This is awesome, thank you @x86matthew.
I wanted to share a blue team perspective on monitoring and hunting for this kind of LNK -> EXE bamboozling
We'll use the example PoC if that's alright with you 🧵
I wanted to share a blue team perspective on monitoring and hunting for this kind of LNK -> EXE bamboozling
We'll use the example PoC if that's alright with you 🧵
https://twitter.com/x86matthew/status/1489624392627859458
Let's execute the PoC of the .LNK, which brings a pop up.
@x86matthew was kind enough to create a non-malicious PoC. But of course an adversary will not be so kind.
So let's take a look at our logs:
@x86matthew was kind enough to create a non-malicious PoC. But of course an adversary will not be so kind.
So let's take a look at our logs:

Let's assume we're rolling with SysMon.
We get an Event 11 for a strange tmp*.exe being created. This of course could be called something different if re-engineered by an adversary IRL.
But for now let's focus on this tmp*.exe
We get an Event 11 for a strange tmp*.exe being created. This of course could be called something different if re-engineered by an adversary IRL.
But for now let's focus on this tmp*.exe

We can see a process is connected to this tmp*.exe, with a parent PowerShell process offering us some insight into the tmp*.exe. 

We can then find evidence that the .LNK was successful in executing.
Not just because we received the pop up box, but because in our Prefetch directory we can see evidence of the tmp*.exe successfully executing
Not just because we received the pop up box, but because in our Prefetch directory we can see evidence of the tmp*.exe successfully executing

Okay so that's a post-mortem of monitoring execution.
Your logging / SIEM solutions aren't blind to this technique, but it is not immediately obvious that it originated from LNK to EXE
Now, I want to talk about how to proactively HUNT for this🕵️🔍🔍
Your logging / SIEM solutions aren't blind to this technique, but it is not immediately obvious that it originated from LNK to EXE
Now, I want to talk about how to proactively HUNT for this🕵️🔍🔍
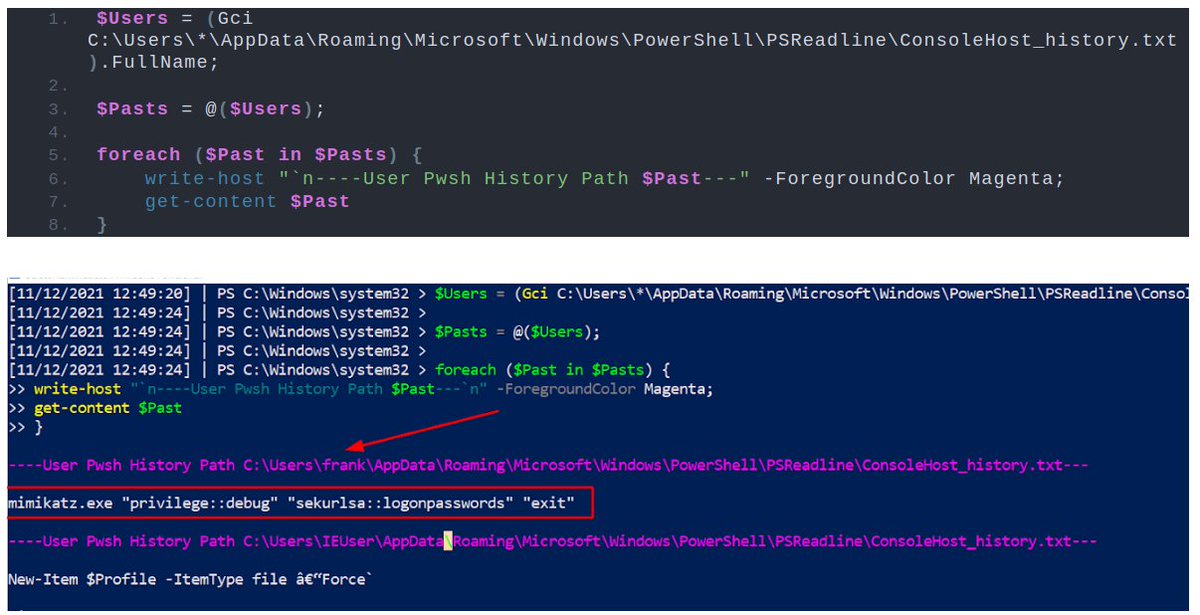
This PwSh one-liner asks for LNKs, and specifies 'only show me after X date'. Then, it asks to see the filename and the related target.
This PwSh is noisy if you don't filter well! But shows anomalies, and scales well for a tool like Velociraptor.
This PwSh is noisy if you don't filter well! But shows anomalies, and scales well for a tool like Velociraptor.

Probably missed loads here, but wanted to contribute with some defence insights.
Thanks @x86matthew
If anyone wants the above PowerShell, or other blue team tips, I have them on my repo: github.com/Purp1eW0lf/Blu…
End of thread 🧵
Thanks @x86matthew
If anyone wants the above PowerShell, or other blue team tips, I have them on my repo: github.com/Purp1eW0lf/Blu…
End of thread 🧵
• • •
Missing some Tweet in this thread? You can try to
force a refresh