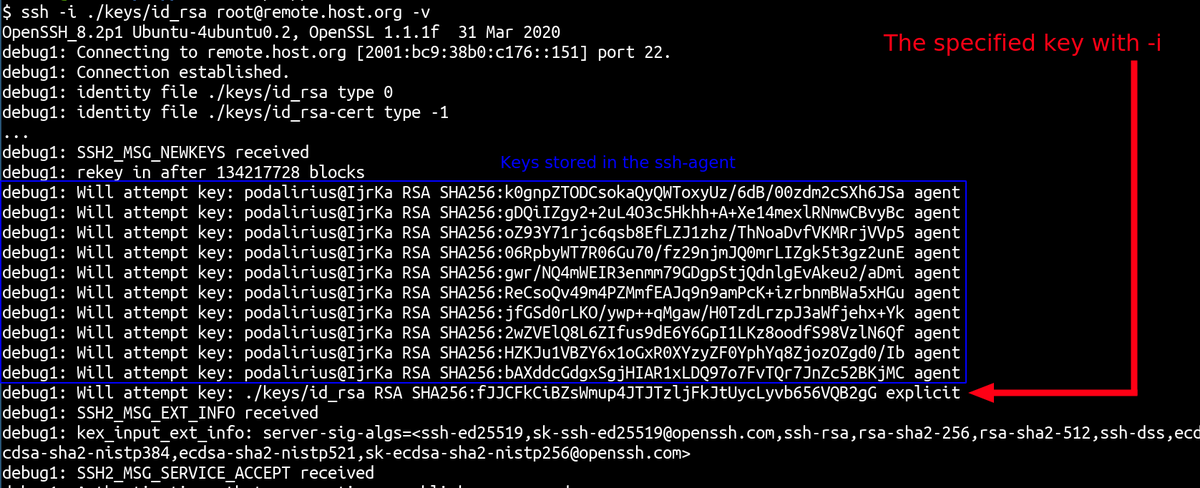
[#thread 🧵] For this third day of #CyberAdvent (3/24), I'll tell you a story. The story of how I gained root access to a server by leveraging a really fun feature in a web application. This #pentest #writeup will explain the complete process from recon to root. 🦋 

[#thread 🧵(2/9)] In the recon phase of my pentest, as usual I was performing a port scan. In the output from nmap, I saw an uncommon port 86 with an HTTP server running "Micro Focus DSD 1.0.0": 

[#thread 🧵(3/9)] When going on the page from a browser, surprise 🥳🎉 we have an unauthenticated access! This is cool, but I never saw this app before so I didn't know whether we could exploit it simply or not! 

[#thread 🧵(4/9)] This application allows to manage #COBOL applications, like what Apache Tomcat does with Java applications. Let's mess around with this!🕵️ 

[#thread 🧵(5/9)] When we create a new application, we have a "Script" tab allowing to create a start/stop shell script that will be executed before/after starting the COBOL application. 

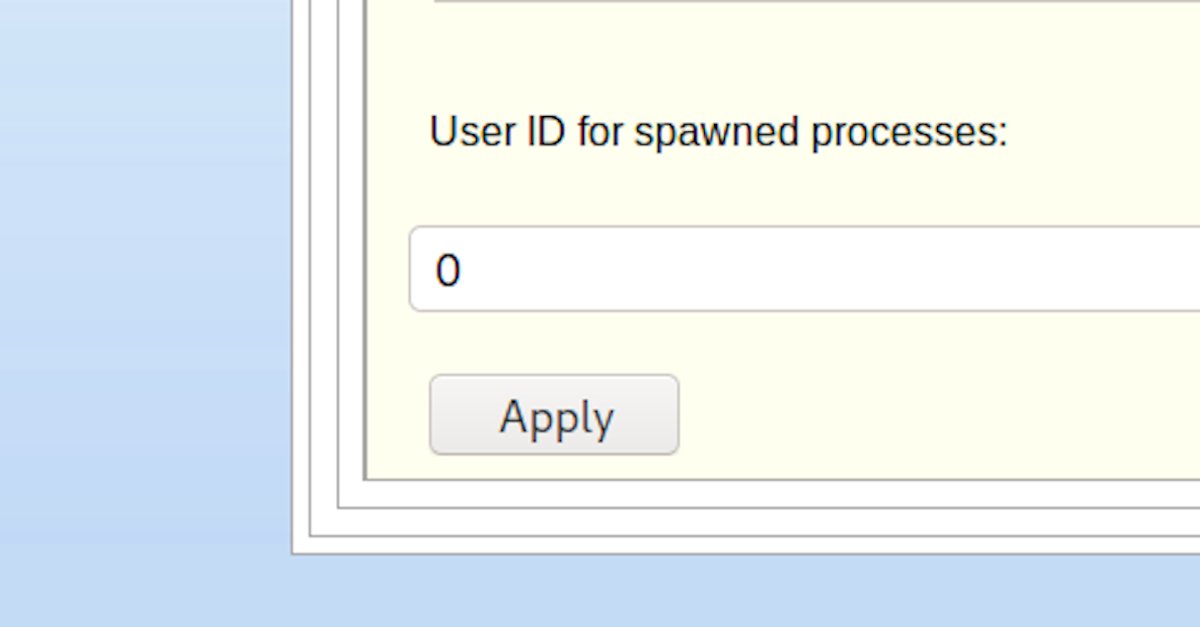
[#thread 🧵(6/9)] We can execute commands on the server, but we do not have any output. And 😱 there is an unbelievable option on this tab. "User id", we can literally choose the user id the script will run as. I'm going to use uid=0 to run commands as root! 
[#thread 🧵(7/9)] As the remote machine was an IBM server with ksh shell, I had to write a reverse shell by living off the land because classic payloads (even compiled static binaries) did not work. So I wrote a wget reverse shell during the night, and I tried it the next morning 

[#thread 🧵(8/9)] Basically, it's a while True loop receiving and sending data in base64 through the User-Agent http header with wget: 

[#thread 🧵(9/9)] I used my wget reverse shell as root to create a new user on the machine, and set its password. After this, I could simply connect with SSH to the machine, and boom I was in ! I also added my user to the sudoers to gain complete control over the server ! 🎉🥳🕵️ 

Complete technical details about the MicroFocus exploit is available on my website here:
podalirius.net/en/articles/ex…
podalirius.net/en/articles/ex…
And complete technical details about the wget reverse shell principle is available here:
podalirius.net/en/articles/co…
podalirius.net/en/articles/co…
• • •
Missing some Tweet in this thread? You can try to
force a refresh