This is really interesting!
Maybe it is an #APT attack targeting #Ukriane:
Zip -> dovidka.chm -> WScript.exe ignit.vbs -> wscript.exe desktop.ini -> regasm.exe core.dll
Also it drops "Windows Prefetch.lNk" in Start-Up directory to make "desktop.ini" persistence.
(1/3)
Maybe it is an #APT attack targeting #Ukriane:
Zip -> dovidka.chm -> WScript.exe ignit.vbs -> wscript.exe desktop.ini -> regasm.exe core.dll
Also it drops "Windows Prefetch.lNk" in Start-Up directory to make "desktop.ini" persistence.
(1/3)

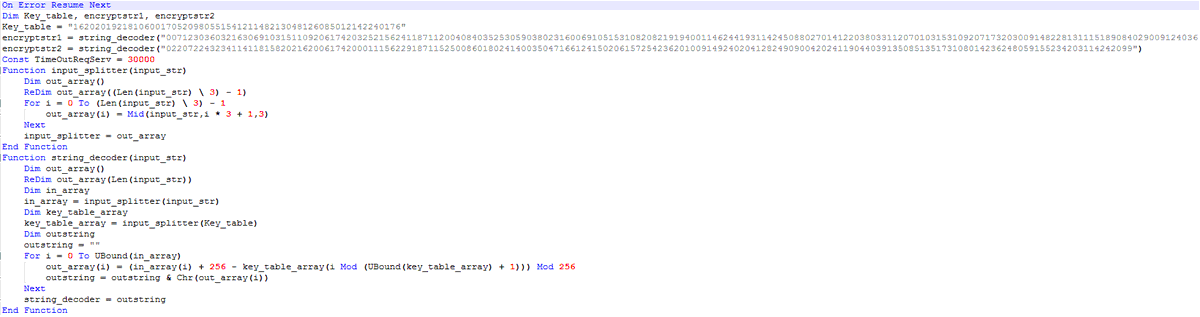
The dropped payload is a small .Net payload that is obfuscated using ConfuserEx. It has been compiled on Jan 31 2022.
IOCs:
e34d6387d3ab063b0d926ac1fca8c4c4
довідка.zip
2556a9e1d5e9874171f51620e5c5e09a
dovidka.chm (According to VT it is exploiting CVE-2019-0541)
(2/3)
IOCs:
e34d6387d3ab063b0d926ac1fca8c4c4
довідка.zip
2556a9e1d5e9874171f51620e5c5e09a
dovidka.chm (According to VT it is exploiting CVE-2019-0541)
(2/3)
ignit.vbs
bd65d0d59f6127b28f0af8a7f2619588
Desktop.ini
a9dcaf1c709f96bc125c8d1262bac4b6
Windows Prefetch.lNk
fb418bb5bd3e592651d0a4f9ae668962
core.dll
d2a795af12e937eb8a89d470a96f15a5
C2:
xbeta[.]online
185.175.158.27
(3/3)
bd65d0d59f6127b28f0af8a7f2619588
Desktop.ini
a9dcaf1c709f96bc125c8d1262bac4b6
Windows Prefetch.lNk
fb418bb5bd3e592651d0a4f9ae668962
core.dll
d2a795af12e937eb8a89d470a96f15a5
C2:
xbeta[.]online
185.175.158.27
(3/3)
• • •
Missing some Tweet in this thread? You can try to
force a refresh