
#ThreatHunting: When investigating a potentially compromised Exchange server, one of the first steps I take is to search the MFT for .aspx files (with @velocidex's MFT Hunt, for example). Examine the results for suspicious file names or paths.
(1/3)
#CyberSecurity
(1/3)
#CyberSecurity
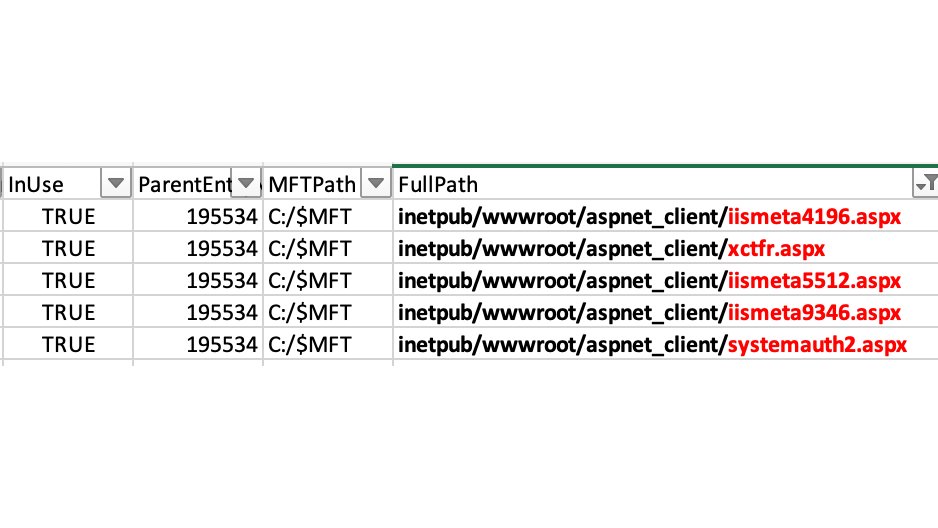
The picture above shows different webshells that I identified within the first few minutes of the investigation.
(2/3)
(2/3)
This procedure also has the advantage of finding "hidden" web shells. Attackers can create a virtualDirectory that points to webshells in non-standard directories. Check the @HuntressLabs blog post about which configuration files to examine:
huntress.com/blog/rapid-res…
(3/3)
huntress.com/blog/rapid-res…
(3/3)
• • •
Missing some Tweet in this thread? You can try to
force a refresh




