
Did you ever want to know what Proof-of-Work is?
It's the consensus protocol behind Bitcoin and, according to some people, the sole reason for climate change due to its insane energy consumption.
Let's take a closer look at this consensus protocol.
A thread. ↓
It's the consensus protocol behind Bitcoin and, according to some people, the sole reason for climate change due to its insane energy consumption.
Let's take a closer look at this consensus protocol.
A thread. ↓
1. Basics
The Proof-Of-Work protocol creates a system in which one party (the prover) has to prove to one or multiple other parties (the verifiers) that they put in a certain amount of work for some purpose.
The Proof-Of-Work protocol creates a system in which one party (the prover) has to prove to one or multiple other parties (the verifiers) that they put in a certain amount of work for some purpose.
The prover's work is moderately hard to very hard, while the verifiers can pretty quickly check whether the proof is correct.
This creates an asymmetric system.
The original idea was to create protection against DDoS attacks and spam.
This creates an asymmetric system.
The original idea was to create protection against DDoS attacks and spam.
If someone sending a request to a service has to put in a lot of work to get an answer, it would be very costly to send many requests or require a disproportionate amount of hardware resources.
This creates certain security for such systems.
This creates certain security for such systems.
2. Variants
Two variants of Proof-Of-Work protocols exist:
1. Challenge-response
2. Solution-verification
Two variants of Proof-Of-Work protocols exist:
1. Challenge-response
2. Solution-verification
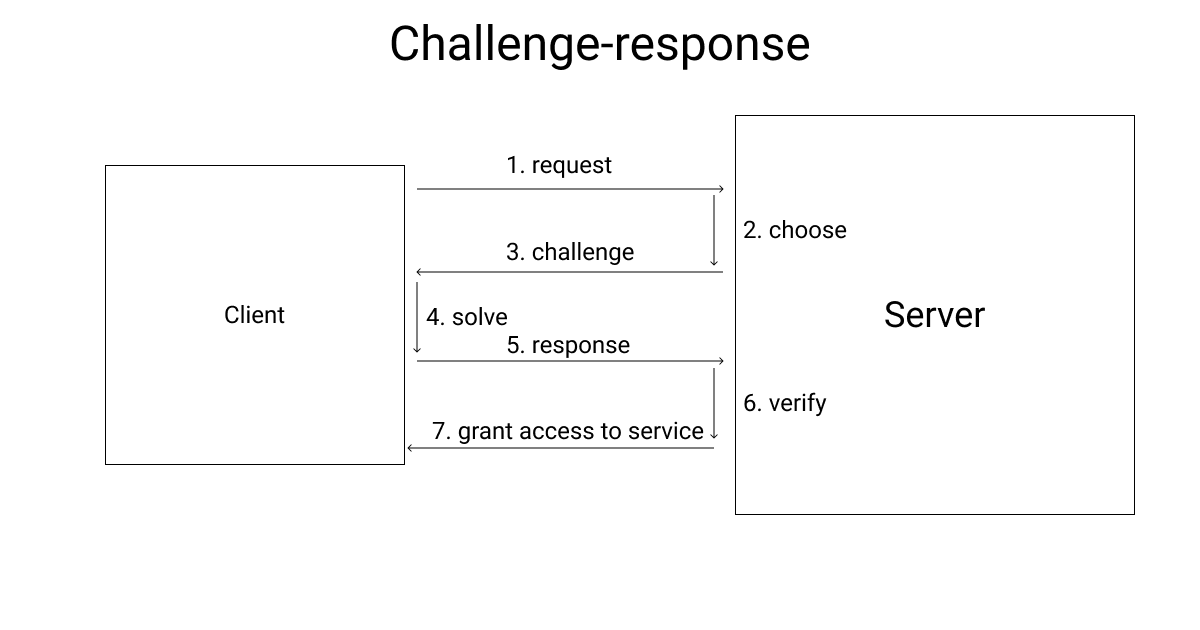
-> 1. Challenge-response
This variant can be used when a direct link between the prover and the verifier exists.
When the prover sends a request, the verifier chooses a problem to solve and asks the prover to do so.
This variant can be used when a direct link between the prover and the verifier exists.
When the prover sends a request, the verifier chooses a problem to solve and asks the prover to do so.
The prover then has to spend computing power to solve the problem and answer the verifier.
If the verification is successful, the prover gets access to the service. If not, access is denied, or whatever the prover sent is not accepted.
If the verification is successful, the prover gets access to the service. If not, access is denied, or whatever the prover sent is not accepted.
-> 2. Solution-verification
This variant doesn't assume a direct link between the prover and the verifier.
There is no request, and the prover wants to prove that their work is valid.
The prover solves a problem that can be self-imposed.
This variant doesn't assume a direct link between the prover and the verifier.
There is no request, and the prover wants to prove that their work is valid.
The prover solves a problem that can be self-imposed.
It means that the prover has the choice of the problem.
The verifier must then verify both the problem and the solution before accepting the overall solution.
Bitcoin uses a modified version of this variant.
The verifier must then verify both the problem and the solution before accepting the overall solution.
Bitcoin uses a modified version of this variant.

3. Usage In Bitcoin
Bitcoin uses a Proof-Of-Work protocol when new blocks are appended to the chain.
It makes up a considerable portion of Bitcoin's security.
To be precise, Bitcoin uses a solution-verification mechanism because the blockchain is a decentralized system.
Bitcoin uses a Proof-Of-Work protocol when new blocks are appended to the chain.
It makes up a considerable portion of Bitcoin's security.
To be precise, Bitcoin uses a solution-verification mechanism because the blockchain is a decentralized system.
The protocol Bitcoin uses is called Hashcash.
It's not the original Hashcash protocol but an adjusted version.
The general idea, however, is actually relatively simple.
It's not the original Hashcash protocol but an adjusted version.
The general idea, however, is actually relatively simple.
Every block contains an irreversible cryptographic hash that considers the hash of all transactions within the current block, the previous block's hash, and a so-called nonce in the new block.
This nonce is a positive integer that the miners can freely choose.
This nonce is a positive integer that the miners can freely choose.

The nonce is the only thing the miners can adjust to try and create a hash that fulfills the current difficulty requirements of the network.
You could say it's a number guessing game.
The nonce is set to a value, a hash is created and then checked for validity.
You could say it's a number guessing game.
The nonce is set to a value, a hash is created and then checked for validity.

If it doesn't meet the requirements, the nonce is incremented, a new hash is created, and so on.
Bitcoin adjusts the original Hashcash system by using two continuous SHA-256 hashes instead of an SHA-1 one.
Bitcoin adjusts the original Hashcash system by using two continuous SHA-256 hashes instead of an SHA-1 one.
This leads to Bitcoin being able to freely adjust the difficulty so that not more than six blocks per hour are ever created on the blockchain.
Clients never have to guess the nonce.
They can simply verify that the leading zeroes within the hash actually represent the network's difficulty, and only then that the data presented to them creates the hash they see.
They can simply verify that the leading zeroes within the hash actually represent the network's difficulty, and only then that the data presented to them creates the hash they see.
4. Critique
The guessing game associated with mining Bitcoins leads to a lot of energy consumption.
As many miners compete, many of them do the same work before one of them finds a fitting solution to the problem.
The guessing game associated with mining Bitcoins leads to a lot of energy consumption.
As many miners compete, many of them do the same work before one of them finds a fitting solution to the problem.
Proof-Of-Work protocols are, by design, meant to take a lot of time, and the increased energy consumption is a by-product of this.
There are alternatives that don't consume that much energy and that might currently look like a better alternative.
There are alternatives that don't consume that much energy and that might currently look like a better alternative.
But, Bitcoin has never been successfully hacked.
This is something to take into account when thinking about whether Proof-of-Work is an excellent system to use.
Another protocol might need less energy, but it might also be more prone to being attacked and hacked.
This is something to take into account when thinking about whether Proof-of-Work is an excellent system to use.
Another protocol might need less energy, but it might also be more prone to being attacked and hacked.
5. Thread end
That's it for this thread.
I hope you found something useful for you in it.
If you enjoyed reading this thread, consider dropping a like, retweet the first tweet, and follow me (@oliverjumpertz) for more content like this.
That's it for this thread.
I hope you found something useful for you in it.
If you enjoyed reading this thread, consider dropping a like, retweet the first tweet, and follow me (@oliverjumpertz) for more content like this.
• • •
Missing some Tweet in this thread? You can try to
force a refresh






