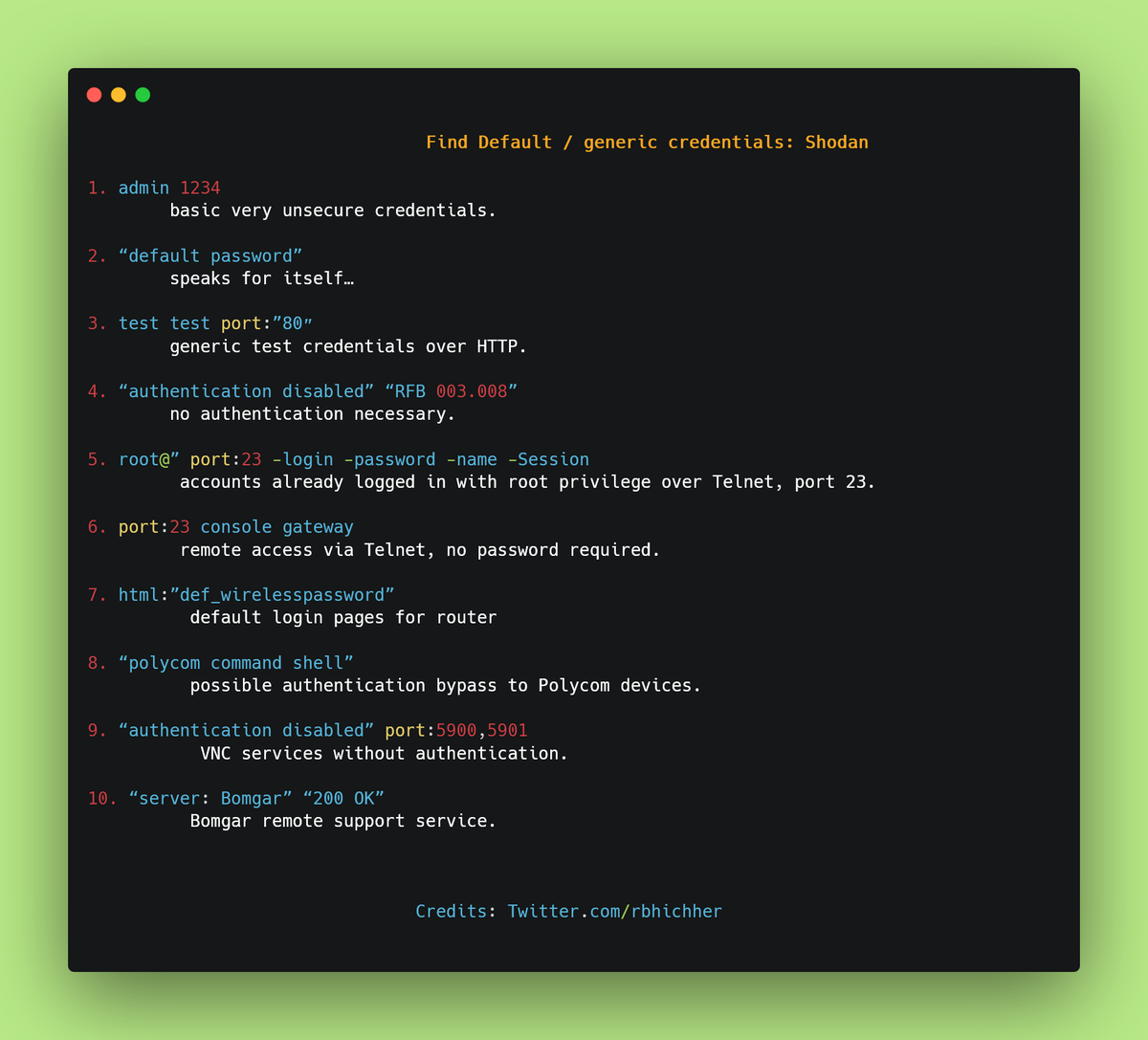
Shodan detects devices that are connected to the internet at any given time, the location of those devices and their current users.
It's a thread 🧵👇
You can search, hack and even get a bounty if lucky enough with @shodanhq
#infosec
It's a thread 🧵👇
You can search, hack and even get a bounty if lucky enough with @shodanhq
#infosec
Feel free to add more #shodan queries.
• • •
Missing some Tweet in this thread? You can try to
force a refresh