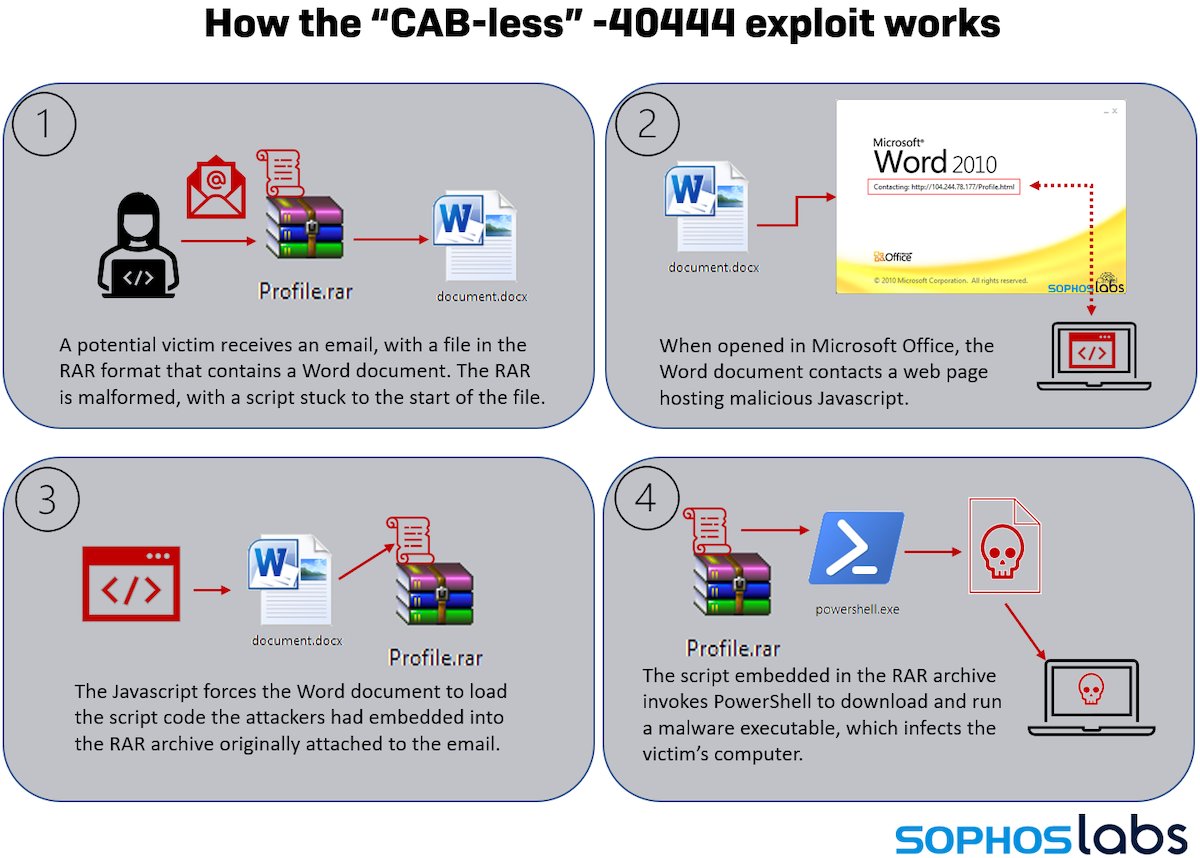
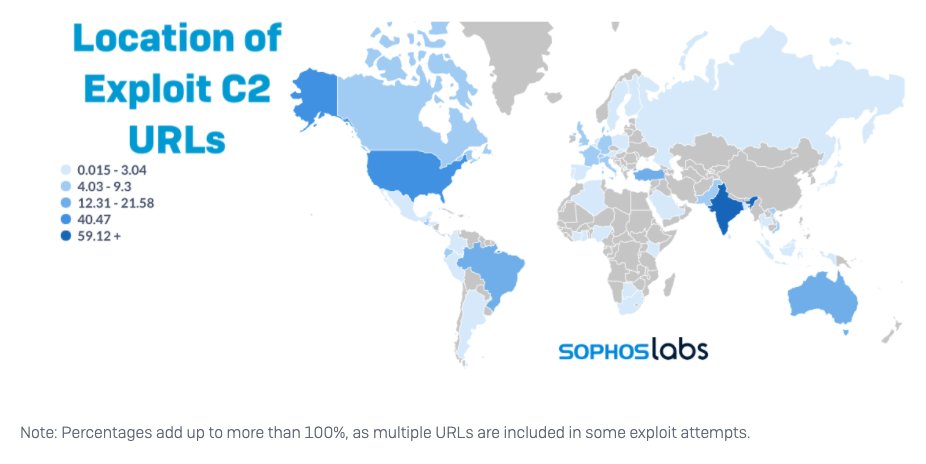
NEW 🧵on Conti...
We published some news this week about Conti. In brief, a #Conti affiliate infiltrated the network of a healthcare provider that a different #ransomware threat actor had already penetrated.
The technical debt in healthcare is dangerous.
1/23
We published some news this week about Conti. In brief, a #Conti affiliate infiltrated the network of a healthcare provider that a different #ransomware threat actor had already penetrated.
The technical debt in healthcare is dangerous.
1/23
But Conti, in particular, attracts a particularly aggressive group of affiliates. And we have another, previously untold, Conti-adjacent story about one of their ransomware affiliates.
It serves as a cautionary tale that not all attackers are necessarily after a ransom. 2/23
It serves as a cautionary tale that not all attackers are necessarily after a ransom. 2/23
This past January we were contacted by a customer in the Middle East to investigate a malware incident that began in mid-December, 2021. The target, in the financial services industry, discovered lateral movement and backdoors in their network the week before new year's day. 3/23
As this is a story told through logs, which are ordered in the reverse chronology, read the logs from the bottom to the top to get a chronological sense of what’s happening.
We’ve removed the dates so as not to reveal to the attacker who our customer is. 4/23
We’ve removed the dates so as not to reveal to the attacker who our customer is. 4/23
The initial point of access was a server running Windows Server 2008 R2 Service Pack 1. That machine was the source of several failed login attempts to a number of other servers, and 15 minutes, attackers had logged in to a 2nd machine, and four minutes later, a 3rd server. 5/23 

Control of the third server gave the attackers admin privileges. They abused a remote management utility called RemoteExec (named CI.exe) and, 18 minutes in to the attack, copied it to six other machines. 6/23 

The next minute, the attackers had copied batch scripts to three of the six compromised servers, and those scripts were running, performing a variety of tasks at high speed. They also installed a backdoor service onto one of the other compromised machines. 7/23 

By minute 26 of the attack, the intruders had downloaded and installed a second commercial remote access utility, called ScreenConnect, and set up temporary access to a specific, external IP address. 8/23 

Methodically over the following hour, attackers moved from compromised server to compromised server, downloading and executing a set of batch scripts. Some of the machines downloaded a payload from an IP address belonging to notorious ISP Green Floid. money.cnn.com/2017/10/25/med… 9/23 

And then…nothing happened for three days. The attackers made no attempt to reconnect to the network until almost 72 hours after the initial break-in. But then the gloves came off…and those servers started reporting detections of malware. 10/23 

Behavioral detections based on the malicious use of PowerShell; Multiple attempts to deploy Cobalt Strike beacons; Placement of malware executables on network shares. The @Sophos endpoint was blocking all of that. 11/23 

All day, the attackers tried and tried and tried again to deploy malware across a wide range of machines, and failed. For more than 15 hours, they repeatedly tried to push malicious executables onto devices or filelessly load them into memory.
They failed. 12/23
They failed. 12/23

After taking a three hour break – all that attempted crime had to be hard work – the attackers then resumed, and continued failing to infect machines, blocked by behavioral and memory detection of the payloads, most of which were Cobalt Strike. 13/23 

Finally the attackers’ gloves came off. They used PowerShell to try to disable Windows Defender. They also leveraged those administrator tools they had used earlier in the attack to bundle up internal documents and send them to Mega, a cloud storage provider. 14/23 

It took almost a full day for them to download the installers for Chrome and WinRAR, to bundle up the sensitive data into archive files, and then upload them to Mega. At the end, they cleaned up after themselves, deleting host logs and records. 15/23 



The attackers took a break for three more days, then came back. We detected them deploying a list of text files on an internal server in preparation for the final phase of the attack, the deployment of ransomware. 16/23 

We also detected (and blocked) more attempts to deploy both Cobalt Strike beacons, Metasploit Meterpreters, and BazarBackdoor malware onto various systems they controlled. Once again, they were prevented from doing so. 17/23 

Finally, at about 1:34am in the target’s time zone, the attackers started trying to deploy ransomware executables. They were prevented from encrypting dozens of servers and workstations, repeatedly, over the next eight hours. Emotet and BazarBackdoor were also blocked. 18/23 



Logs showed that, while the attackers were trying to deploy the ransomware, they used some of their other tools to log in to machines and see what was going on. They probably weren’t happy with what they found. 19/23 



The following day, they tried using every tool they could think of to try to disable Sophos. They used PsKill and PsExec and GMER. They tried using the Windows version of a tool called FixGo. They tried to use RemCom, “the open source psexec”
github.com/kavika13/RemCom 20/23
github.com/kavika13/RemCom 20/23

In the end, they were unsuccessful at encrypting the machines. After three days of trying, the threat actors decided to give up but they would salt the earth in their wake.
They just wiped every machine they could reach. 21/23
They just wiped every machine they could reach. 21/23
Perhaps they thought they could get away with just extorting the target, or perhaps the encryption was only a ruse, and they got what they were after in the exfiltrated data. 22/23
Thank you to @threatresearch for their contributions to this thread.
Check out our recent article "Conti and Karma actors attack healthcare provider at same time through ProxyShell exploits" from @thepacketrat ⬇️
news.sophos.com/en-us/2022/02/…
23/23
Check out our recent article "Conti and Karma actors attack healthcare provider at same time through ProxyShell exploits" from @thepacketrat ⬇️
news.sophos.com/en-us/2022/02/…
23/23
• • •
Missing some Tweet in this thread? You can try to
force a refresh