
Senior Security Researcher @SpecterOps | 3xMicrosoft Security MVP | Creator of opensource security tools 🎬 https://t.co/QaAENc4NcY
How to get URL link on X (Twitter) App





 [#thread 🧵(2/9)] A bit of History !
[#thread 🧵(2/9)] A bit of History !

 [#thread 🧵(2/10) ] LDAP is a directory structure (a tree) containing objects with their attributes:
[#thread 🧵(2/10) ] LDAP is a directory structure (a tree) containing objects with their attributes: 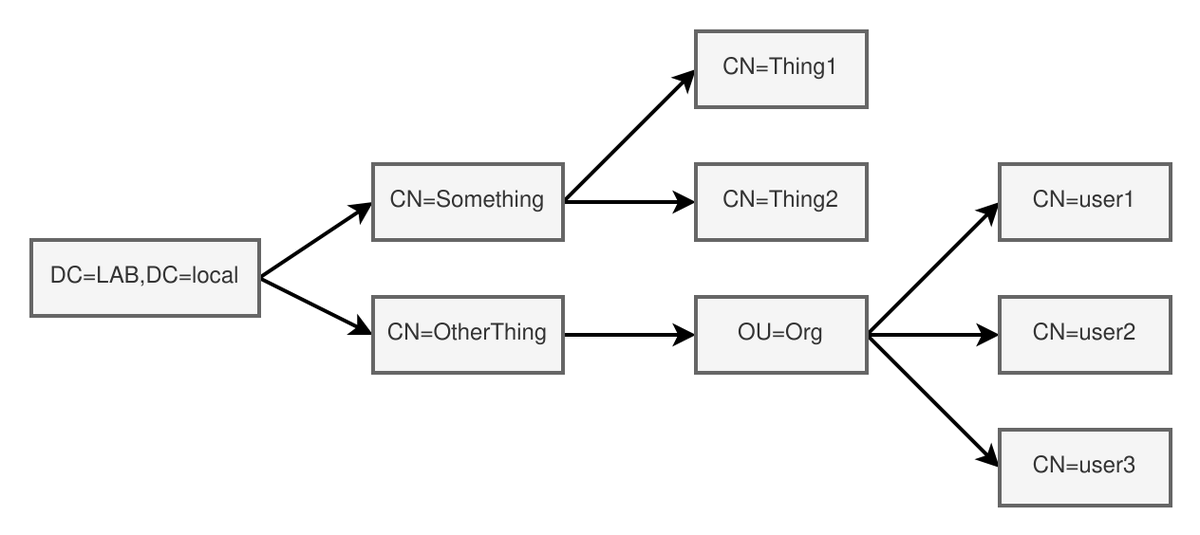

 [#thread 🧵(2/9)] In the recon phase of my pentest, as usual I was performing a port scan. In the output from nmap, I saw an uncommon port 86 with an HTTP server running "Micro Focus DSD 1.0.0":
[#thread 🧵(2/9)] In the recon phase of my pentest, as usual I was performing a port scan. In the output from nmap, I saw an uncommon port 86 with an HTTP server running "Micro Focus DSD 1.0.0": 


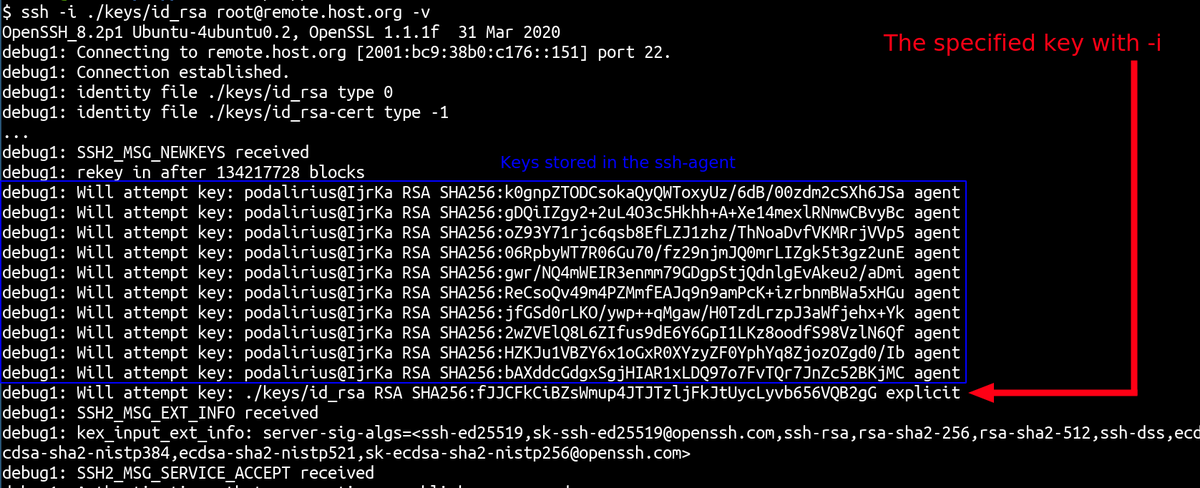
 After this message, ssh tries to authenticate with the keys in the order listed above. Why is that a problem ?
After this message, ssh tries to authenticate with the keys in the order listed above. Why is that a problem ?