
How to get URL link on X (Twitter) App




 2/ The affected (and remotely accessible) server have had Confluence installed.
2/ The affected (and remotely accessible) server have had Confluence installed. 
 2/ With #Velociraptor, I ran the hunt Sysinternals.Autoruns, and with the CLI version of AutoRuns, the malware is found in the Startup folder.
2/ With #Velociraptor, I ran the hunt Sysinternals.Autoruns, and with the CLI version of AutoRuns, the malware is found in the Startup folder. 

 2/ Below is an excerpt from the content of config.txt; the configuration file passed as an argument to the tor service.
2/ Below is an excerpt from the content of config.txt; the configuration file passed as an argument to the tor service.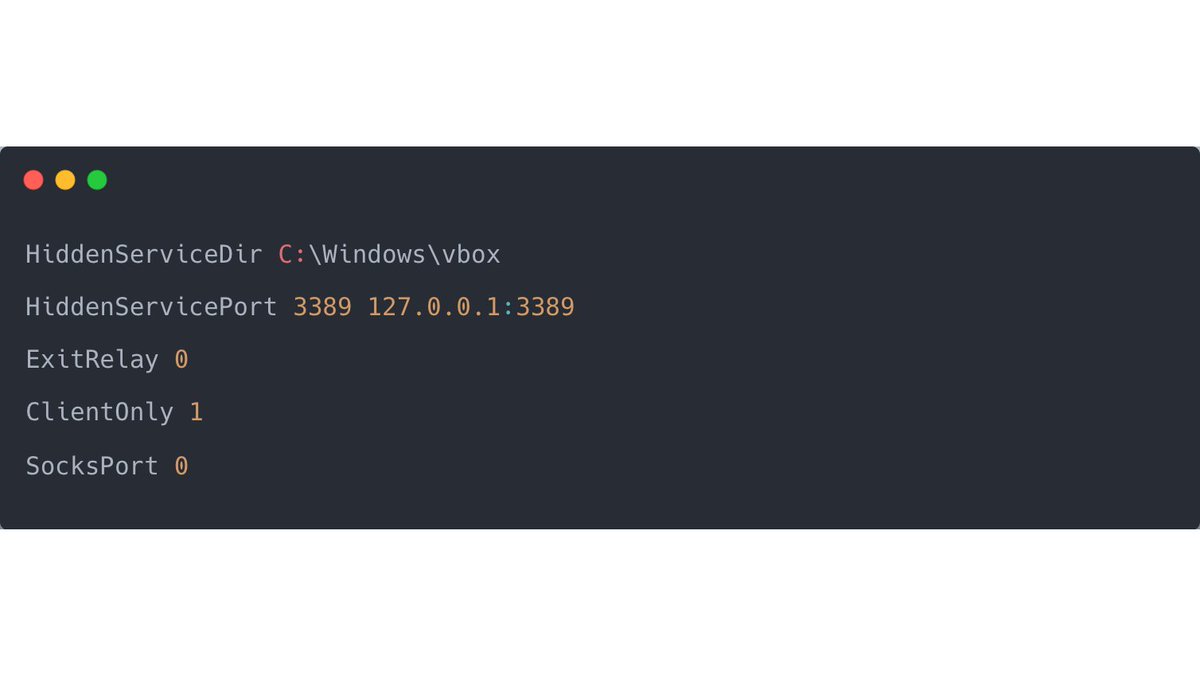

 2/ Why is this a bad idea?
2/ Why is this a bad idea?
https://twitter.com/BushidoToken/status/1522525471182893056
 2/ We talked about vulnerable drivers before:
2/ We talked about vulnerable drivers before:https://twitter.com/malmoeb/status/1551449425842786306



 This is the last thread in this AD hardening measure series, but there would still be so much to discuss 😅
This is the last thread in this AD hardening measure series, but there would still be so much to discuss 😅

 2/ There exists a ton of different techniques of how attackers can relaying credentials to another host in order to raise their privileges or get a shell on the target server.
2/ There exists a ton of different techniques of how attackers can relaying credentials to another host in order to raise their privileges or get a shell on the target server. 

 2/ A running print spooler service on domain controllers is still a relatively common finding in our AD assessments, even though an attack path via spooler service and unconstrained delegations have been known for years. [1]
2/ A running print spooler service on domain controllers is still a relatively common finding in our AD assessments, even though an attack path via spooler service and unconstrained delegations have been known for years. [1]

 2/ To raise the bar again, add critical accounts to the Protected Users Security Group.
2/ To raise the bar again, add critical accounts to the Protected Users Security Group. 
 2/ #PingCastle lists, among many other things, the privileges assigned to domain users via GPOs.
2/ #PingCastle lists, among many other things, the privileges assigned to domain users via GPOs. 

 2/ The following case is still worth mentioning:
2/ The following case is still worth mentioning: 

 2/ Strictly speaking not part of a guide about hardening AD, but I must stress once again the importance of logging executed PowerShell code on clients and servers:
2/ Strictly speaking not part of a guide about hardening AD, but I must stress once again the importance of logging executed PowerShell code on clients and servers:https://twitter.com/malmoeb/status/1608796598888452097
https://twitter.com/malmoeb/status/1627214815012716546

 2/ We talked about passwords in SYSVOL before:
2/ We talked about passwords in SYSVOL before:https://twitter.com/malmoeb/status/1522499535158796290


 2/ In our AD assessments or IR cases, we repeatedly see that service accounts are highly privileged, often also part of the domain administrators group.
2/ In our AD assessments or IR cases, we repeatedly see that service accounts are highly privileged, often also part of the domain administrators group.https://twitter.com/malmoeb/status/1553006183484727298




 2/ The customer disabled the login mask a long time ago on the public internet-facing IP address of the Cisco ASA, as depicted in the image below.
2/ The customer disabled the login mask a long time ago on the public internet-facing IP address of the Cisco ASA, as depicted in the image below. 


 2/ The screenshot above depicts the content of the config.json file, which is located in the installation directory of DWservice, and could be interesting for LEA purposes (the key could be linked to an account).
2/ The screenshot above depicts the content of the config.json file, which is located in the installation directory of DWservice, and could be interesting for LEA purposes (the key could be linked to an account).

 2/ In this case, a malicious .bat file gets executed when the user double clicks "View Document".
2/ In this case, a malicious .bat file gets executed when the user double clicks "View Document".