
Visualizing #cybersecurity concepts can be a great way to learn more about specific tools, methodologies, and techniques! Here is a thread that shows 6 useful infographics on threat intelligence and related topics!🧵👇#infosec #threatintel
1⃣ - Practical Threat Intel
1⃣ - Practical Threat Intel

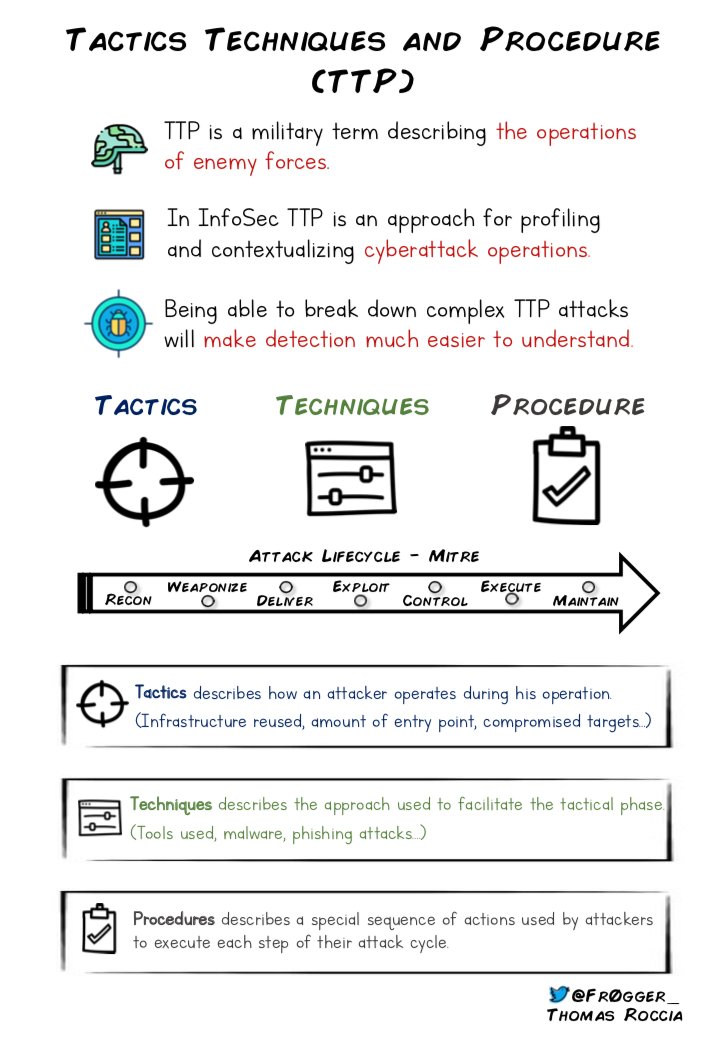
2⃣ - Tactics, Techniques and Procedures is an important concept to understand when you are working on threat intelligence to understand the capabilities of threat actors! 🤓 #Infosec #ttp 
3⃣ - Mitre ATT&CK Matrix is became one of the references to classify and categorize attackers' TTPs! ☠️ #cybersecurity 

3⃣ - Diamond Model of Intrusion is another interesting concept that can help profiling tactics of threat actors! 💻#infosec 

4⃣ - Anatomy of a YARA rule - Once you have gained more knowledge of threat intelligence concepts and methodologies, learning to use YARA rules can be very powerful for your threat hunting abilities!🛠️ #yararules #threathunting 

5⃣ - Anatomy of a SIGMA rule - Sigma is another great tool that will help you hunt your logs. While Yara is for file, Sigma is for logs. ⚒️ #sigmarule #infosec 

6⃣ - Log Parsing Cheatsheet -At some point, you'll have to get your hands dirty. Knowing the popular Linux commands for log parsing can be very helpful and timesaving during incident response! #DFIR #forensic 



That's it! If you like this kind of content, you can visit my page dedicated to them where I publish these infographics! You can follow me for more stuff like this! ❤❤️🔥👇#infosec #cybersecurity #threatintel
medium.com/malware-buddy/…
medium.com/malware-buddy/…
• • •
Missing some Tweet in this thread? You can try to
force a refresh





