
All right, Twitter; time to kick the @awscloud tires on these new Graviton2 Lambda functions. 

Now, @alex_casalboni has already done the heavy lifting for me with this dingus. github.com/alexcasalboni/…
It supports the new runtimes even!
It supports the new runtimes even!
I'll deploy it through the Serverless Application Repository, meaning I'm now a full third of that thing's customer base for October.
Now I need a Lambda function to test this on. Fortunately I have one that fires off once a minute, is idempotent, and powers the horrible yet strangely compelling @awscwoud.
Let's give this config a shot. (Somewhere an AWS employee is looking up the account ID and discovering that the globally unique account alias for this @awscloud account is indeed "Shitposting.") 
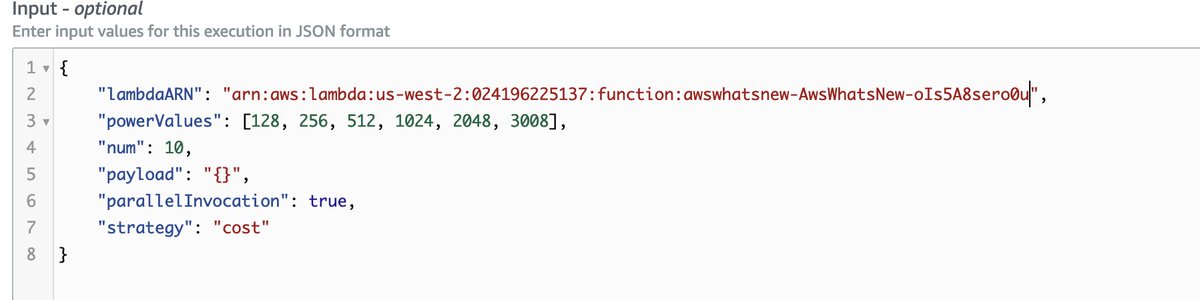
There we go. No surprise, "cheap" or "good" are the options here. Now let's see if this asplodes when I kick the Lambda over to use Graviton2. 

I use the advanced DevOps IaC approach of "using the @awscloud console, then lying about it" to make the change. Yes, I really did call my handler that. 

(Had to repackage and re-upload it just because I'm a sensible person who sets code packages to expire.)
Now we run the thing and see if it melts. Hope with me!
I don't know about you, but looking at five zeros before a number doesn't help me get a sense of cost overly well. Fortunately @alex_casalboni has thought of this with the handy "Compare" button. 

It looks like 256MB + Gwaviton2 is the most cost effective answer here unless I misread the admittedly complex chart. Am I right?
John is completely correct, but remember that this is a backend job. The latency absolutely does not matter; @awscwoud doesn't need to respond THAT quickly.
https://twitter.com/zz9/status/1453160137586323465?s=20
An update on my Graviton2 Lambda conversion. The most obnoxious part was getting the tooling updated to support the new configuration. The wrapt library by default compiles a C extension; you can override it to use pure python, but that's not straightforward.
• • •
Missing some Tweet in this thread? You can try to
force a refresh








