I have been able to capture #Flubots deployment code⚠️
🔍This code is used on websites when a victim attempts to download the malicious APK
Here is what I found ⤵️
1/n
🔍This code is used on websites when a victim attempts to download the malicious APK
Here is what I found ⤵️
1/n

The code is a single php file with 330 lines...
However after removing hundreds of new lines and padding to 'hide' the code
We are left with this...
However after removing hundreds of new lines and padding to 'hide' the code
We are left with this...

My eyes are immediately drawn to the large data blob in the code 👀
Now the first task is to remove some of the obfuscation to understand what is happening here...
Now the first task is to remove some of the obfuscation to understand what is happening here...
Most of the items are simply base64 encoded
Decoding this we can understand the functions which are included 🔍
Decoding this we can understand the functions which are included 🔍

Following the trail we see the data blob getting decoded:
$var1 = (gzuncompress(base64_decode('eNrtXFuP2lgSfo+0/yEPK/WsZjVrmyZpK8oDNxsbcDc2Pth+GWG7MeALT..
$var1 = (gzuncompress(base64_decode('eNrtXFuP2lgSfo+0/yEPK/WsZjVrmyZpK8oDNxsbcDc2Pth+GWG7MeALT..
Performing this operation on the data blob gives us more code but sadly another large data blob is present.
So we repeat the steps to decode the data...
So we repeat the steps to decode the data...

We can see similar variables are being used in this code 🔍
We now move our attention to the data blob...
We now move our attention to the data blob...

The data is hilariously just base64 encoded...
Allowing us to use CyberChef to decode the code contained within
Allowing us to use CyberChef to decode the code contained within
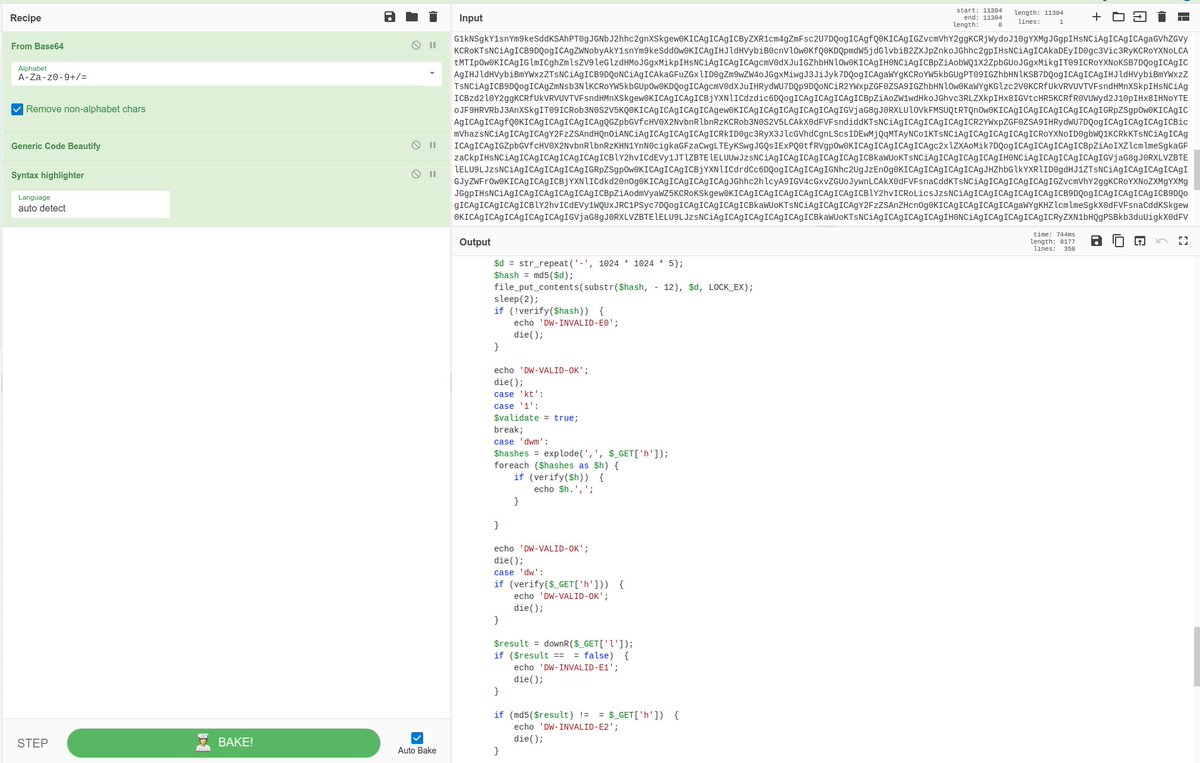
The PHP code is complex with a number of functions and logic statements
The IoCs extracted from the sample lead us down a rabbit hole...
The IoCs extracted from the sample lead us down a rabbit hole...
One domain mentioned is hxxp://smurfetta.ru
This domain sits on 91.240.118.223 🇷🇺
This domain sits on 91.240.118.223 🇷🇺
We can see a call to a URL on the host
🌐/click_api/v3?
The code then builds a http query
🏗️Which features a token set to a static value of 'hmf7fdqs9vfxp8s4rwqzxbfz6c43bwgb'
🌐/click_api/v3?
The code then builds a http query
🏗️Which features a token set to a static value of 'hmf7fdqs9vfxp8s4rwqzxbfz6c43bwgb'
We can see the code checking to make sure the accessing user has all the items set correctly otherwise the APK will not be downloaded 

On the same IP as the initial code was found there is a number of flu bot campaigns running
🌐185.215.113.96🇸🇨
🌐185.215.113.96🇸🇨

If you enjoyed this, follow me for more analysis of current campaigns
• • •
Missing some Tweet in this thread? You can try to
force a refresh