
Anatomy of a Russian Seperatist False Flag - On February 18th the Telegram channel of the press service of the People's Militia of the Donetsk People's Republic published the following video, claiming to show a sabotage operation targeting chlorine tanks
t.me/nm_dnr/6192
t.me/nm_dnr/6192
They claimed that Polish speaking saboteurs "planned to blow up a tank with chlorine on the territory of a sewage treatment plant near the city of Gorlovka” and the video was recovered from the saboteurs' bodies.
t.me/nm_dnr/6191
t.me/nm_dnr/6191

However, the online community started to quickly identify a number of issues with the evidence presented. @oldLentach examined the metadata from the video, and discovered a media creation data of Feb 8th, and a Feb 4th project folder date.
https://twitter.com/oldLentach/status/1494962375816007685
Also in the metadata was a filename, "M72A5 LAW and AIPLAS live fire.mp4" under the “Pantry” section of the metadata. This part of the metadata contains details of other files that make up the published file, such as other sources of audio and video. 

That means the video file had additional audio or video added to it. Adobe provides details of their Pantry/Ingredient system and what it means with regards to metadata here:
wwwimages.adobe.com/content/dam/ac…
wwwimages.adobe.com/content/dam/ac…

A quick search on YouTube reveals just one video with exactly the same name as the file in the metadata of the “Polish saboteur” video, from a military firing range in Finland, featuring a number of bangs and explosions.

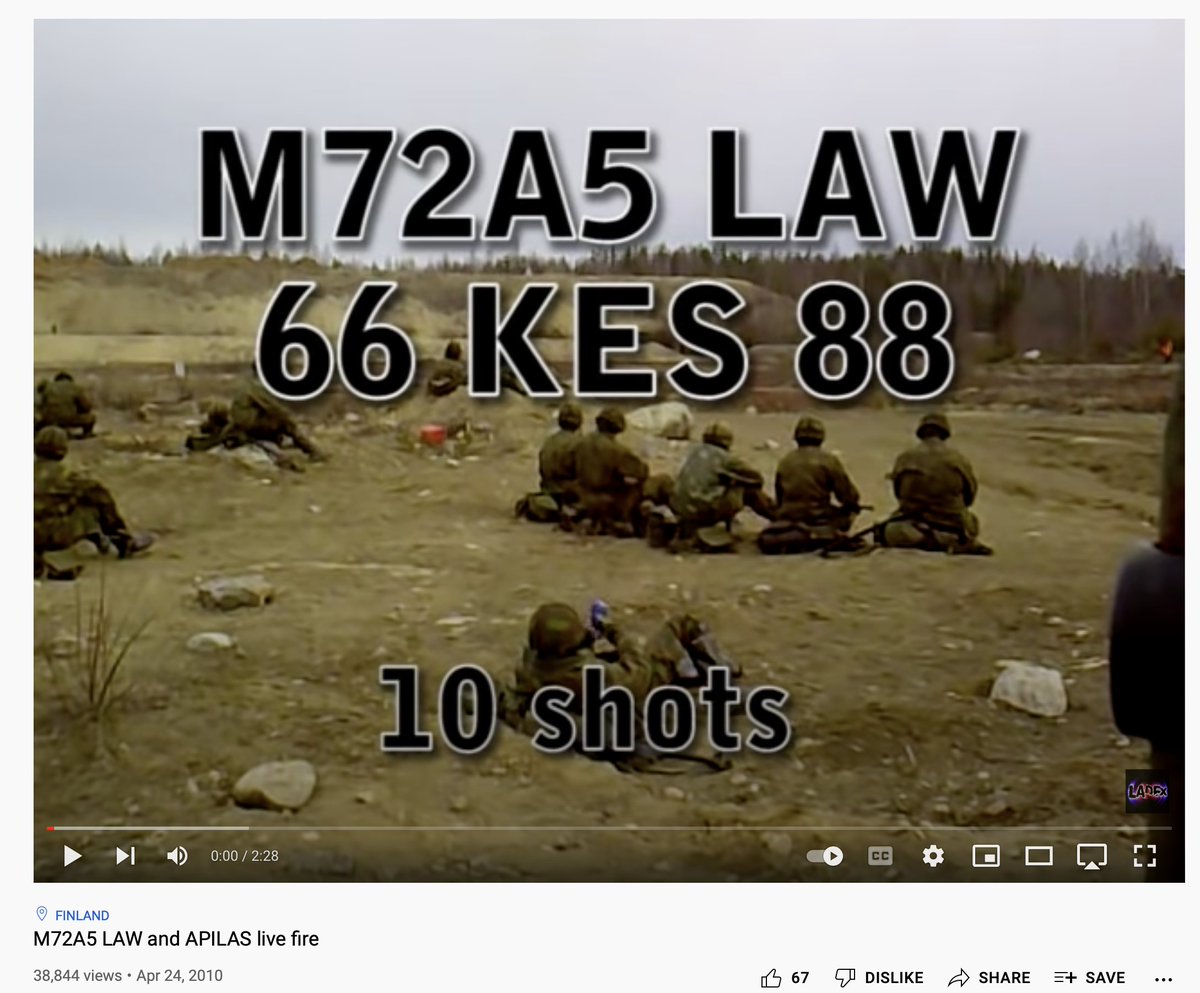
As @AugustGraham first pointed out, the specific audio waveforms of certain explosions from 1:51 of the “M72A5 LAW and AIPLAS live fire” YouTube video were a very close match to those in the “Polish saboteur” video
https://twitter.com/AugustGraham/status/1495031586483580933
He also noted that the sound of one of the explosions in the “Polish saboteur” video appears to cut out, just at the point in the original source video where the watching soldiers audibly react to the explosion
https://twitter.com/AugustGraham/status/1495069297911156740
Further analysis of the audio in both videos by @mistercw showed many more similarities, confirming that the “Polish saboteur” video had audio of explosions from another source pasted into it.
https://twitter.com/mistercw/status/1495156975071600645
If you wish to check this data for yourself and add your own comments on what you find you can view the metadata on metadata2go.com and download the original video here:
t.me/nm_dnr/6192
t.me/nm_dnr/6192
There's still things to discover in the metadata, for example it appears this part of the metadata shows which part of the file was pasted into the final video, and is consistent with the time of the explosion used in the first video.
https://twitter.com/EliotHiggins/status/1495350321387917318
In conclusion, in an attempt to create a casus belli for the Russian invasion separatists published false allegations, using a fake video, of “Polish saboteurs” attacking chemical storage to create a major chemical incident, claims that were then propagated in Russian media.
The confirmation this was an attempted false flag was established through the combined efforts of an informal community connected through social media, which currently seems to be one of the strongest counters against Russian disinformation around Ukraine.
This is in part thanks to the growth of an open source community around the conflict in Ukraine in 2014, catalysed by the downing of Malaysia Airlines Flight 17, and sustained thanks to Russia's ongoing involvement in the conflict in Eastern Ukraine.
In my mind it's the growth and development of these communities in different regions, or focused on different topics, that can create an effective and rapid response to disinformation.
For clarification:
https://twitter.com/xoryouyou/status/1495372375944310792
An example of the Russia media using this video in its coverage of Ukraine
https://twitter.com/thomasbratt/status/1495418042196631562?t=ukaWHW90BFvdCzPdVNRDqQ&s=19
More examination of the audio confirming the audio cuts off to hide the chatter of soldiers in the original audio source
https://twitter.com/mistercw/status/1495719973423132673?t=3uCTei5HT0zGt9KG2fEbvw&s=19
• • •
Missing some Tweet in this thread? You can try to
force a refresh














