1\ #DefenceEvasion Technique: Maliciously Modifying Registry Timestamps 👿👀
This technique doesn't log events in the Security.evtx and is almost trivial to perform as a defence evasion technique...
Read my blog for technique + detection:
bit.ly/3r7jfuO
TL;DR 👇👇


This technique doesn't log events in the Security.evtx and is almost trivial to perform as a defence evasion technique...
Read my blog for technique + detection:
bit.ly/3r7jfuO
TL;DR 👇👇


2\ Why should you care?
During an IR, registry timestamps are important evidence items for timelining & triaging an incident. They answer questions like...
> What files did the TAs open?
> When was a security tool disabled?
> What folders were the TAs looking at?
> etc...
During an IR, registry timestamps are important evidence items for timelining & triaging an incident. They answer questions like...
> What files did the TAs open?
> When was a security tool disabled?
> What folders were the TAs looking at?
> etc...
3\ The native API "NtSetInformationKey" specifically allows a TA to overwrite a registry "Last Write" timestamp in an extremely trivial manner.
The param KEY_SET_INFORMATION_CLASS being passed the value KEY_WRITE_TIME_INFORMATION is what performs this.
undocumented.ntinternals.net/UserMode/Undoc…
The param KEY_SET_INFORMATION_CLASS being passed the value KEY_WRITE_TIME_INFORMATION is what performs this.
undocumented.ntinternals.net/UserMode/Undoc…

4\ When I was performing research into this, I found a PoC written by Joakim Schicht using this specific API to perform the timestomping action.
He also calls the API NtFlushKey to make the change immediately on disk.
github.com/jschicht/SetRe…
He also calls the API NtFlushKey to make the change immediately on disk.
github.com/jschicht/SetRe…
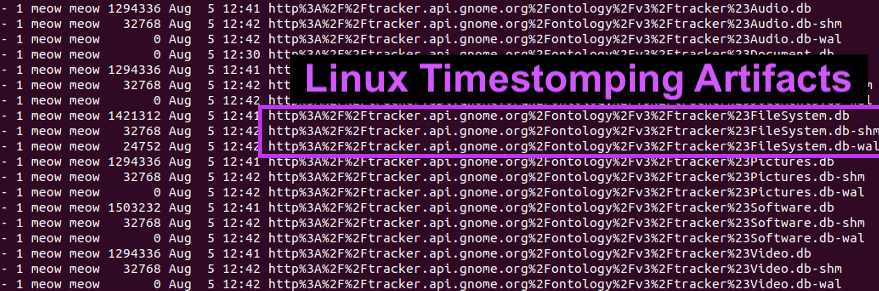
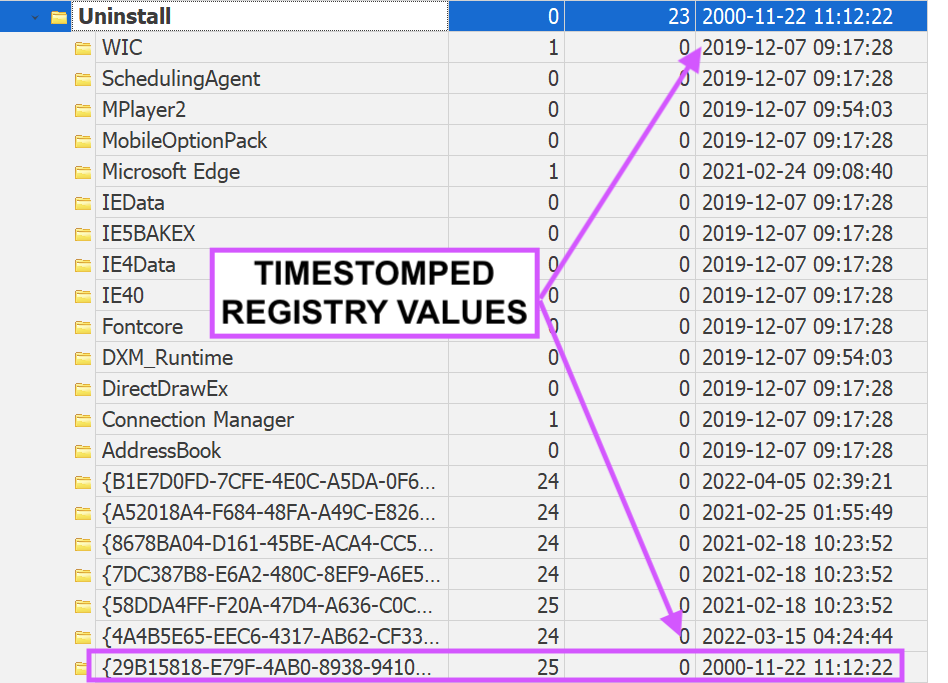
5\ Here is an example of this attack:
Pic 1: Pre-timestomped RUN key
Pic 2: Me running Joakim's tool
Pic 3: The timestomped registry key


Pic 1: Pre-timestomped RUN key
Pic 2: Me running Joakim's tool
Pic 3: The timestomped registry key



6\ Detection Method 1: Windows EVTX
Event IDs 4656. 4757. 4660, 4663 do NOT detect this.
Look at ID 4657 - this event wont generate because it's alerting on a change to a registry VALUE, not the registry TIMESTAMP. This means enabling reg auditing won't detect this technique.
Event IDs 4656. 4757. 4660, 4663 do NOT detect this.
Look at ID 4657 - this event wont generate because it's alerting on a change to a registry VALUE, not the registry TIMESTAMP. This means enabling reg auditing won't detect this technique.

7\ Detection Method 2: Reg Discrepancies
For nested keys, the topmost key reflects the timestamp of the most recent subkey entry time. Unless each timestamp is timestomped, you can see that there is a time discrepancy.
NOTE: This detection WON'T work for keys with no subkeys.
For nested keys, the topmost key reflects the timestamp of the most recent subkey entry time. Unless each timestamp is timestomped, you can see that there is a time discrepancy.
NOTE: This detection WON'T work for keys with no subkeys.

8\ Detection Method 3: EDR
Running through procmon, one entry stood out which is the high-fidelity detection for this technique. You can see the KeySetInformationClass param from the "NtSetInformationKey" being used to write to a timestamp.
This is NOT normal behaviour!!
Running through procmon, one entry stood out which is the high-fidelity detection for this technique. You can see the KeySetInformationClass param from the "NtSetInformationKey" being used to write to a timestamp.
This is NOT normal behaviour!!

9\ I would finally detect on the use of the following APIs in conjunction:
NtCreateKey
NtOpenKey
NtEnumerateKey
NtSetInformationKey
NtQueryKey
NtFlushKey
NtCreateKey
NtOpenKey
NtEnumerateKey
NtSetInformationKey
NtQueryKey
NtFlushKey
10\ Finally, just an observation of mine... IR analysts are taught to look for timestomping of files by comparing $standard_information vs $filename. But there isn't a straight forward method of finding registry timestomping as it isn't as simple as parsing out MFT timestamps..
• • •
Missing some Tweet in this thread? You can try to
force a refresh