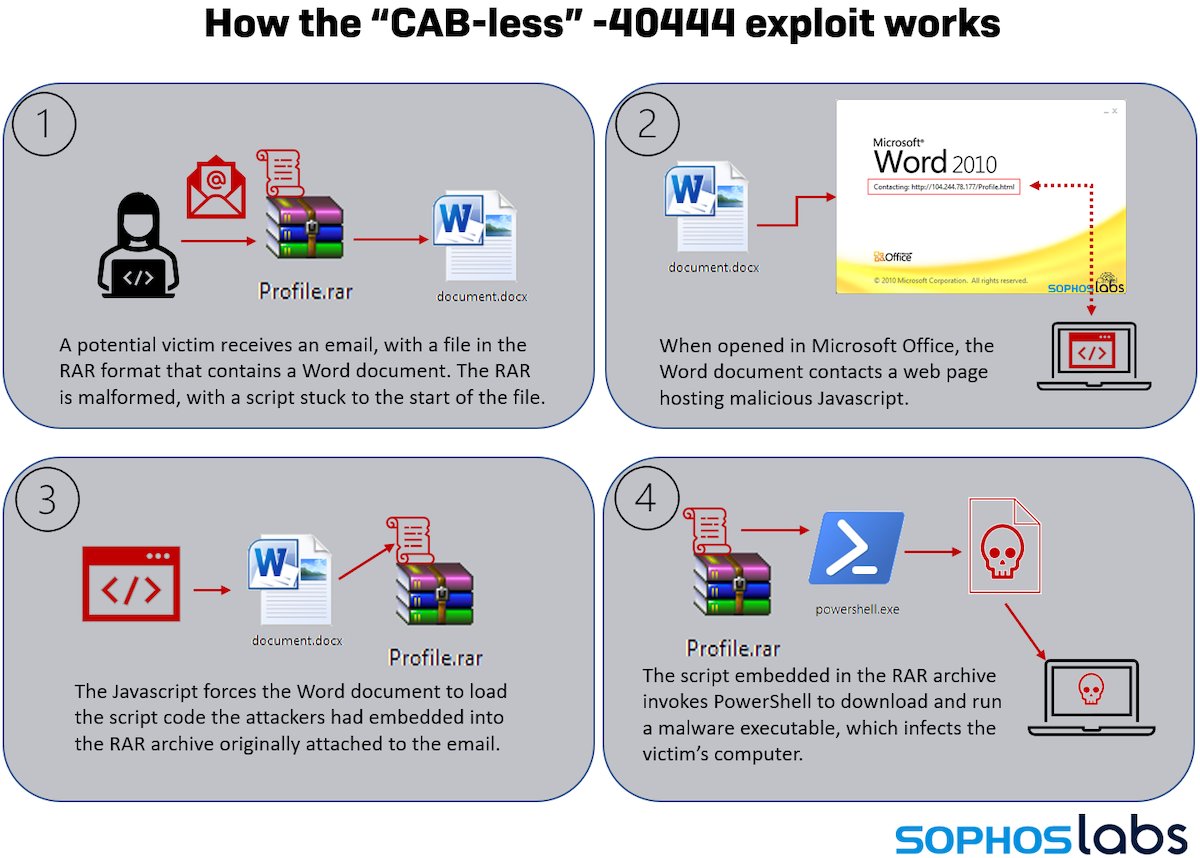
NEW: Avos Locker remotely accesses boxes, even running in Safe Mode
Infections involving this relatively new ransomware-as-a-service spiked in November and December...
1/16
Infections involving this relatively new ransomware-as-a-service spiked in November and December...
1/16

Over the past few weeks, an up-and-coming ransomware family that calls itself Avos Locker has been ramping up attacks while making significant effort to disable endpoint security products on the systems they target. 2/16
In a recent series of ransomware incidents involving this ransomware, Sophos Rapid Response discovered that attackers had booted their target computers into Safe Mode to execute the ransomware, similar to now-defunct Snatch, REvil, and BlackMatter ransomware families. 3/16
The reason for this is that many, if not most, endpoint security products do not run in Safe Mode — a special diagnostic configuration in which Windows disables most third-party drivers and software, and can render otherwise protected machines unsafe. 4/16
Avos Locker attackers were not only rebooting the machines into Safe Mode for the final stages of the attack; They also modified the Safe Mode boot configuration so they could install and use the AnyDesk tool while the Windows computers were still running in Safe Mode. 5/16
Normally, third party software would be disabled on a computer that had been rebooted into Safe Mode, but these attackers clearly intended to continue to remotely access and control the targeted machines unimpeded. 6/16
It isn’t clear whether a machine that had been set up in this way – with AnyDesk set to run under Safe Mode – would even be remotely manageable by its legitimate owner. The operator of the machine might need to physically interact with the computer in order to manage it. 7/16 

In some instances we’ve also seen the attackers employ a tool called Chisel, which creates a tunnel over HTTP, with the data encrypted using SSH, that the attackers can use as an secure back channel to the infected machine. 8/16
There are also other indications that, in some of the attacks, there had been lateral movement and other indicators of malicious behavior which were saved in the Event Logs of some machines. 9/16
The attackers also appear to have leveraged another commercial IT management tool known as PDQ Deploy to push out Windows batch scripts to machines they planned to target. 10/16
@Sophos Rapid Response has created a chart that highlights the consequences of one of these batch files running. The batch files are run before the computer is rebooted into Safe Mode. 11/16 

👉 Guidance and detection
Working in Safe Mode makes the job of protecting computers all the more difficult, because Microsoft does not permit endpoint security tools to run in Safe Mode. 12/16
Working in Safe Mode makes the job of protecting computers all the more difficult, because Microsoft does not permit endpoint security tools to run in Safe Mode. 12/16
That said, @Sophos products behaviorally detect the use of various Run and RunOnce Registry keys to do things like reboot into Safe Mode or execute files after a reboot. 13/16
We have been refining these detections to reduce false positives, as there are many completely legitimate tools and software which use these Registry keys for normal operations. 14/16
👉 The key message for IT security teams facing such an attack is that even if the ransomware fails to run, until every trace of the attackers’ AnyDesk deployment is gone from every impacted machine, the targets will remain vulnerable to repeated attempts. 15/16
See more details from @threatresearch: news.sophos.com/en-us/2021/12/…
Thank you to Fraser Howard, @AnandAjjan, @AltShiftPrtScn, Ferenc László Nagy, Sergio Bestulic, and Timothy Easton for their help with analysis and threat response.
16/16
Thank you to Fraser Howard, @AnandAjjan, @AltShiftPrtScn, Ferenc László Nagy, Sergio Bestulic, and Timothy Easton for their help with analysis and threat response.
16/16
• • •
Missing some Tweet in this thread? You can try to
force a refresh