AI Security x Threat Intel · Sr. Threat Researcher @Microsoft · Creator of #Unprotect & #NOVA · Malware Warlock · Python 🧡 · Prev @McAfee_Labs · Views mine 😈
2 subscribers
How to get URL link on X (Twitter) App


 When we talk about adversarial prompts, most people think of prompt injection or prompt jailbreaking.
When we talk about adversarial prompts, most people think of prompt injection or prompt jailbreaking. 
 1️⃣ Direct Prompt Injection
1️⃣ Direct Prompt Injection


 As always, when analyzing new data, check out the structures and formats, and spend time to understand what kind of data you're dealing with. THIS is crucial!🔍
As always, when analyzing new data, check out the structures and formats, and spend time to understand what kind of data you're dealing with. THIS is crucial!🔍






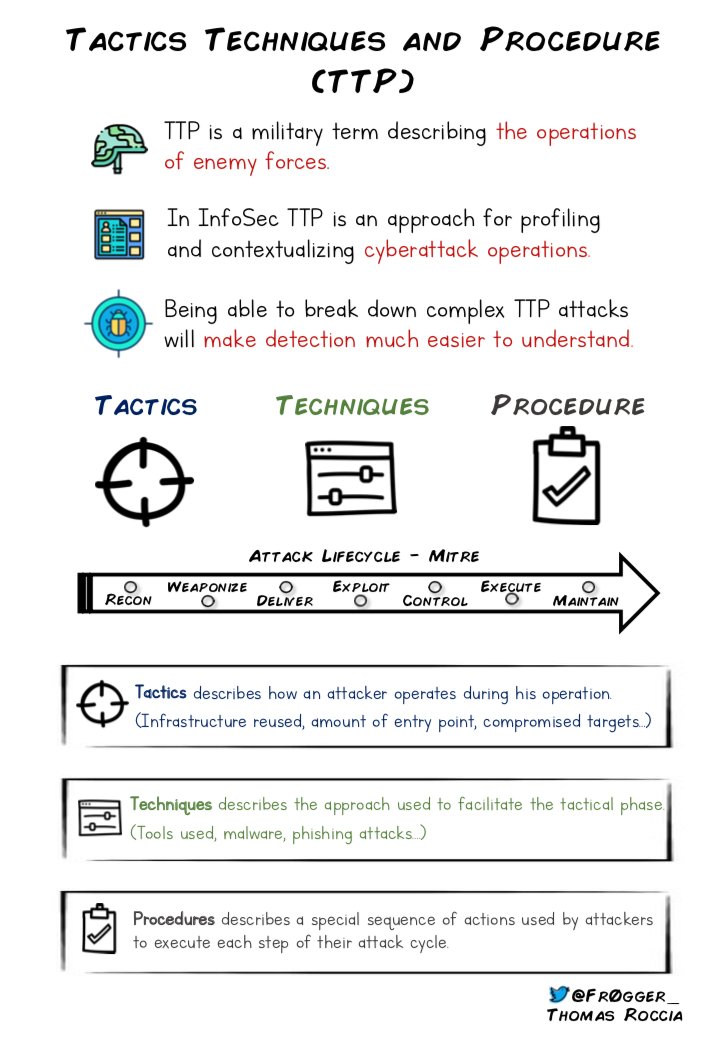
 2⃣ - Tactics, Techniques and Procedures is an important concept to understand when you are working on threat intelligence to understand the capabilities of threat actors! 🤓 #Infosec #ttp
2⃣ - Tactics, Techniques and Procedures is an important concept to understand when you are working on threat intelligence to understand the capabilities of threat actors! 🤓 #Infosec #ttp