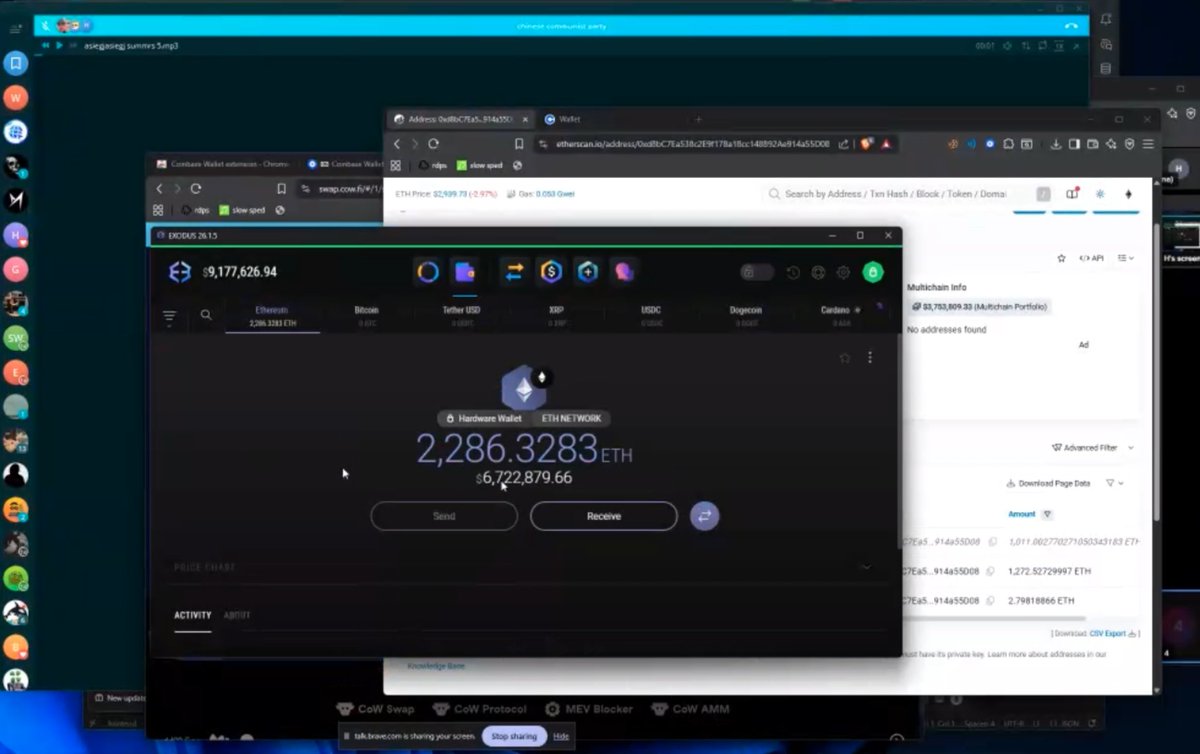
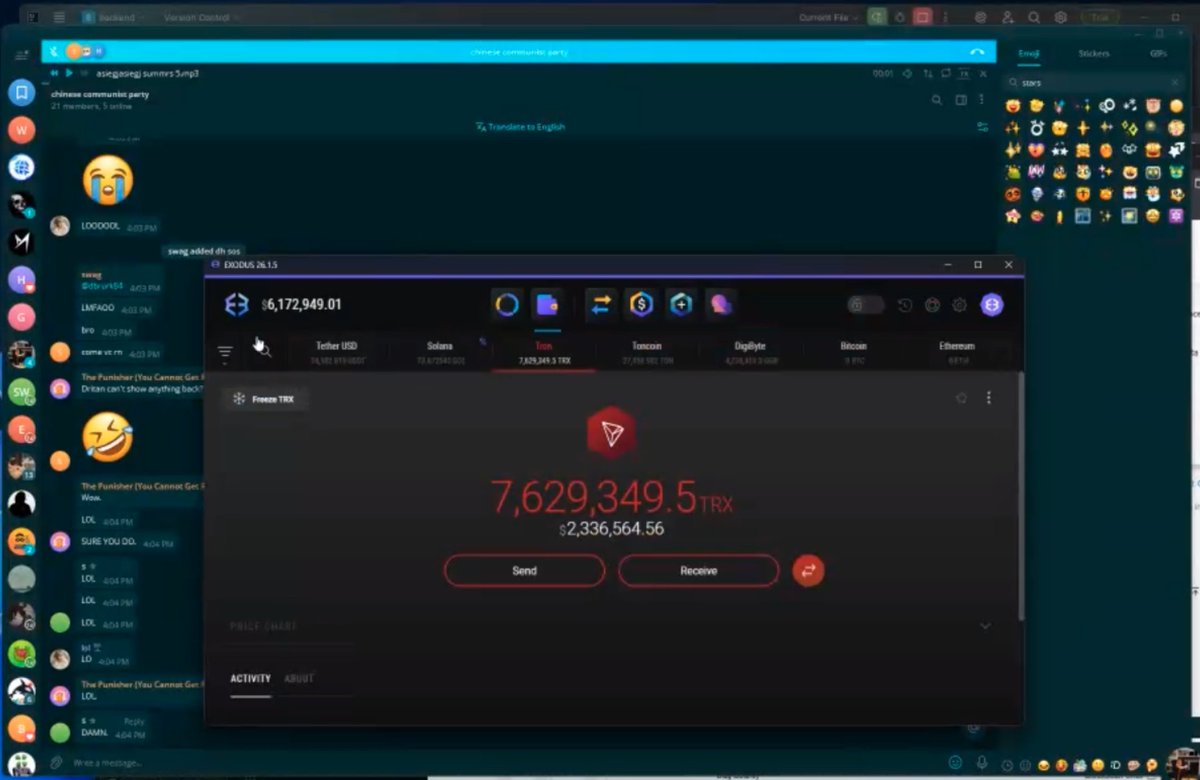
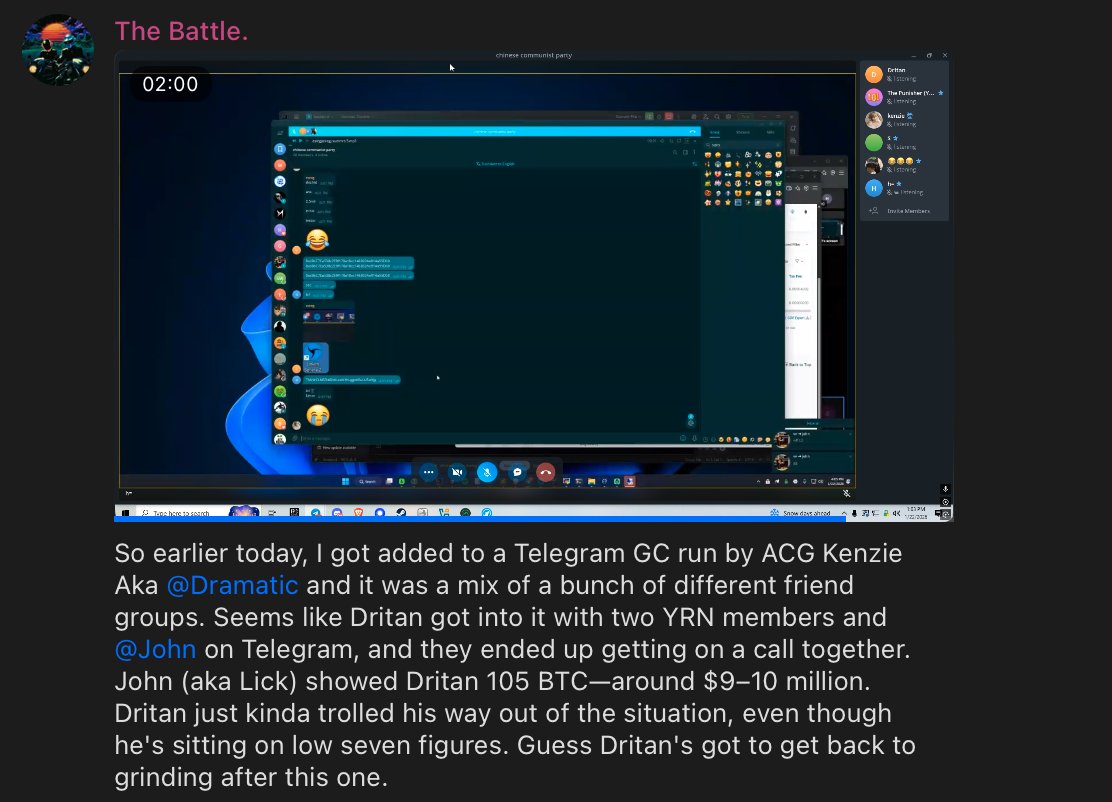
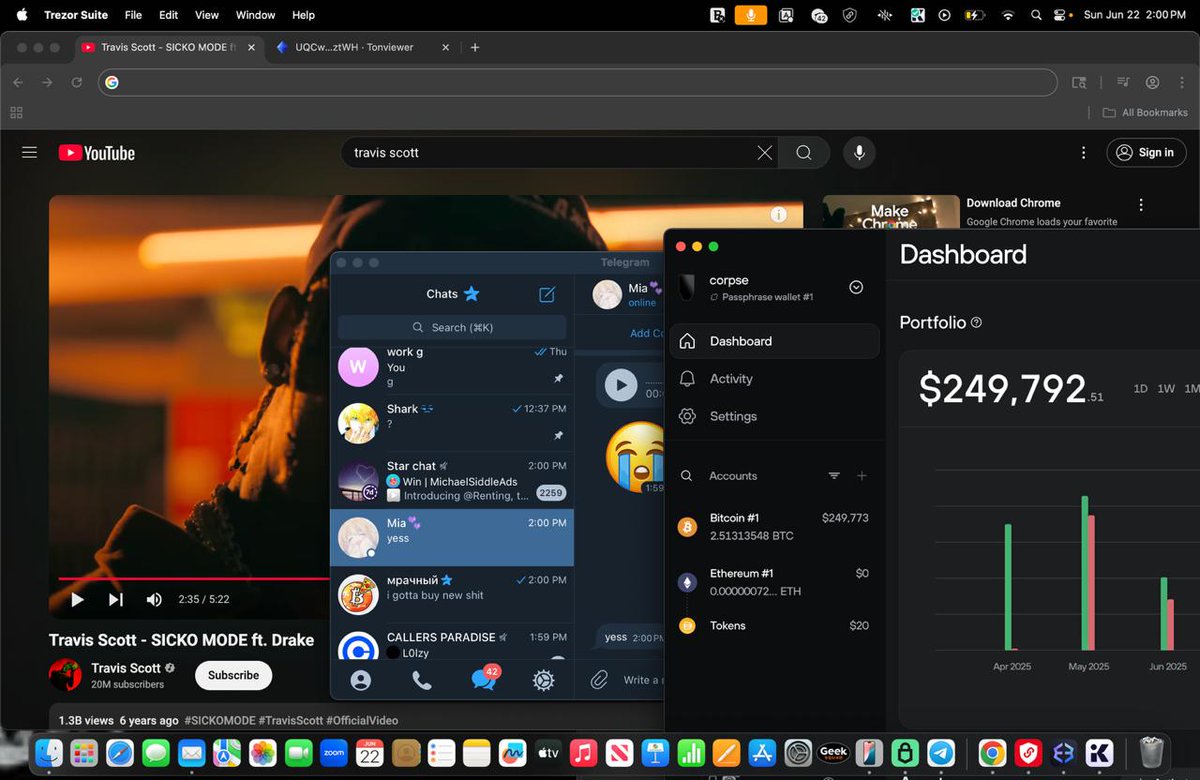
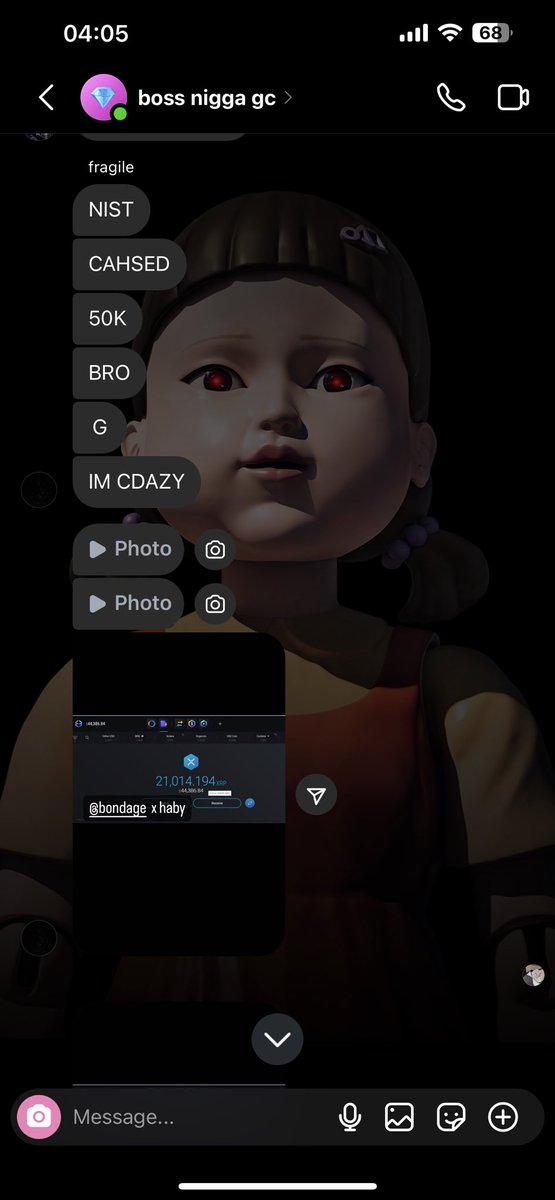
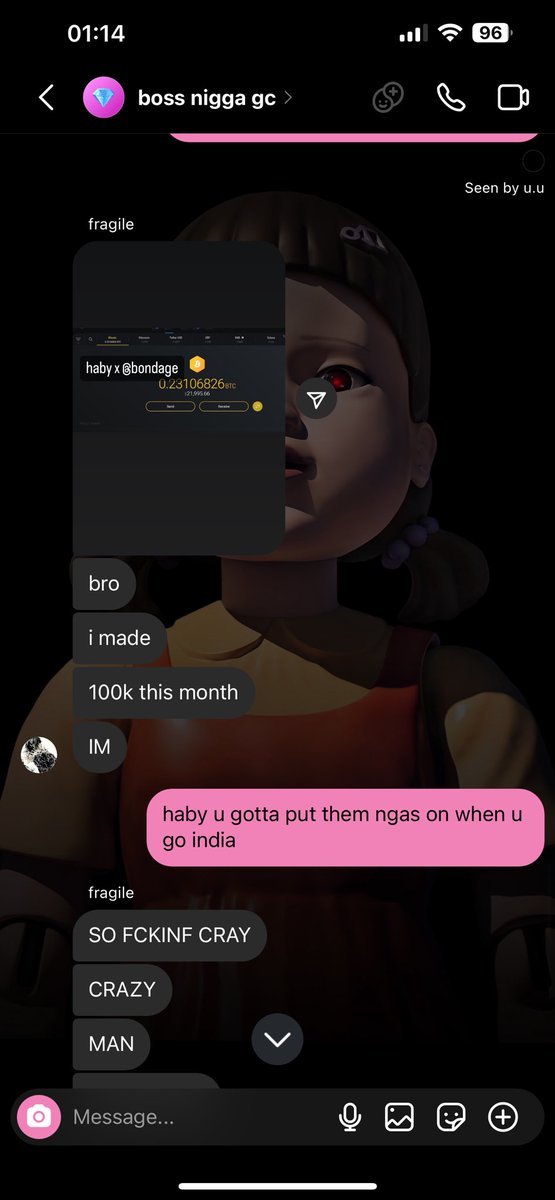
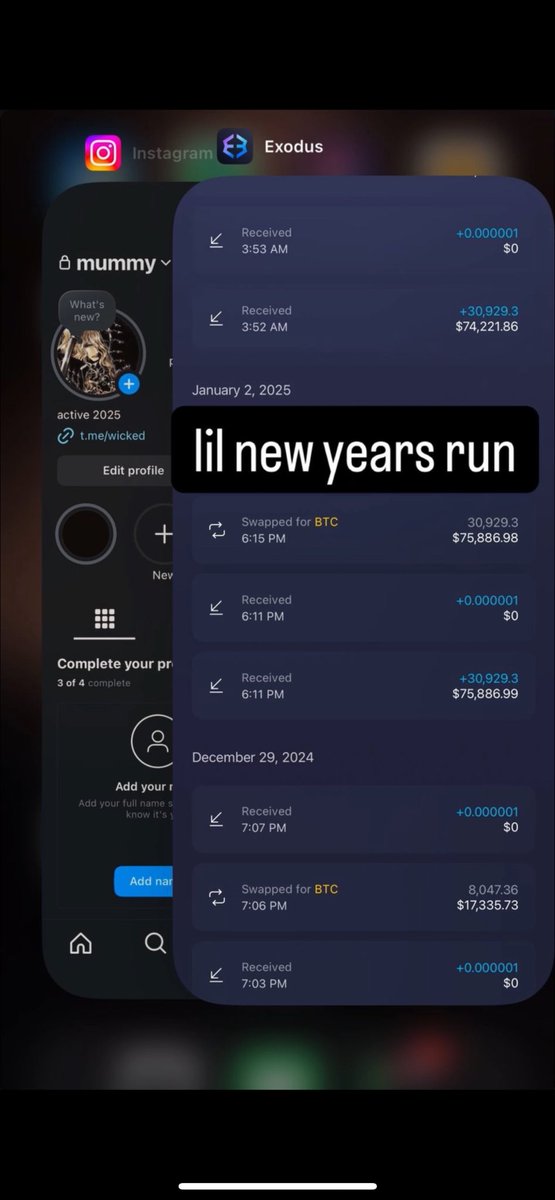
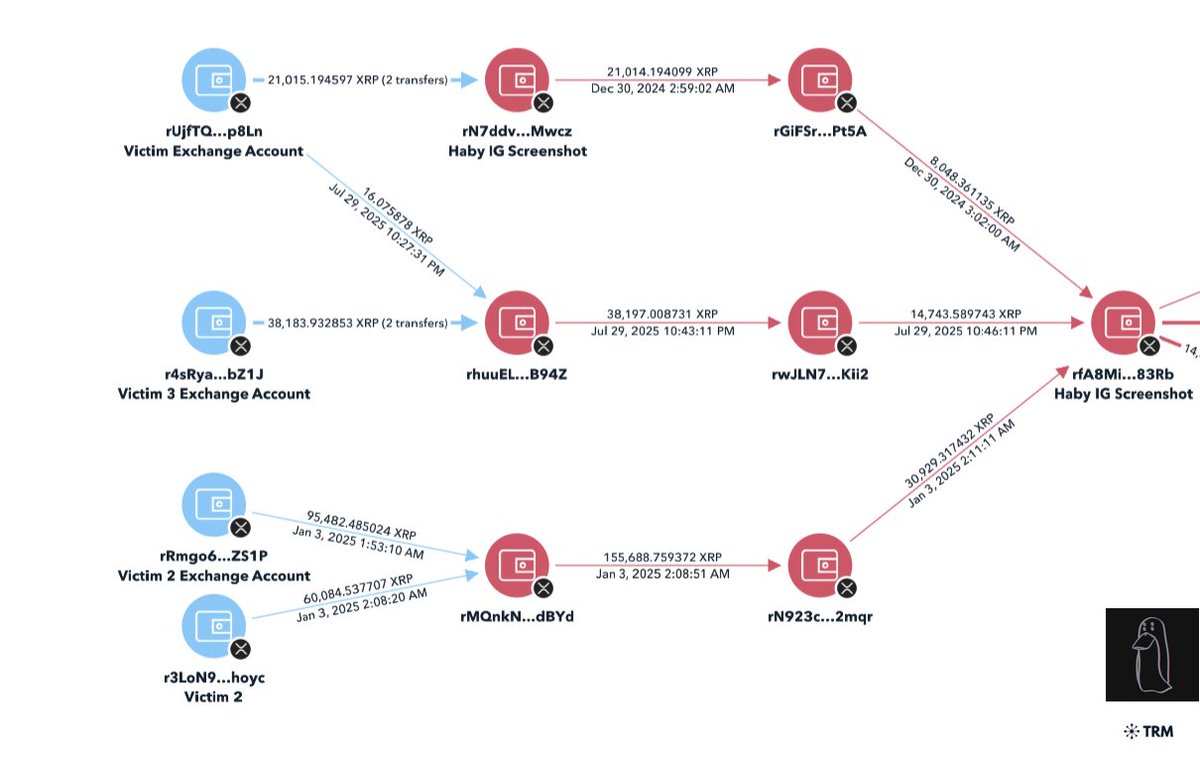
1/ Let’s review all the direct scams Bitboy has worked with in the past. Just in case you forgot here is the flyer with how much he charges.
I received this a while back by posing as a project interested in a promotion.
🧵 👇

I received this a while back by posing as a project interested in a promotion.
🧵 👇


2/After Coffeezilla made a video on paid promotions in the crypto space last month an Official Bitboy representative stated they “rigorously vet” projects.
I uncovered 7 direct scams Bitboy actively worked with and promoted to his audience.
I uncovered 7 direct scams Bitboy actively worked with and promoted to his audience.

3/ In Fall 2020 Bitboy worked with $MYX and even was warned by community members. Bitboy has since deleted the video. 

https://twitter.com/LigerLite/status/1297881775906193409


4/ Also in fall 2020 Bitboy worked with $DISTX a video he titled “my most trusted coin”
He went on to change the video title later on. The video also had zero promotion disclosure & project exit scammed.
The video is still up but don’t worry it has been archived safely by me.



He went on to change the video title later on. The video also had zero promotion disclosure & project exit scammed.
The video is still up but don’t worry it has been archived safely by me.




5/ Now we have Zao Finance another project that exit scammed in Fall 2020.
He deleted the tweet but don’t worry I recovered it.
At least he put #ad on the scam right?


He deleted the tweet but don’t worry I recovered it.
At least he put #ad on the scam right?



6/ Here’s $ETHY another scam Bitboy worked with in December 2020 that ended up rugging
Notice a pattern here with deleted videos?


Notice a pattern here with deleted videos?



7/ Another one people forget about is $LOCK (Meridian Network) a project he covered twice in late 2020.
The project’s Twitter & Website are no longer there and once again Bitboy deleted his video on it.


The project’s Twitter & Website are no longer there and once again Bitboy deleted his video on it.



8/ We have the $CPH slow rug promoted by Bitboy (also deleted)
Coin was delayed for years and founder has sketchy past.
Search “$cph scam” for more

Coin was delayed for years and founder has sketchy past.
Search “$cph scam” for more


9/ We also have $PAMP another scam promoted by Bitboy. The video hasn’t been deleted but is unlisted.
I’ve also downloaded this video.


I’ve also downloaded this video.



10/ I’m sure there is more so feel free to drop any comments if you’ve found any
It’s clear simple due diligence is not done and it’s profits over followers with shills. Just bc you delete a video doesn’t mean it didn’t happen
As per usual follow for more threads in the future
It’s clear simple due diligence is not done and it’s profits over followers with shills. Just bc you delete a video doesn’t mean it didn’t happen
As per usual follow for more threads in the future

In case you missed my thread on Bitboy stealing art for his NFTs
https://twitter.com/zachxbt/status/1477450175916425221
An example of plagiarism Bitboy did
https://twitter.com/zachxbt/status/1478161465123168259
Another example of plagiarism Bitboy did this past year
https://twitter.com/zachxbt/status/1478162433449603072
@YouTubeCreators @YouTube @YTAdvertisers how can you let people be continuously taken advantage of by crypto YouTubers with their deceptive advertising…
More plagiarism
https://twitter.com/zachxbt/status/1477450175916425221
• • •
Missing some Tweet in this thread? You can try to
force a refresh