1\ How to detect what command line spawned a process with no EDR/AV? 👀 #DFIR
If you have a memory sample, this is how you can figure out what cmd spawned the processes by using volshell and memory forensics.
STEP BY STEP GUIDE BELOW
👇 👇 👇 👇
#MemoryForensics

If you have a memory sample, this is how you can figure out what cmd spawned the processes by using volshell and memory forensics.
STEP BY STEP GUIDE BELOW
👇 👇 👇 👇
#MemoryForensics

2\ Each process in Windows is represented by an "EPROCESS" structure.
These EPROCESS blocks are joined in a doubly linked list structure. The flink (forward link) tells you the next process running and blink (backwards link) tells you the previous process.
These EPROCESS blocks are joined in a doubly linked list structure. The flink (forward link) tells you the next process running and blink (backwards link) tells you the previous process.

3\ When you see a list of processes on a live system, often times this is gathered by walking this doubly-linked structure of EPROCESS blocks.
Of course malware can unlink a process in this doubly linked list to hide from detection :P
Of course malware can unlink a process in this doubly linked list to hide from detection :P
4\ Now inside each of EPROCESS blocks is a pointer to a PEB (Process environment block). This is an object that stores information about a process like:
> What command started this process ;)
> The directory the process lives in
> handles, heaps etc
en.wikipedia.org/wiki/Process_E….
> What command started this process ;)
> The directory the process lives in
> handles, heaps etc
en.wikipedia.org/wiki/Process_E….
5\ Given this knowledge, this is how we'll figure out what spawned the process:
1. Examine the EPROCESS object for the process
2. Locate the PEB pointer
3. Locate “_RTL_USER_PROCESS_PARAMETERS” inside the PEB that stores the command line that the process was started with
1. Examine the EPROCESS object for the process
2. Locate the PEB pointer
3. Locate “_RTL_USER_PROCESS_PARAMETERS” inside the PEB that stores the command line that the process was started with
6\ STEP 1: Enter volshell.
To enter into volshell type in this command into Volatility:
vol.py -f <filename> —profile=<profile> volshell
To enter into volshell type in this command into Volatility:
vol.py -f <filename> —profile=<profile> volshell

7\ STEP 2: Enter into the context of the process - in this instance I will use cmd.exe
Type in ps() to see the running processes and to get the:
> PID
> Offset
Type in cc(pid=X) to enter into the context of the process
Type in ps() to see the running processes and to get the:
> PID
> Offset
Type in cc(pid=X) to enter into the context of the process

8\ STEP 3: Examine the EPROCESS structure of the process
Type in dt(“_EPROCESS”, <offset>)
Scroll until you see the decimal address of the PEB and convert that into hex address :) I have it highlighted in white at the bottom.
Type in dt(“_EPROCESS”, <offset>)
Scroll until you see the decimal address of the PEB and convert that into hex address :) I have it highlighted in white at the bottom.

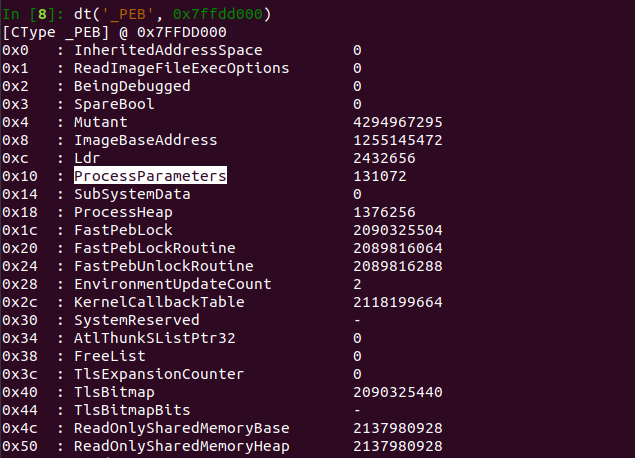
9\ STEP 4: Examine the PEB of the process
Type dt(“_PEB”, <PEB address>)
This address is what you converted into hex from the step above. This reveals the structures within the PEB.
Locate the “ProcessParameters” structure and convert the decimal address into HEX again.
Type dt(“_PEB”, <PEB address>)
This address is what you converted into hex from the step above. This reveals the structures within the PEB.
Locate the “ProcessParameters” structure and convert the decimal address into HEX again.

10\ STEP 5: Fetch the command that spawned the process
With the converted ProcessParameters hex address, type:
dt(“_RTL_USER_PROCESS_PARAMETERS”, <hexaddress>)
Voila, this will then show you the command line that spawned the process :)
With the converted ProcessParameters hex address, type:
dt(“_RTL_USER_PROCESS_PARAMETERS”, <hexaddress>)
Voila, this will then show you the command line that spawned the process :)

11\ The plugins pstree/pslist/psxview/psscan show you what processes were running/terminated.
You can use the technique I showed you above to see how those processes were spawned and the command lines that were used. :)
You can use the technique I showed you above to see how those processes were spawned and the command lines that were used. :)
12\ This is a link to volatility <3 <3
github.com/volatilityfoun…
github.com/volatilityfoun…
13\ I never know if you guys prefer these as tweets or as a blog..
• • •
Missing some Tweet in this thread? You can try to
force a refresh