfo/us/threa…
[5/5] To defend systems against ransomware, organizations must employ a proactive approach that involves patching vulnerabilities and monitoring systems for suspicious behavior:
research.trendmicro.com/3CFkll3
research.trendmicro.com/3CFkll3
• • •
Missing some Tweet in this thread? You can try to
force a refresh