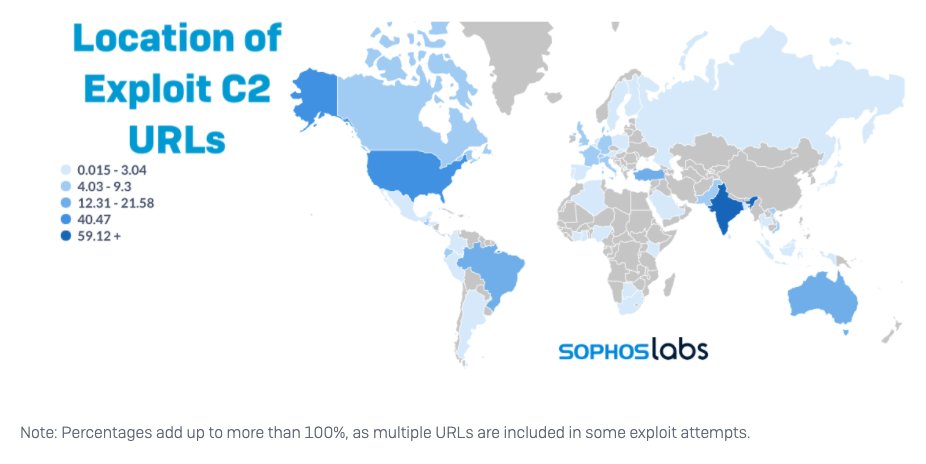
NEW: Attackers test “CAB-less 40444” exploit in a dry run
An updated exploit takes a circuitous route to trigger a Word document into delivering an infection without using macros...
1/11
An updated exploit takes a circuitous route to trigger a Word document into delivering an infection without using macros...
1/11
In September, Microsoft published mitigation steps and released a patch to a serious bug (CVE-2021-40444) in the Office suite of products. Criminals began exploiting the Microsoft MSHTML Remote Code Execution Vulnerability at least a week before September’s Patch Tuesday... 2/11
...but the early mitigations (which involved disabling the installation of ActiveX controls), and the patch (released a week later), were mostly successful at stopping the exploits that criminals had been attempting to leverage to install malware. 3/11
Unfortunately, soon after Microsoft published these solutions, attackers morphed the attack in an attempt to get around the patch’s protection. 4/11 

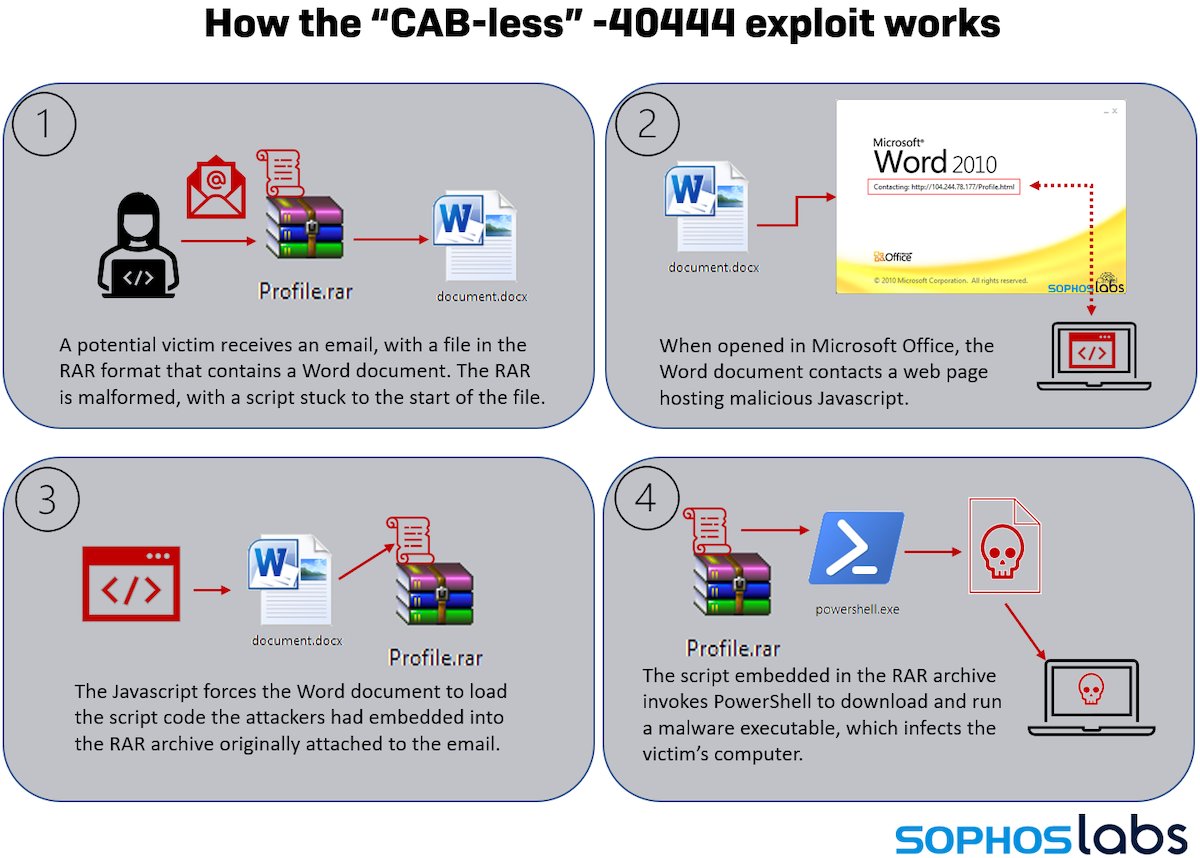
Between October 24 and 25, we received a small number of spam email samples that contained weaponized file attachments; The attachments represent an escalation of the attacker’s abuse of the -40444 bug and demonstrate that... 5/11
...even a patch can’t always mitigate the actions of a motivated and sufficiently skilled attacker.
Each of the messages shared the same body content, FROM: address, and malicious attachment. 6/11
Each of the messages shared the same body content, FROM: address, and malicious attachment. 6/11
In the initial versions of CVE-2021-40444 exploits, malicious Office document retrieved a malware payload packaged into a Microsoft Cabinet (or .CAB) file. When Microsoft’s patch closed that loophole, attackers discovered they could... 7/11
...use a different attack chain altogether by enclosing the maldoc in a specially-crafted RAR archive. Because it doesn’t actually use the CAB-style attack method, we’ve called it the CAB-less 40444 exploit. 8/11
👉 Detection guidance
Sophos endpoint products will detect the weaponized document files that contain the CABless -40444 exploit as Troj/DocDL-AEOL; Sophos endpoint products generically detect Formbook malware based on longstanding static analysis rules. 9/11
Sophos endpoint products will detect the weaponized document files that contain the CABless -40444 exploit as Troj/DocDL-AEOL; Sophos endpoint products generically detect Formbook malware based on longstanding static analysis rules. 9/11
+ We’ve published indicators relating to samples investigated in this report on the SophosLabs Github page. 11/11
See more details about how the attack transpired in the full article from @threatresearch and Stephen Ormandy...
news.sophos.com/en-us/2021/12/…
11/11
news.sophos.com/en-us/2021/12/…
11/11
• • •
Missing some Tweet in this thread? You can try to
force a refresh