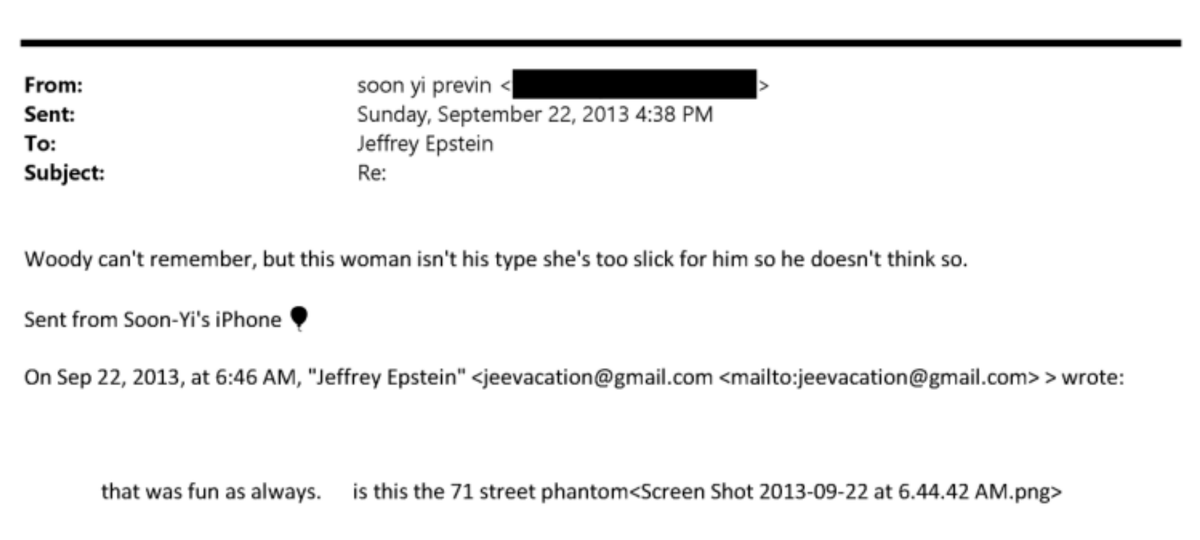
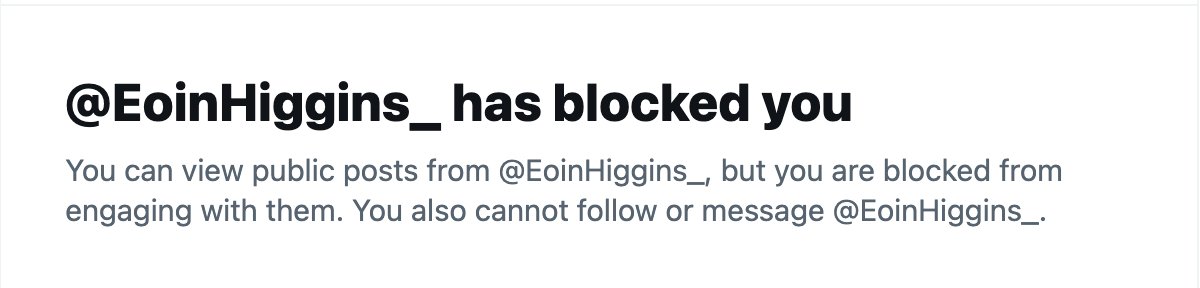
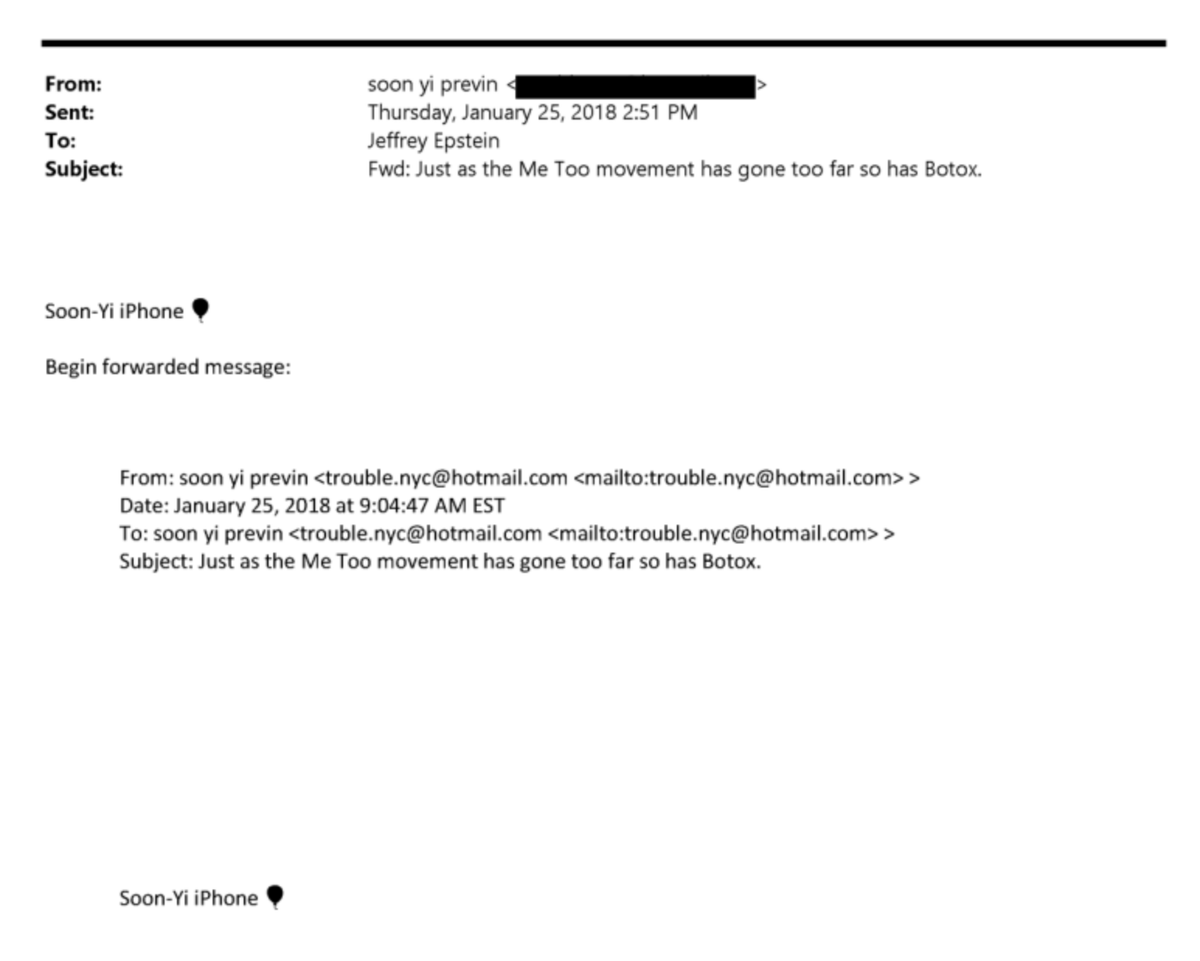
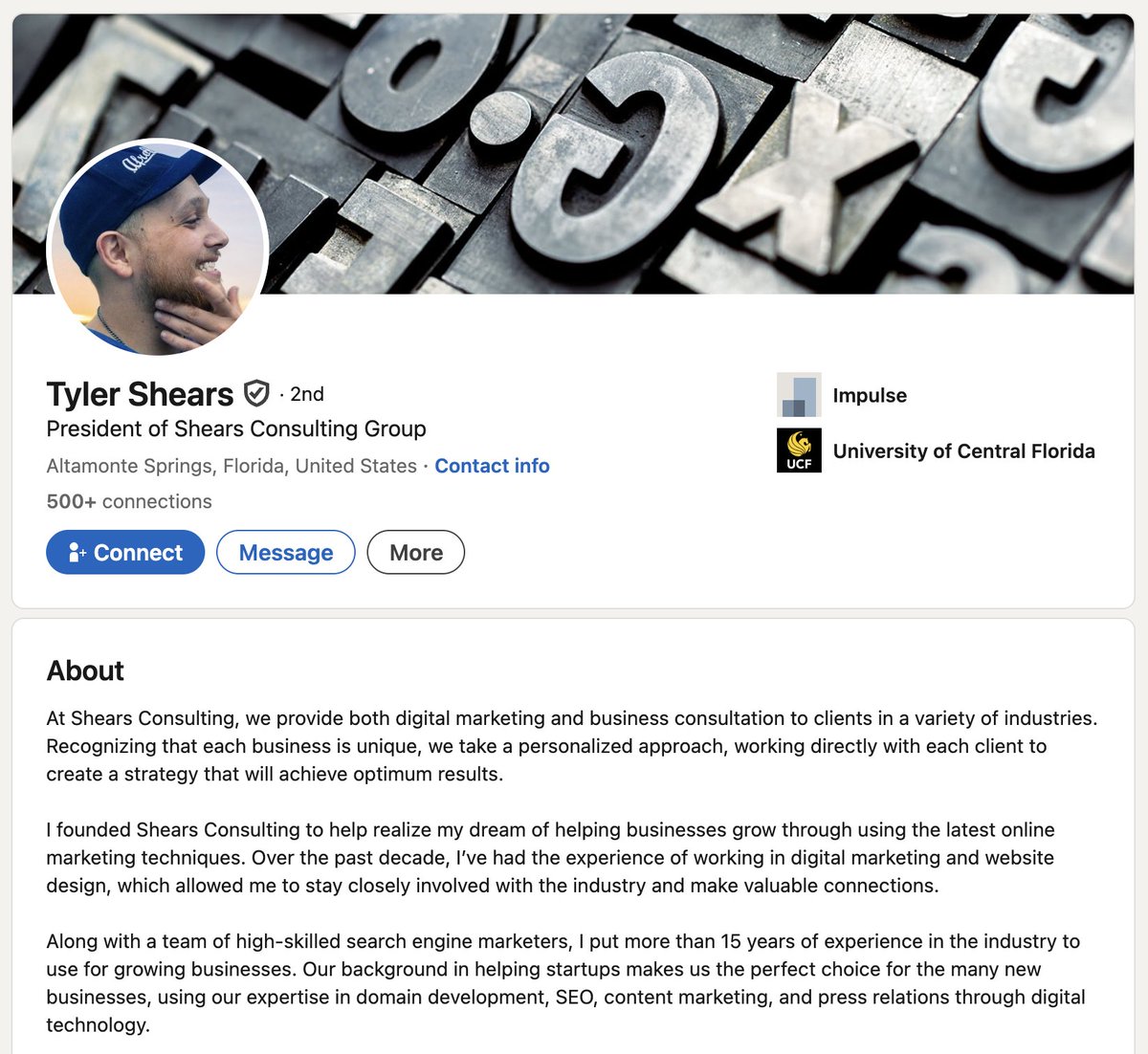
I want to share something important I learned thru the process of producing NFTs with my partner @0xBanana over the past months
I had a valuable realization stemming from the creation of new things of uncertain value & shipping them to buyers
This is for the #infosec crowd
1/8
I had a valuable realization stemming from the creation of new things of uncertain value & shipping them to buyers
This is for the #infosec crowd
1/8
Creating art which is then roundly enjoyed by others has helped me with perfectionism.
Intellectually, I know that ‘perfect is the enemy of good’.
Unfortunately, my standards for my own work are often far too high to encourage incremental progress & learning in public.
2/8
Intellectually, I know that ‘perfect is the enemy of good’.
Unfortunately, my standards for my own work are often far too high to encourage incremental progress & learning in public.
2/8
Part of the reason why I feel that way is because the security community is so frequently negatively judging. As this is the community I joined from a young age, it has molded my behavior to be far too constrained & limited — in direct opposition to the hacker ethos.
3/8
3/8
Judging the work of oneself & others to an extremely high (& often unattainable) standard reduces the likelihood that people in a given community will produce original work for the benefit of said community by releasing it publicly — even when such efforts are sorely needed
4/8
4/8
The community essentially molded my behavior to the point where I have refused to release original work in the security space.
Meaning: useful code/scripts. Methodologies. Process improvements. Updates to the state of the art in information security. Incremental progress.
3/8
Meaning: useful code/scripts. Methodologies. Process improvements. Updates to the state of the art in information security. Incremental progress.
3/8
I haven’t always felt the things I’ve created have been good enough to stand up to the intense scrutiny which comes from both being a woman and a human in this space — and even if they were, I wanted to avoid the minutiae of the forced and oft-entitled/angry peer review.
4/8
4/8
Through the work and culture of infosec, I’ve developed an extremely keen eye for mistakes, errors, and systematic problems — and often fail to state how much I appreciate the value of someone’s work before criticizing it.
5/8
5/8
Yet what I’ve helped make has received so much kudos, & the process of making them has been so enjoyable & validating, that I feel I am “good enough” to release artwork for public sale & consumption under my own name — even if not at the level of a Kandinsky or Warhol.
6/8
6/8
Seeing the support and kindness people make the effort to express in the #NFTcommunity (within certain communities on Discord especially, shout-out to @itskay_k) has repeatedly shown me that there is another way, and not everyone is like this outside our weird little bubble.
7/8
7/8
I’d love for the infosec community to recognize how our overly-critical reactions to the work of others is often the opposite of encouragement, even if well-intentioned, and reduces opportunities for us to effectively learn from each other to improve our craft & culture ❤️
8/8
8/8
• • •
Missing some Tweet in this thread? You can try to
force a refresh